The BS 7799 / ISO 17799 Standard
For a better approach to information security
White Paper
Jacquelin Bisson, CISSP
Information Security Analyst, Callio Technologies
René Saint-Germain
,
President, Callio Technologies
Executive Summary
When it comes to implementing codes of practice for information security management, the best point
of reference is BS 7799 / ISO 17799, an internationally recognized standard in this field that is widely
used for drafting security policies.
The BS 7799 / ISO 17799 standard is written and published in two parts:
1) ISO/IEC 17799 Part 1: Code of practice for information security management is a guide containing
advice and recommendations to ensure the security of a company’s information according to ten fields
of application.
2) BS 7799 Part 2: Information security management -- specifications with guidance for use provides
recommendations for establishing an effective Information Security Management System (ISMS). At
audit time, this document serves as the assessment guide for certification.
Several software programs are currently available on the market to help companies implement the BS
7799 / ISO 17799 standard and develop security policies. Callio Secura 17799 is one of these. It
brings together a sound methodology, questionnaires, an informational guide and all of the tools
needed to develop an information security management system and accelerate its implementation.

© Callio Technologies
BS7799 / ISO 17799 Solution
i
Company Profile
Callio Technologies was created in 2001
and specializes in the field of information
security. Its first product, Callio Secura
17799, is software that offers companies
the opportunity to comply with the BS 7799
/ ISO 17799 information security
management standard.
Callio Technologies’ areas of expertise are:
risk analysis; developing security codes of
practice and information security
management systems; drafting security
policies based on BS 7799 / ISO 17799;
security audits; contingency plans; and
training in computer risk management.
Our mission: enable companies to assess, manage
and reduce their computer risks. We provide software
and other tools that give you decision-making power
supported by complete risk analysis.

© Callio Technologies
BS7799 / ISO 17799 Solution
2
Information security has always been a
major challenge to most organizations.
Computer infections by the “I-Love-You”
virus, the 9-11 terrorist attacks and the
crippling electrical blackouts in the
northeastern United States in 2003 are
just a few well-known examples of the
need to come to terms with information-
related risks.
Unfortunately, organizations forget too
quickly that information security is more
than a simple matter of technology. In
reality, it should be part of an ongoing risk
management process, covering all of the
information that needs to be protected.
An array of laws now hold the officers of a corporation liable for protection of its
informational assets, under threat of penalty. It has become a must for administrators
to show due diligence in this regard, fostering greater concern for countering risks
with appropriate measures to reduce or eliminate them.
Introduction
3
© Callio Technologies
BS7799 / ISO 17799 Solution
What is information security?
“Information systems security is not a contradiction in terms... security without risk
management is.” (J. Bisson, 2003)
Information is an asset which, like other
important business assets, has value to an
organization and consequently needs to be
suitably protected. Information security
protects information from a wide range of
threats in order to ensure business continuity,
minimize business losses and maximize
return on investments and business
opportunities.
Information can exist in many forms. It can
be printed or written on paper, stored
electronically, transmitted by post or using
electronic means, shown on films, or spoken
in conversation. Whatever form the
information takes, whatever the means by
which it is shared or stored, it should always
be appropriately protected.
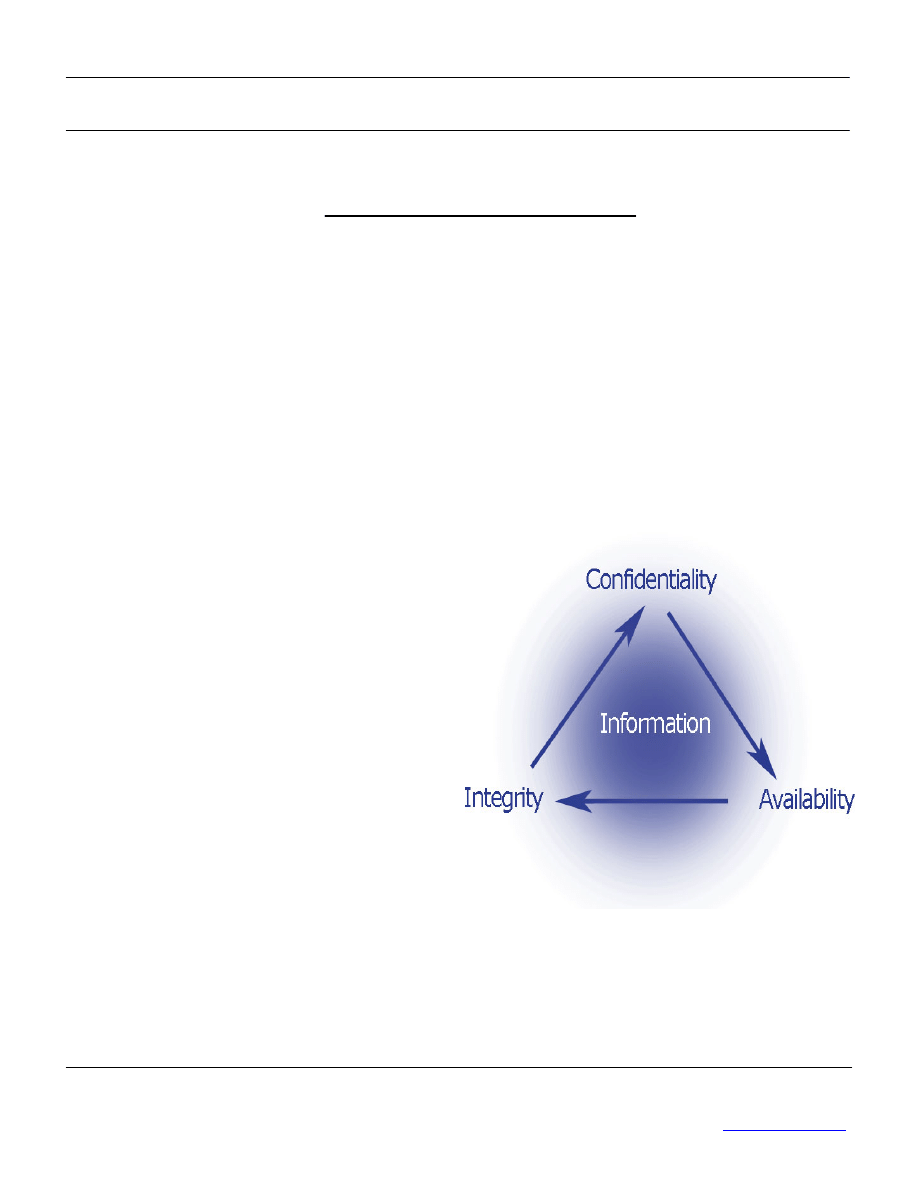
Information security consists of preserving
the following elements:
a) confidentiality: ensuring that information
can only be accessed by those with the
proper authorization;
b) integrity: safeguarding the accuracy and
completeness of information and the ways in
which it is processed;
c) availability: ensuring that authorized users
have access to information and associated
assets whenever required.
Information security is achieved by
implementing a suitable set of controls, which
could be policies, practices, procedures,
organizational structures and software
functions. These controls need to be
established in order to ensure that the
specific security objectives of the
organization are met.
Source: ISO/IEC 17799 Part 1: Code of
practice for information security
management
Source: ISO 17799
© Callio Technologies
BS7799 / ISO 17799 Solution
What is BS 7799 / ISO 17799?
The goal of BS 7799 / ISO 17799 is to “provide a common base for developing
organizational security standards and effective security management practice and to provide
confidence in inter-organizational dealings.”
The standard is published in two parts:
ISO/IEC 17799 Part 1: Code of practice for
information security management
BS 7799 Part 2: Information security
management -- specifications with guidance
for use
The international standard ISO/IEC 17799
was developed by the British Standards
Institution (BSI) as BS 7799. It was adopted
through a special “fast track procedure” by
the JTC 1 (Joint ISO/IEC Technical
Committee), concurrently with its approval by
the national member institutes of ISO and the
IEC.
ISO/IEC 17799 is presented in the form of
guidelines and recommendations that were
assembled following consultations with big
business. The 36 security objectives and 127
security controls contained in ISO/IEC 17799
are divided among ten domains. The
following is a brief overview of each of these
domains:
1. Security Policy - Provide guidelines and
management advice for improving
information security.
2. Organizational Security - Facilitate
information security management within the
organization.
ISO/IEC 17799 (Part 1)
3. Asset Classification and Control - Carry
out an inventory of assets and protect these
assets effectively.
4. Personnel Security - Minimize the risks of
human error, theft, fraud or the abusive use
of equipment.
5. Physical and Environmental Security -
Prevent the violation, deterioration or
disruption of industrial facilities and data.
6. Communications and Operations Management -
Ensure the adequate and reliable operation
of information processing devices.
7. Access Control - Control access to
information.
8. Systems Development and Maintenance -
Ensure that security is incorporated into
information systems.
9. Business Continuity Management -
Minimize the impact of business interruptions
and protect the company’s essential
processes from failure and major disasters.
10. Compliance - Avoid any breach of
criminal or civil law, of statutory or contractual
requirements, and of security requirements.
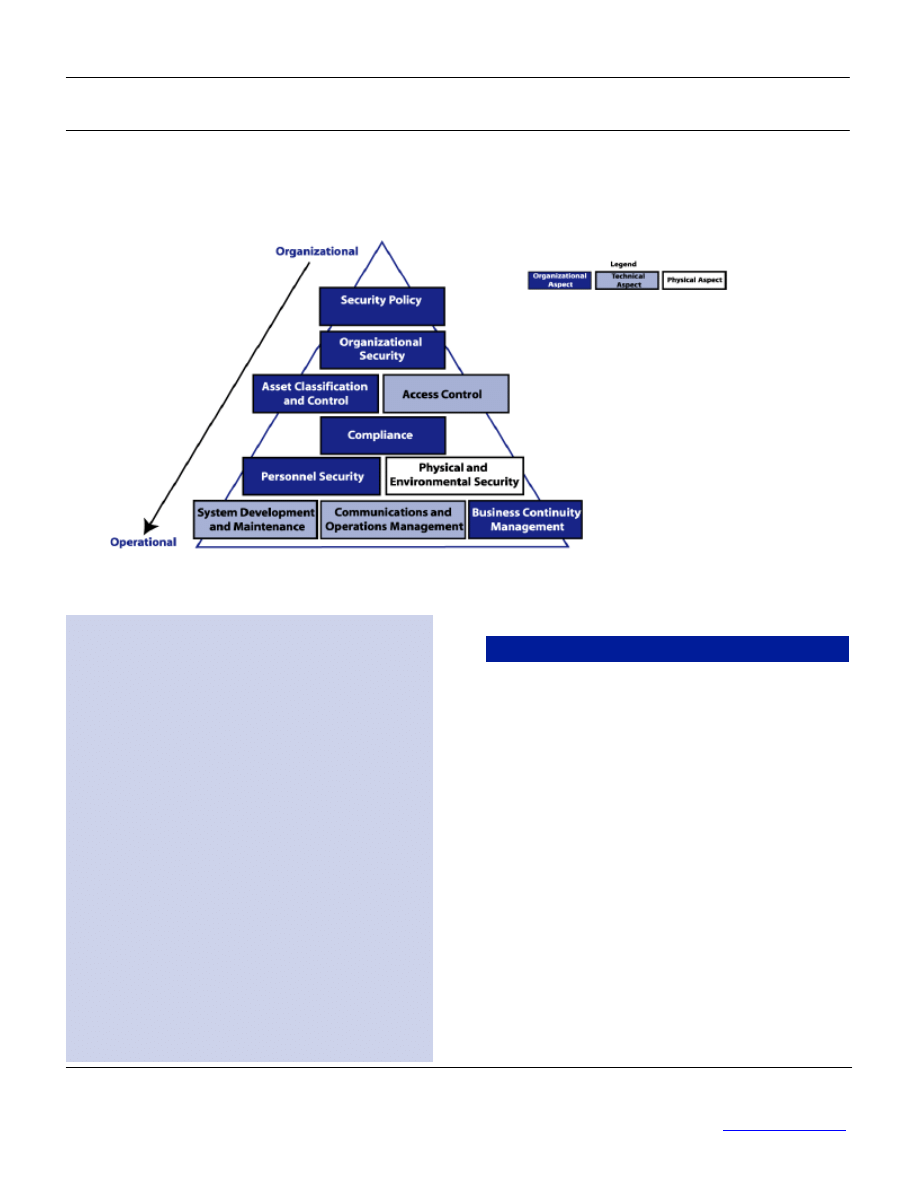
The following diagram suggests a structure for the ten domains of the standard. Each domain
deals with a separate topic built around administrative, technical and physical measures and
driven from the top down, in other words such that its impact is felt from the management level
all the way to the operational level.
5
© Callio Technologies
BS7799 / ISO 17799 Solution
About ISO and the IEC
The International Organization for
Standardization (ISO) and the International
Electrotechnical Organization (IEC)
constitute a specialized system for
standardization around the world. Through
technical committees, these two
organizations participate jointly in the
development and adoption of international
standards, as was the case for ISO/IEC
17799.
These technical committees, like the
ISO/IEC
Joint Technical Committee
(ISO/IEC JTC 1), submit proposed
standards to the many national
organizations for the purpose of a vote. In
order to be recognized internationally, a
standard must obtain the approval of at least
75% of national voting bodies.
BS7799 provides conditions for information
security management. Comprised of the ten
domains and 127 controls of the ISO 17799
standard, this reference applies to the
development, implementation and
maintenance stages of an information
security management system. Organizations
applying for certification are evaluated
according to this document.
An organization that bases its ISMS on the
provisions in BS 7799 can obtain certification
from an accredited body. The organization
thereby demonstrates to its partners that its
system both complies with the standard and
answers the need for security measures as
determined by its own requirements.
BS 7799-2 (Part 2)

© Callio Technologies
BS7799 / ISO 17799 Solution
It is important to understand that an
organization that obtains certification is
considered ISO 17799 compliant and BS7799-
2 certified.
What is an ISMS?
“To establish the organization’s information
security policy and objectives... and then
meet these objectives.”
An Information Security Management
System (ISMS) provides a systematic
approach to managing sensitive information
in order to protect it. It encompasses
employees, processes and information
systems.
Information security involves more than
simply installing a firewall or signing a
contract with a security firm. In this field it is
essential to integrate multiple initiatives
within a corporate strategy so that each
element provides an optimal level of
protection. This is where information security
management systems come into play - they
ensure that all efforts are coordinated in
order to acheive optimum security.
A management system must therefore
include an evaluation method, safeguards
and a documentation and revision process.
This is the underlying principle of the PDCA
(Plan-Do-Check-Act) model which strongly
resembles the ISO 9001 model for quality
management.
Plan
- Define the ISMS scope and the organization’s
security policies
- Identify and assess risks
- Select control objectives and controls that will help
manage these risks
- Prepare the statement of applicability
Do
- Formulate and implement a risk mitigation plan
- Implement the previously selected controls in order
to meet the control objectives.
Check
- Perform monitoring procedures
- Conduct periodic reviews to verify the effectiveness
of the ISMS
- Review the levels of acceptable and residual risk
- Periodically conduct internal ISMS audits
Act
- Implement identified ISMS improvements
- Take appropriate corrective and preventive action
- Maintain communications with all stakeholders
- Validate improvements
BS 7799-2 is already widely used in many
countries as a reference document for
information security management
certification. These countries include
England, Australia, Norway, Brazil and
Japan.
© Callio Technologies
BS7799 / ISO 17799 Solution
For over a hundred years, the British Standards Institution (BSI) has carried out studies for the
purpose of establishing effective, high-quality industry standards. BS 7799 was developed at the
beginning of the 1990s in response to industry, government and business requests for the
creation of a common information security structure. In 1995, the BS7799 standard was officially
adopted.
Four years went by before the publication in May 1999 of a second major version of the BS 7799
standard, incorporating numerous improvements. It was during this period that the International
Organization for Standardization (ISO) began to take an interest in the work published by the
British institute.
In December 2000, ISO took over the first part of BS 7799, re-baptising it ISO 17799. In
September 2002, a revision of the second part of the BS7799 standard was carried out in order
to make it consistent with other management standards such as ISO 9001:2000 and ISO
14001:1996 as well as with the principles of the Organization for Economic Cooperation and
Development (OECD).
Currently, consultations are taking place at the international level to keep BS 7799 / ISO 17799
at the leading edge of the latest developments.
History of the BS7799 / ISO 17799 standard
Compliance, Certification and Accreditation
To avoid confusion, here is a brief definition of these three terms in the context of an Information
Security Management System (ISMS):
Compliance is a self-assessment carried out by an organization in order to verify whether a
system that has been implemented complies with a standard.
Certification (also called registration) is conferred by an accredited certification body when an
organization successfully completes an independent audit, thus certifying that the management
system meets the requirements of a specific standard, for example BS7799-2. A company may
comply with ISO 17799, but certification is only possible with BS7799.
Accreditation consists of the means by which an authorized organization (the accreditation
body) officially recognizes the authority of a certification body to evaluate, certify and register an
organization’s ISMS with regard to published standards.
© Callio Technologies
BS7799 / ISO 17799 Solution
BS 7799 / ISO 17799 meets the needs of organizations and companies of all types, both
private and public.
For any organization that stores confidential information on internal or external systems,
depends on such systems to run its operations, or indeed wishes to demonstrate its
information security by conforming to a known standard, BS 7799 / ISO 17799 would be of very
great interest. The following chart illustrates the many possible uses of the standard:
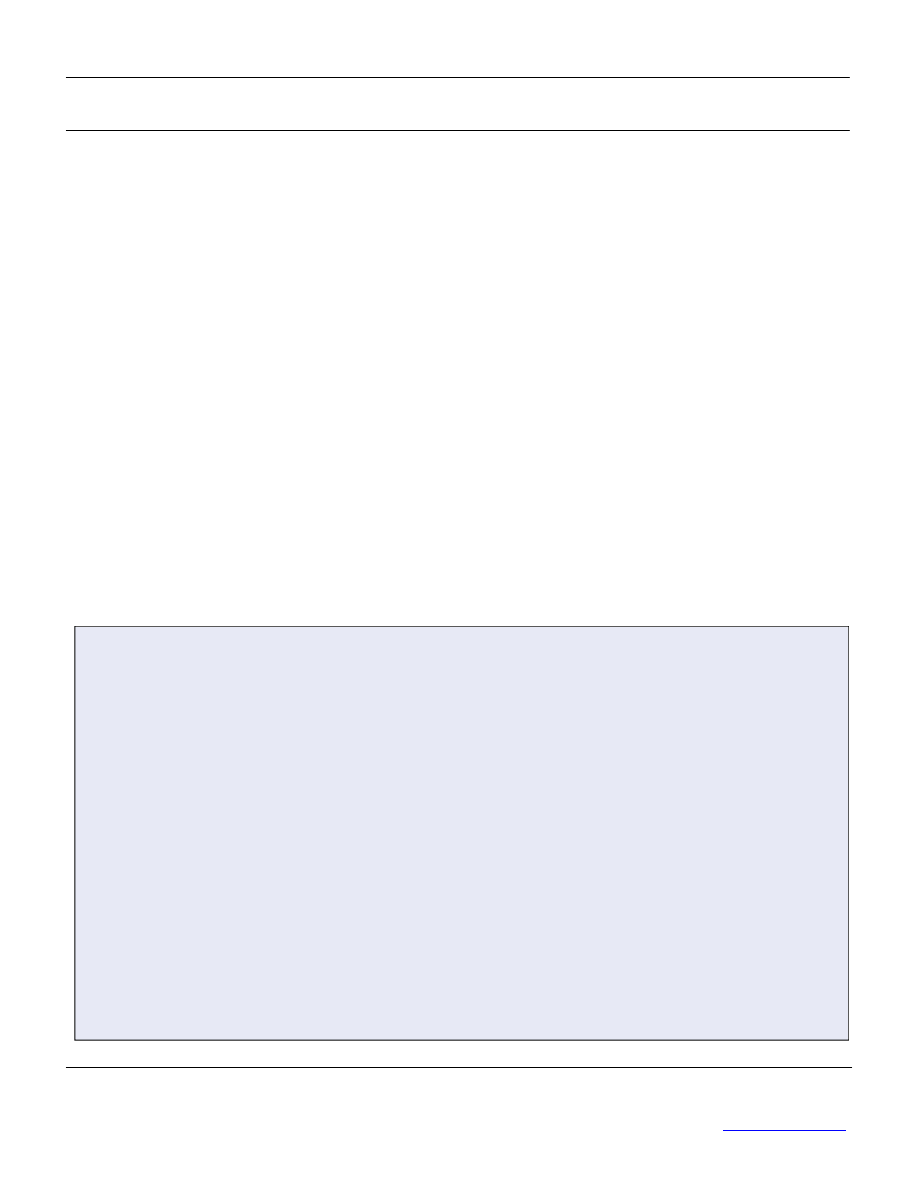
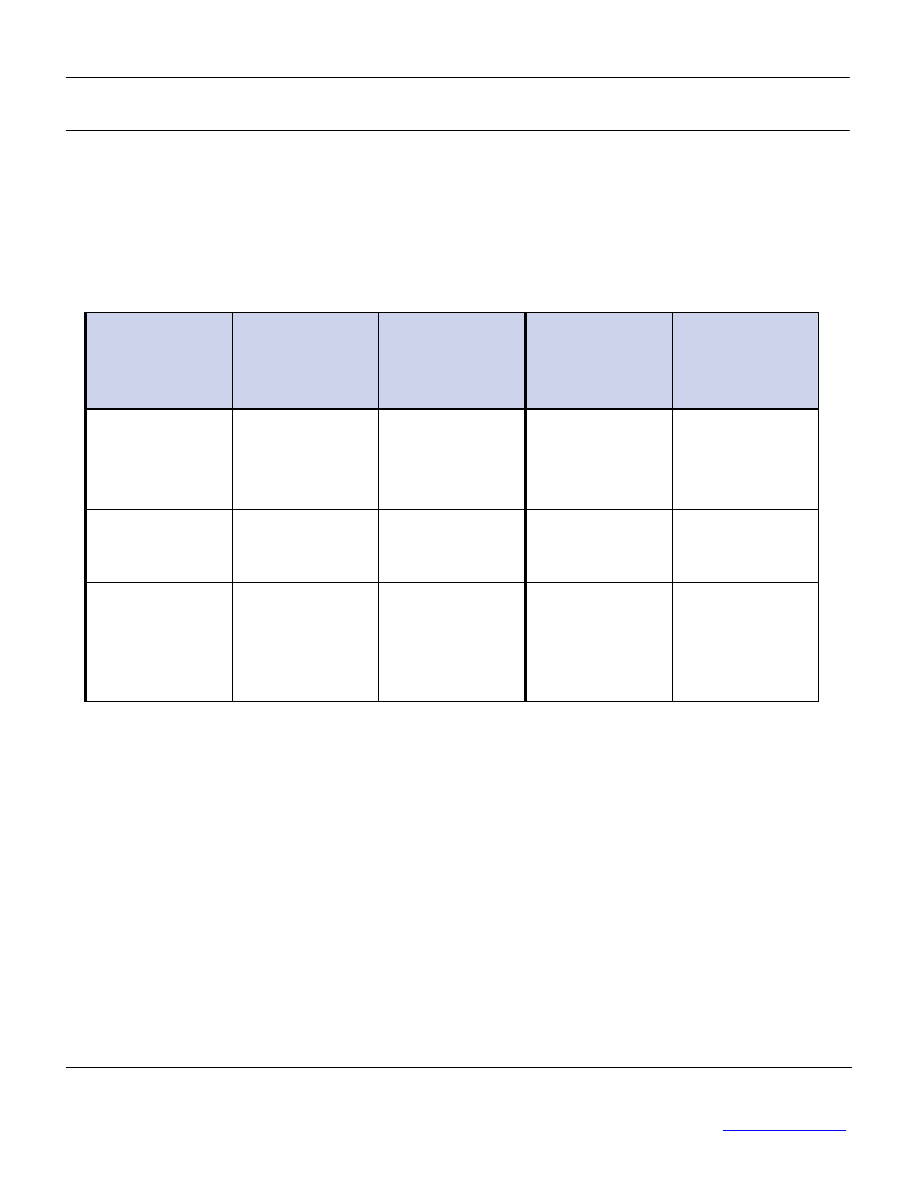
Who is ISO 17799 for?
Of course, the greater the risk
to an organization, the more
likely the organization is to
pay greater attention to the
security of its data.
Such is the case in
governmental, financial and
health-related fields, as
shown in the accompanying
figure:
Type of company
Size
Primary objective
Use of the standard
Small enterprise or
organization
Less than 200
employees
Raise management’s
awareness regarding
information security
ISO 17799 contains the
security topics that should
be dealt with as a
foundation for management.
Medium enterprise
(centralized or
decentralized)
Less than
5000
employees
Create a compatible
corporate security
culture
The standard contains the
practices required to put
together an information
security policy.
Large enterprise
More than
5000
employees
Obtain security
certification at the end
of the process
Use BS 7799-2 to create an
internal security reference
document.
9
© Callio Technologies
BS7799 / ISO 17799 Solution
Obviously, complying with the ISO 17799
standard or obtaining BS 7799-2 certification
does not in itself prove that an organization
is 100% secure. The truth is, barring a
cessation of all activity, there is no such
thing as complete security. Nevertheless,
adopting this international standard confers
certain advantages that any manager should
take into consideration, including:
At the organizational level
Commitment: certification serves as a
guarantee of the effectiveness of the effort
put into rendering the organization secure at
all levels, and demonstrates the due
diligence of its administrators.
At the legal level
Compliance: certification demonstrates to
competent authorities that the organization
observes all applicable laws and
regulations. In this matter, the standard
complements other existing standards and
legislation (for example HIPAA, the Privacy
Act of 1974, the Computer Security Act of
1987, the National Infrastructure Act of
1996, the Gramm-Leach-Bliley Act of 1999,
and the Government Information Security
Reform Act of 2001).
At the operating level
Risk management: leads to a better know-
ledge of information systems, their
weaknesses and how to protect them.
Equally, it ensures a more dependable
availability of both hardware and data.
At the commercial level
Credibility and confidence: partners,
shareholders and customers are reassured
when they see the importance afforded by
Benefits of the BS7799 / ISO 17799 standard
the organization to protecting information.
Certification can help set a company apart
from its competitors and in the marketplace.
Already, international invitations to tender are
starting to require ISO 17799 compliance.
At the financial level
Reduced costs related to security breaches,
and possible reduction in insurance
premiums.
At the human level
Improves employee awareness of security
issues and their responsibilities within the
organization.
10
© Callio Technologies
BS7799 / ISO 17799 Solution
The popularity of BS 7799-2 / ISO 17799 is due in part to its flexibility and its complementarity
with other information and IT security standards.
Complementarity of BS7799 / ISO 17799
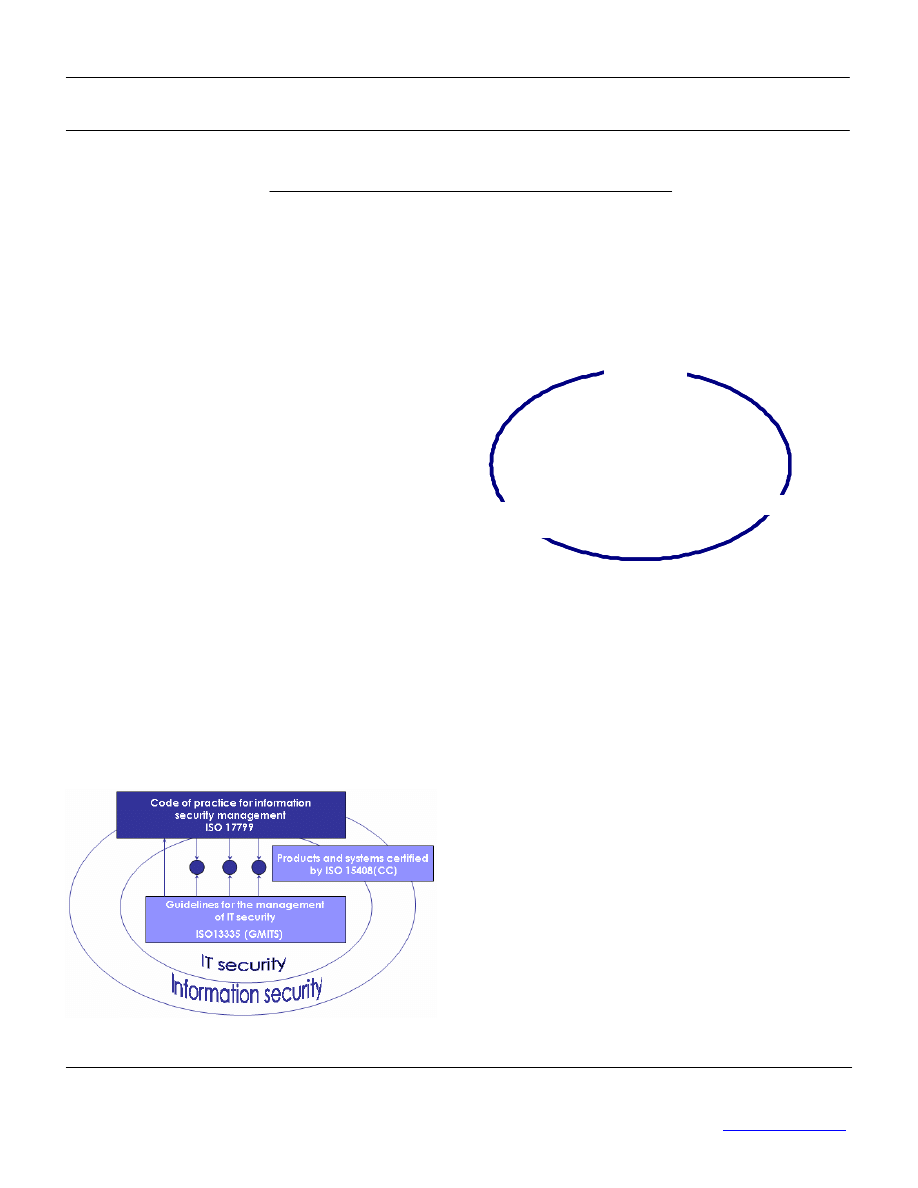
While ISO 17799 sets out the best
practices for managing information security
and creating security policies, ISO 13335,
also called GMITS - Guidelines for the
Management of IT Security - is its big
brother. This standard deals more with the
technological aspects of information, and
brings value-added content to risk
assessment. The protective measures
proposed in the fourth of ISO 13335’s five
guides (Part 4: Selection of safeguards)
could be compared to the controls offered
in ISO 17799.
There is also a strong complementarity
between ISO 17799 and ISO 15408. The
latter, better known under the name
Common Criteria, certifies the levels of
defense conferred by the security
measures in information systems. It
therefore covers technical aspects,
whereas ISO 17799 focuses more on the
organizational and administrative aspects
of security.
A relationship also exists between ISO 17799
and numbers 18044, 17944, 18028 and
14516 of the International Organization for
Standardization, as summarized in the
following figure:
As of the new 2002 revision, BS7799-2 is
harmonized with the standards for other well-
known management systems, such as ISO
9001:2000 and ISO 14001:1996.
Indeed, numerous companies are aware of or
have implemented a quality management
system (QMS) using ISO 9001, or an
environment management system (EMS)
using ISO 14001. BS 7799-2 now follows the
same structure and has much the same
requirements for developing an Information
Security Management System (ISMS).
ISO 13335
(GMITS)
ISO 15408
ISO 18044: Incident management
ISO 17944: Financial systems
ISO 18028: Communications management
ISO 14516: E-commerce security
ISO 17799
ISO 13335
(GMITS)
ISO 15408
ISO 18044: Incident management
ISO 17944: Financial systems
ISO 18028: Communications management
ISO 14516: E-commerce security
ISO 17799
11
© Callio Technologies
BS7799 / ISO 17799 Solution
Many governments around the world are preparing or have adopted regulations prescribing how
companies should manage and control information security. The aim is simple: compel
management and boards of directors to be responsible for information security, and encourage
them to display the same “due diligence” they devote to protecting their assets.
Such regulations include the Sarbanes-Oxley Act of 2002 (SOX), the Gramm-Leach-Bliley Act
(GLBA) and the Health Insurance Portability and Accountability Act of 1996 (HIPAA):
The good news is that an organization that complies with any one of these regulations already
possesses a concrete and practical example of an information security management system.
For example, HIPAA tackles the same subjects as the ISO 17799 standard while placing the
emphasis on the protection of private information.
Similarly, the PDCA (Plan-Do-Check-Act) model in BS 7799-2 compares nicely with the four steps
in GLBA:
1. Identify and assess the risks to customers’ information;
2. Develop a plan containing policies and procedures to manage and control those risks;
3. Implement and test the plan;
4. Adjust the plan on a continuing basis.
Finally, compliance with ISO 17799 and BS7799-2 can include the definition of policies and
procedures for the security of a company’s sensitive information, as touched on in SOX.
Complementarity with existing legislation
RECENT
LEGISLATION
WHO IS
AFFECTED?
WHAT DO THE
SECURITY
PROVISIONS
COVER?
WHAT ARE
THE
PENALTIES?
WHEN IS IT IN
EFFECT?
Sarbanes-Oxley
Act of 2002
All public
companies
subject to US
security laws
Internal controls
and financial
disclosures
Criminal and
civil penalties
Current law
Gramm-Leach-
Bliley Act of
1999
Financial
institutions
Security of
customer
records
Criminal and
civil penalties
Current law
Health
Insurance
Portability and
Accountability
Act (HIPAA)
Health plans,
health care
clearinghouses,
and health care
providers
Personal health
information in
electronic form
Civil fines and
criminal
penalties
Final security
rule takes effect
in April 2005
12
© Callio Technologies
BS7799 / ISO 17799 Solution
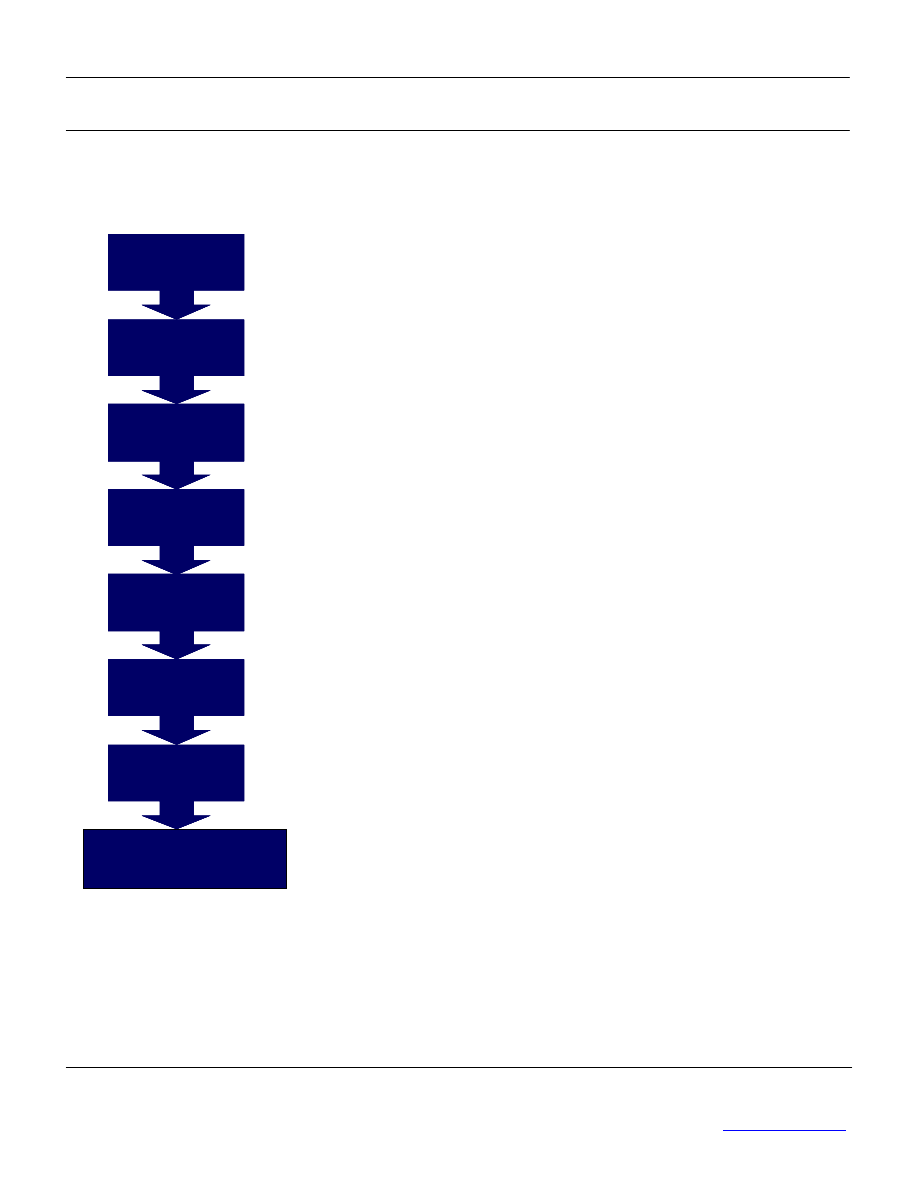
Implementing an ISMS
The following table describes each of the eight steps involved in implementing an ISMS:
Learn how to validate your management framework and what must be done before
you bring in an external auditor for BS 7799-2 certification.
Control and Continual
Improvement
Project Initiation
Risk Treatment
Audit Preparation
Audit
Risk Assessment
Training and
Awareness
Definition of the
ISMS
Ensure the commitment of senior management. Select and
train members of the initial project team.
Identify the scope and limits of the information security management
framework. This step is crucial to the success of the project.
Diagnose the level of compliance with ISO 17799. Compile an
inventory of the assets to be protected and assess them. Identify
and evaluate threats and vulnerabilities.
Find out how selecting and implementing the right controls can
enable an organization to reduce risk to an acceptable level.
Employees may be the weakest link in your organization's information
security. Learn how to set up an information security awareness program.
Learn more about the steps performed by external auditors and find out about
BS 7799-2 accredited certification bodies.
Learn how to improve the effectiveness of your ISMS in accordance with the
management model recognized by ISO.
Learn how to validate your management framework and what must be done before
you bring in an external auditor for BS 7799-2 certification.
Control and Continual
Improvement
Project Initiation
Risk Treatment
Audit Preparation
Audit
Risk Assessment
Training and
Awareness
Definition of the
ISMS
Ensure the commitment of senior management. Select and
train members of the initial project team.
Identify the scope and limits of the information security management
framework. This step is crucial to the success of the project.
Diagnose the level of compliance with ISO 17799. Compile an
inventory of the assets to be protected and assess them. Identify
and evaluate threats and vulnerabilities.
Find out how selecting and implementing the right controls can
enable an organization to reduce risk to an acceptable level.
Employees may be the weakest link in your organization's information
security. Learn how to set up an information security awareness program.
Learn more about the steps performed by external auditors and find out about
BS 7799-2 accredited certification bodies.
Control and Continual
Improvement
Project Initiation
Risk Treatment
Audit Preparation
Audit
Risk Assessment
Training and
Awareness
Definition of the
ISMS
Ensure the commitment of senior management. Select and
train members of the initial project team.
Identify the scope and limits of the information security management
framework. This step is crucial to the success of the project.
Diagnose the level of compliance with ISO 17799. Compile an
inventory of the assets to be protected and assess them. Identify
and evaluate threats and vulnerabilities.
Find out how selecting and implementing the right controls can
enable an organization to reduce risk to an acceptable level.
Employees may be the weakest link in your organization's information
security. Learn how to set up an information security awareness program.
Learn more about the steps performed by external auditors and find out about
BS 7799-2 accredited certification bodies.
Project Initiation
Risk Treatment
Audit Preparation
Audit
Risk Assessment
Training and
Awareness
Definition of the
ISMS
Ensure the commitment of senior management. Select and
train members of the initial project team.
Identify the scope and limits of the information security management
framework. This step is crucial to the success of the project.
Diagnose the level of compliance with ISO 17799. Compile an
inventory of the assets to be protected and assess them. Identify
and evaluate threats and vulnerabilities.
Find out how selecting and implementing the right controls can
enable an organization to reduce risk to an acceptable level.
Employees may be the weakest link in your organization's information
security. Learn how to set up an information security awareness program.
Learn more about the steps performed by external auditors and find out about
BS 7799-2 accredited certification bodies.
Learn how to improve the effectiveness of your ISMS in accordance with the
management model recognized by ISO.
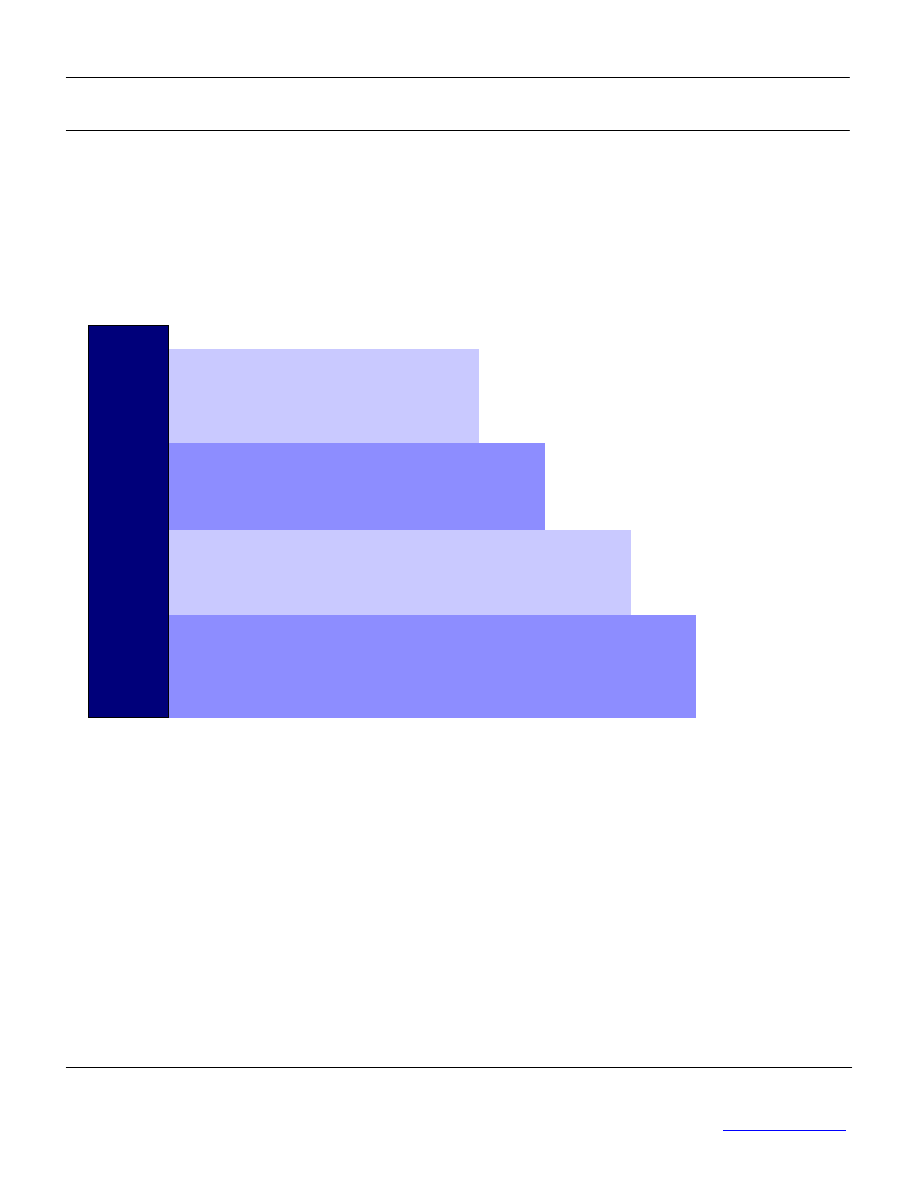
13
© Callio Technologies
BS7799 / ISO 17799 Solution
Documenting an ISMS is an important requirement during implementation and has two major
dimensions:
1) description of the organization’s strategy, objectives and risk assessment along with the
measures taken to mitigate risks;
2) control and followup once the ISMS is in operation.
At least four levels of documentation exist, as shown in the following figure:
Obstacles
Certain obstacles may be encountered when implementing an ISMS, namely:
- Fear, resistance to change
- Risk that changes made in one area necessitate subsequent adjustments in other areas
- Increased costs
- Insufficient knowledge of the approach used
- Seemingly insurmountable tasks
To help overcome these obstacles, certain success factors should be taken into consideration.
Documenting an ISMS
Describes how tasks and specific
activities are done
Policy, scope, risk assessment,
statement of applicability
Describes processes – who, what,
when, where
Provides objective evidence of compliance
with ISMS requirements
Level 1
Level 2
Level 3
Level 4
Security manual
Procedures
Work instructions,
checklists, forms, etc.
Records
Describes how tasks and specific
activities are done
Policy, scope, risk assessment,
statement of applicability
Describes processes – who, what,
when, where
Provides objective evidence of compliance
with ISMS requirements
Level 1
Level 2
Level 3
Level 4
Security manual
Procedures
Work instructions,
checklists, forms, etc.
Records
14
© Callio Technologies
BS7799 / ISO 17799 Solution
Success Factors
Experience has shown that the following factors are often crucial to ensuring the successful
implementation of information security management within an organization:
a) a security policy and security objectives and activities that reflect the company’s goals
b) an implementation approach to security management that is consistent with company
culture
c) visible support and commitment from management
d) a good understanding of security requirements, risk assessment and risk management
e) effective communication of security issues to all managers and employees
f) the distribution of guidelines regarding the information security policy and standards to all
employees and suppliers
g) appropriate training and education
h) a comprehensive and balanced system of measurement that is used to evaluate the
effectiveness of information security management and provide feedback and suggestions for
improvement
In summary: BS7799 / ISO 17799
What it is:
A structured and internationally
recognized guide with recommenda-
tions devoted to information security
A concise process for evaluating,
implementing, maintaining and
managing information security
The fruit of efforts exerted by a
consortium of companies to meet the
needs of industry
A balanced process between physical,
technical and procedural security, and
personnel security
What it isn’t:
A technical standard
A product-oriented or technological
standard
An equipment evaluation methodology such as
the Common Criteria (CC/ISO 15408).
However, it is complementary to such
standards and can make use of the evaluation
assurance levels (EAL) found in the Common
Criteria.
ISO 17799 isn’t a system that leads to a
security certification (for the moment, only BS
7799-2 and its national derivatives provide a
certification process).
ISO 17799 doesn’t specify any obligations
regarding the risk assessment method. It is
sufficient to choose whichever one best suits
the company’s needs.

© Callio Technologies
BS7799 / ISO 17799 Solution
A range of information security products and services are currently available on the market. Many
are based on physical safeguards (locks, gates, fences, extinguishers, guards, etc.) and technical
controls (firewalls, biometrics, encryption, etc.). When it comes to adopting administrative
safeguards, however, often companies forget how important these are.
But information security isn’t complete without the development and publication of security policies
and procedures, or employee awareness and training programs, to name only those. Information
security is really an ongoing risk management process and therefore requires tools that meet
these needs.
Beyond any doubt, ISO 17799 offers what companies need in order to better manage information
security. The best way to implement this standard is to ease the process using multiuser software
that will collect the information required and that contains the principal tools that will be needed
along the way. Start with a simple and efficient risk assessment tool that generates
recommendations based on the ISO 17799 code of practice for each of the informational contexts
identified. Add to that a complete methodology, compliance questionnaires, a security policy
generator, an integrated document manager, examples, templates and information guides
regarding the implementation and audit of ISO 17799 controls, and managers will quickly
understand that such a tool can save the company much time and money. This software exists:
it is a Web application called Callio Secura 17799, created by Callio Technologies Incorporated. A
demo version of Callio Secura 17799 can be downloaded at the following address:
www.callio.com
.
Of course, another approach is to implement the standard with the aid of a consulting firm--one
that uses such software.
Available software tools and resources
Methodology, method and standard
A methodology is a rigorous and standardized approach to information security analysis that
uses various tools such as specialized software and questionnaires.
A methodology therefore uses methods, that is to say, means to effectively achieve the desired
result. The latter is usually formulated in a standard.
A standard can be defined as a reference document that is based on a consensus of large
industrial or economic interests and established on a voluntary basis.
It is therefore obvious that the method will be the tool used to meet the requirements of a standard.

© Callio Technologies
BS7799 / ISO 17799 Solution
The software solution
One of the main advantages of BS 7799 / ISO 17799
has to do with public confidence. Just as ISO 9000
represents a guarantee of quality, this standard is a
mark of confidence in a company’s overall security.
Here are some of the advantages of implementing the
BS 7799 / ISO 17799 standard with Callio Secura 17799:
- Reduce the time and cost of implementing the
BS 7799 / ISO 17799 standard
- Centralize management of policies and procedures
- Standardize the BS 7799 / ISO 17799
implementation process
- Ensure the efficiency of implemented procedures
- Facilitate updates and revisions of documentation

17
© Callio Technologies
BS7799 / ISO 17799 Solution
Now more than ever, it is essential to align information security with the corporate mission.
The confidentiality, integrity and availability of information are crucial factors in conserving a
competitive edge, cash flow, legal compliance and a good business image.
Seeking certification is also a demonstration that business executives and upper management
are showing due diligence in protecting corporate assets. Development of an information
security policy based on ISO 17799 is thus at the very core of information security
management.
BS 7799 / ISO 17799 is especially pertinent in this context. Simply by learning the
requirements of the standard, companies will improve their understanding of information
security management.
One of the best ways to implement a complete and effective information security management
system is to purchase a software tool such as the Web application Callio Secura 17799 and to
use this tool in conjonction with professional or internal services. Callio Secura 17799 offers a
wealth of documentation and four principle modules: risk assessment, risk treatment, policy
generation and document management. Powerful yet user-friendly, Callio Secura 17799
enables users to comply with BS7799 / ISO 17799.
Conclusion
Over 80 000 firms around the world are BS 7799 / ISO 17799 compliant, including:
- Fujitsu Limited
- KPMG
- Marconi Secure Systems
- Sony Bank
- Toshiba IS Corporate
What about you? Implement the highest standards of information risk
management.
18
© Callio Technologies
BS7799 / ISO 17799 Solution
Web Sites
Official Website of the British Standards Institution
Presentation of the BS7799-2 methodology
Information on the BS7799 certification process
Website dealing with the BS7799 / ISO 17799 standard
Listing of BS7799 audit services
www.bs7799-iso17799-consultant.com
Listing of firms and independent consultants that offer services
www.bs7799-iso17799-directory.net
Listing of useful Websites and tools related to BS7799 / ISO 17799
Listing of international BS7799 / ISO 17799 events
Website of ISO 17799 news, updated regularly
www.bs7799-iso17799-software.com
International Electrotechnical Commission
www.information-security-awareness.org
Practical information on drafting employee awareness plans
Official site of the International Organization for Standardization
www.training-bs7799-iso17799.com
Listing of BS7799 / ISO 17799 training centres
Appendix A. References
19
© Callio Technologies
BS7799 / ISO 17799 Solution
References
British Standards Institution. BS 7799-2:2002: Information security management sys
tems - specification with guidance for use. London: 2002
British Standards Institution. PD 3001:2002: Preparing for BS 7799-2 Certification.
London. 2002.
British Standards Institution. PD 3002:2002: Guide to BS 7799 Risk Assessment.
London: 2002.
British Standards Institution. PD 3003:2002: Are you ready for a BS 7799 Part 2 Audit.
London: 2002.
British Standards Institution. PD 3004:2002: Guide to the implementation and auditing
of BS 7799 controls. London. 2002.
British Standards Institution. PD 3005:2002: Guide on the selection of BS 7799 Part 2
controls. London. 2002.
Calder, Alan and Steve Watkins. IT Governance, Data Security & BS 7799/ISO 17799
A Manager's Guide to Effective Information Security. London: Kogan Page, 2003.
International Organization for Standardization/International Electrotechnical
Commission. International Standard ISO/IEC 17799: Information technology -
Code of practice for information security management. Geneva: ISO, 2000.
International Organization for Standardization/International Electrotechnical
Commission. International Standard ISO/IEC TR 13335-1:1996 Guidelines for
the management of IT security - Part 1: Concepts and models for IT Security.
Geneva: ISO,1996.
International Organization for Standardization/International Electrotechnical
Commission. International Standard ISO/IEC TR 13335-2:1997 Guidelines for
the management of IT security - Part 2: Managing and planning IT Security.
Geneva: ISO, 1997.
International Organization for Standardization/International Electrotechnical
Commission. International Standard ISO/IEC TR 13335-3:1998 Guidelines for
the management of IT security - Part 3: Techniques for the management of IT
security. Geneva: ISO, 1998.
International Organization for Standardization/International Electrotechnical
Commission. International Standard ISO/IEC TR 13335-4:2000 Guidelines for the
management of IT security - Part 4: Selection of safeguards. Geneva: ISO, 2000.
International Organization for Standardization/International Electrotechnical
Commission. International Standard ISO/IEC TR 13335-5:2001 Guidelines for the
management of IT security - Part 5: Management guidance on network security.
Geneva: ISO, 2001.
Ramakrishnan, Prasanna, CISSP. "Information Security Management Systems." The
CISSP and SSCP Open Study Guides Website. 2003. CISSP and SSCP. 5 Jan.
2004
Callio Technologies
740, Galt Street West, Suite 10
Sherbrooke, (Quebec)
Canada, J1H 1Z3
Telephone: (819) 820-8222
Toll-free: 1-866-211-8222
Fax: (819) 820-9518
Information: info@callio.com
Human Resources: rh@callio.com
Webmaster: webmestre@callio.com
Wyszukiwarka
Podobne podstrony:
!BSI, wyk ad 4
BSI id 93515 Nieznany (2)
BSI, rozp2 MSWiA ePUAP
BSI test, PJWSTK, 0sem, BSI
BSI kolokwium wszystkie pytania
Madsen rozczarowany i zaskoczony?cyzją BSI
BSI,KRI 11 projekt
bsi egzam, BSI egzamin pytania 2008, Mniej wiecej do 40 pytania, to pytania jakie zebralem od roznyc
bsi-kolokwia, BSI-kolokwium, 1
bsi-sciaga-egz, BSI sciaga v2, Zagadnienia testu zaliczaj cego ć wiczenia z przedmiotu
!BSI, wyk ad 1
BSI ISO 27000
BSI, Semestr 8, Bezpieczeństwo systemów komputerowych
więcej podobnych podstron