
www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
Help you pass any it exams
www.ciscoexams.org
The IOS Firewall Set Questions & Answers:
1-Question:Define the term "DMZ" as it pertains to network security, and name three different
common network devices that are typically found there.
Answer: It's easy to think of your network as the "inside", and everything else as "outside".
However, we've got a third area when it comes to firewalls - the DMZ.
From an IT standpoint, the DMZ is the part of our network that is exposed to outside networks.
It's
common to find the following devices in a DMZ:
•
FTP server
•
Email server
•
E-commerce server
•
DNS servers
•
Web servers
2-Question: Identify the true statements.
A. Stateless packet filtering considers the TCP connection state. B.
Stateful packet filtering considers the TCP connection state.
C. Neither stateless nor stateful packet filtering monitor the TCP connection state.
D. Both stateless and stateful packet filtering monitor the TCP connection state, and keep a state
table containing that information.
Answer: (B.) Stateful packet filtering does monitor the connection state, and that's particularly
important when it comes to preventing TCP attacks. A stateful firewall will not only monitor the
state of the TCP connection, but also the sequence numbers. Stateful firewalls accomplish this by
keeping a session table, or state table.
3-Question:Does the Cisco IOS Firewall feature set act as a stateful or stateless packet filter?
Answer:The Cisco IOS Firewall is a stateful filter.
4-Question: Which of the following are considered parts of the IOS Firewall feature set? A.

www.640-553.com Help you pass CCNA SECURITY EXAMS
IOS Firewall
B. Intrusion Prevention System
C. RADIUS
D. Authentication Proxy
E. Password Encryption

www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
Answer:(A, B, D.) There are three major components to the IOS Firewall feature set - the IOS
Firewall, the Intrusion Prevention System (IPS), and the Authentication Proxy.
5-Question:Identify the true statements regarding the Authentication Proxy. A.
It's part of the IOS Firewall Feature Set.
B. It allows creation of per-user security profiles, rather than more general profiles.
C. It allows creation of general security profiles, but not per-user profiles. D.
Profiles can be stored locally, but not remotely.
E. Profiles can be stored on a RADIUS server.
F. Profiles can be stored on a TACACS+ server.
Answer: (A, B, E, F. T he Authentication Proxy allows us to create security profiles that will be applied
on a per-user basis, rather than a per-subnet or per-address basis. These profiles can be kept
on either of the following:
•
RADIUS server
•
TACACS+ server
Upon successful authentication, that particular user's security policy is downloaded from the
RADIUS or TACACS+ server and applied by the IOS Firewall router.
6-Question:Configuring ACLs is an important part of working with the IOS Firewall. What
wildcard masks are replaced in ACLs by the words host and any?
Answer: We have the option of using the word host to represent a wildcard mask of 0.0.0.0.
Consider a configuration where only packets from IP source 10.1.1.1 should be allowed and all other
packets denied. The following ACLs both do that.
R3#conf t
R3(config)#access-list 6 permit 10.1.1.1 0.0.0.0
R3(config)#conf t
R3(config)#access-list 7 permit host 10.1.1.1
The keyword any can be used to represent a wildcard mask of 255.255.255.255. Both of the
following lines permit all traffic.
R3(config)#access-list 15 permit any
R3(config)#access-list 15 permit 0.0.0.0 255.255.255.255
There's no "right" or "wrong" decision to make when you're configuring ACLs in the real world. For
your exam, though, I'd be very familiar with the proper use of host and any.

www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
7-Question:What does the dollar sign in the following ACL line indicate?
R1(config)#$ 150 deny ip 172.50.50.0 0.0.0.255 172.50.100.0 0.0.0.255
Answer: The dollar sign simply indicates that part of the command you're entering or viewing can't
be shown because the entry is so long. It does not mean the command is illegal.
8-Question:Basically, how does an IOS Firewall prevent a TCP SYN attack?
Answer: The IOS Firewall can use any or all of the following values to detect when a TCP SYN
attack is underway
Overall total of incomplete TCP sessions
Number of incomplete TCP sessions in a certain amount of time
Number of incomplete TCP sessions on a per-host basis
When any of these thresholds are reached, either of the following actions can be taken:
Block all incoming SYN packets for a certain period of time
Transmit a RST to both parties in the oldest incomplete session
9-Question:What does the term "punch a hole in the firewall" refer to? (Logically, that is, not
physically.)
Answer: That term simply refers to configuring the firewall to open a port that was previously
closed. Don't forget to close it when you no longer need it to be open!
10-Question:What exactly does the router-traffic option in the following configuration do?
R4(config)#ip inspect name PASSCCNASECURITY tcp router-traffic
R4(config)#ip inspect name PASSCCNASECURITY udp router-traffic
R4(config)#ip inspect name PASSCCNASECURITY icmp router-traffic
Answer: If you're going to inspect traffic that is actually generated on the router, you need to include the
router-traffic option at the end of that particular ip inspect statement
Questions On NTP, SSH, Telnet, And More
11-Question: We'll start with a question you learned the answer to in your CCNA studies. When you
have an enable secret and an enable password set, which takes precedence over the other?
A. The enable secret takes precedence.
B. The enable password takes precedence.
C. You cannot set both an enable secret and an enable password.
D. You can set them both, but since they must be set to the same value, there is no question of
precedence.

www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
Answer: A. The enable secret always takes precedence over the enable password
12-Question: What device and stratum level are found at the top of the NTP hierarchy? A.
Atomic clocks, stratum 1
B. Atomic clocks, stratum 0
C. NTP Masters, stratum 1
D. NTP Masters, stratum 0
E. NTP Primary, stratum 0
F. NTP Primary, stratum 1
Answer: B. Atomic clocks are at the top of the NTP hierarchy, and that top level is Stratum 0. Cisco
routers cannot get their time directly from a Stratum 0 device.
13-Question: What port does NTP use?
Answer: NTP uses UDP port 123. Remember that when you're configuring your ACLs!
14-Question: What are the options for NTP authentication? A.
MD5
B. Bellman-Ford
C. clear text
D. CHAP
E. PAP
Answer: A. As IOS Help illustrates, the only option here is MD5. You still have to specify that
option, though.
R1(config)#ntp authentication-key 1 ?
md5 MD5
authentication
15-Question: What command resulted in the following output?
R2#
Clock is synchronized, stratum 10, reference is 172.12.23.3
nominal freq is 250.0000 Hz, actual freq is 250.0000 Hz, precision
is 2**19
reference time is CBB9CEC8.17FBD1B8 (15:05:44.093 UTC Wed Apr 23
2008)

www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
clock offset is -0.6214 msec, root delay is 37.20 msec
root dispersion is 5.04 msec, peer dispersion is 0.53 msec
Answer: That command output is the result of the show ntp status command
16-Question: What command will limit the overall number of NTP peers and clients that the local
router can form an association with?
Answer: You can limit the overall number of NTP peers and clients with the ntp max-associations
command.
R3(config)#ntp max-associations ?
<0-4294967295> Number of associations
17-Question: What authentication option is available for Telnet that is not available with SSH?
Answer: You can use a line password for Telnet, but not for SSH. For SSH, you'll need to use AAA
or a locally configured database
18-Question: What command resulted in the following output?
R1(config)#
The name for the keys will be: HQ.HQ.com
Choose the size of the key modulus in the range of 360 to 2048 for
your
General Purpose Keys. Choosing a key modulus greater than 512 may
take a few minutes.
How many bits in the modulus [512]: 1024
% Generating 1024 bit RSA keys, keys will be non-exportable...[OK]
Answer: That output is the result of the crypto key generate rsa command.
19-Question: Name the two options for TCP Intercept mode and describe the major operational
difference between the two.
Answer: TCP Intercept is generally run in intercept mode, allowing the router to intercept those
TCP SYN requests and answer them on behalf of the server.
If the SYN source is legitimate, a TCP ACK should be received by the router. If and when that
happens, the router considers that three-way handshake to be complete and the SYN source to be
legitimate.
In turn, the router opens a TCP connection to the server, and when that connection is complete, the
router merges the two open connections into one.
This prevents any non-legitimate SYN packets from ever reaching the server. TCP Intercept can be
configured to intercept all incoming SYN packets, or an ACL can be written to identify the source
and destination for packets that should be intercepted.

www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
TCP Intercept can also be run in watch mode, a much more passive mode than intercept mode. In
watch mode, the router does not intercept the SYN packets, but passes them through to the TCP
server.
The router does watch this incomplete connection, and will close it if it's not completed after a
certain period of time - by default, 30 seconds.Use the ip tcp intercept-mode command to configure the
desired mode.
R1(config)#ip tcp intercept mode ?
intercept Intercept connections
watch Watch
connections
R1(config)#ip tcp intercept mode intercept
20-Question: Name the two operational modes for Autosecure and describe the major difference
between them.
Answer: The Autosecure modes:
Interactive, where the admin is prompted for input. This mode is similar to Setup Mode. If you're
going to configure anything requiring user interaction - SSH, enable passwords, etc. - you should use this
mode.
Non-interactive, where Cisco's recommended settings for Autosecure are put into action. Cisco's
recommended settings are very secure - maybe too secure for your network!
Network Attacks And Defenses Questions & Answers:
21-Question Which RFC refers to all of the following network address ranges, and how do these
ranges relate to network security?
0.0.0.0 /8
10.0.0.0 /8
127.0.0.0 /8
172.16.0.0 /12
192.168.0.0 /16
224.0.0.0 /4
240.0.0.0 /4
Answer: RFC 3704 (an updated version of RFC 2827) recommends that packets sourced from those
address ranges not be allowed to enter your network.

www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
Blocking these address ranges for incoming traffic on your network's perimeter routers is sometimes
called "2827 filtering" or "3704 filtering", referring to the original and updated RFCs that discuss
this topic in a great deal of detail.
22-Question Which of the following are considered reconnaissance attacks, and which are access
attacks?
A. ping sweep
B. port scan
C. password attack
D. trust exploitation
E. DSL query
Answer: Recon attacks: ping sweeps, port scans, DSL queries.
Access attacks: password attacks and trust exploitation
23-Question The term "port redirection" refers to which type of network attack mentioned in
Question 2?
Answer: Port redirections are a type of trust exploitation.
24-Question Which of the following statements referring to Superviews and Views are true?
A. IOS Commands can be contained in multiple views on the same router. B.
A single view can be contained in more than one Superview.
C. Deleting a Superview results in all Views contained in that Superview to be deleted as well.
D. Logging into a Superview allows the user to execute all commands in all Views that are part of
that Superview.
Answer: A, B, D. The only false statement is that deleting a Superview results in the deletion of all
of the Views it contain. Deleting a Superview does not result in the deletion of its Views.
25-Question Which of the following are disabled by default when you run Autosecure? A.
PAD
B. UDP and TCP Small Servers
C. BootP
D. CDP

www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
E. NTP
Answer: A, B, C, D, E.
By default, the following will be globally disabled by AutoSecure:
Finger - recon attack possibility
PAD - known vulnerabilities
UDP and TCP Small Servers - attacker can request large number of UDP diagnostics
BootP - known vulnerabilitiest
HTTP services, Identification Service (queries TCP port), CDP, NTP and IP source routing are also
disabled globally.
26-Question Which of the following are enabled by default when you run Autosecure on a Cisco
router?
A. Password encryption service
B. TCP keepalives (inbound only) C.
TCP keepalives (outbound only)
D. TCP keepalives (both inbound and outbound)
E. IP source routing
F. HTTP services
Answer: A, D. Both the password encryption service and TCP keepalives (inbound and outbound)
will be enabled by AutoSecure
27-Question Which of the following will be enabled by default when you run Autosecure?
A. logging timestamps and sequence numbers
B. logging console critical
C. logging buffered
D. logging trap disabled
Answer: A, B, C, D. All of those will be enabled by AutoSecure.
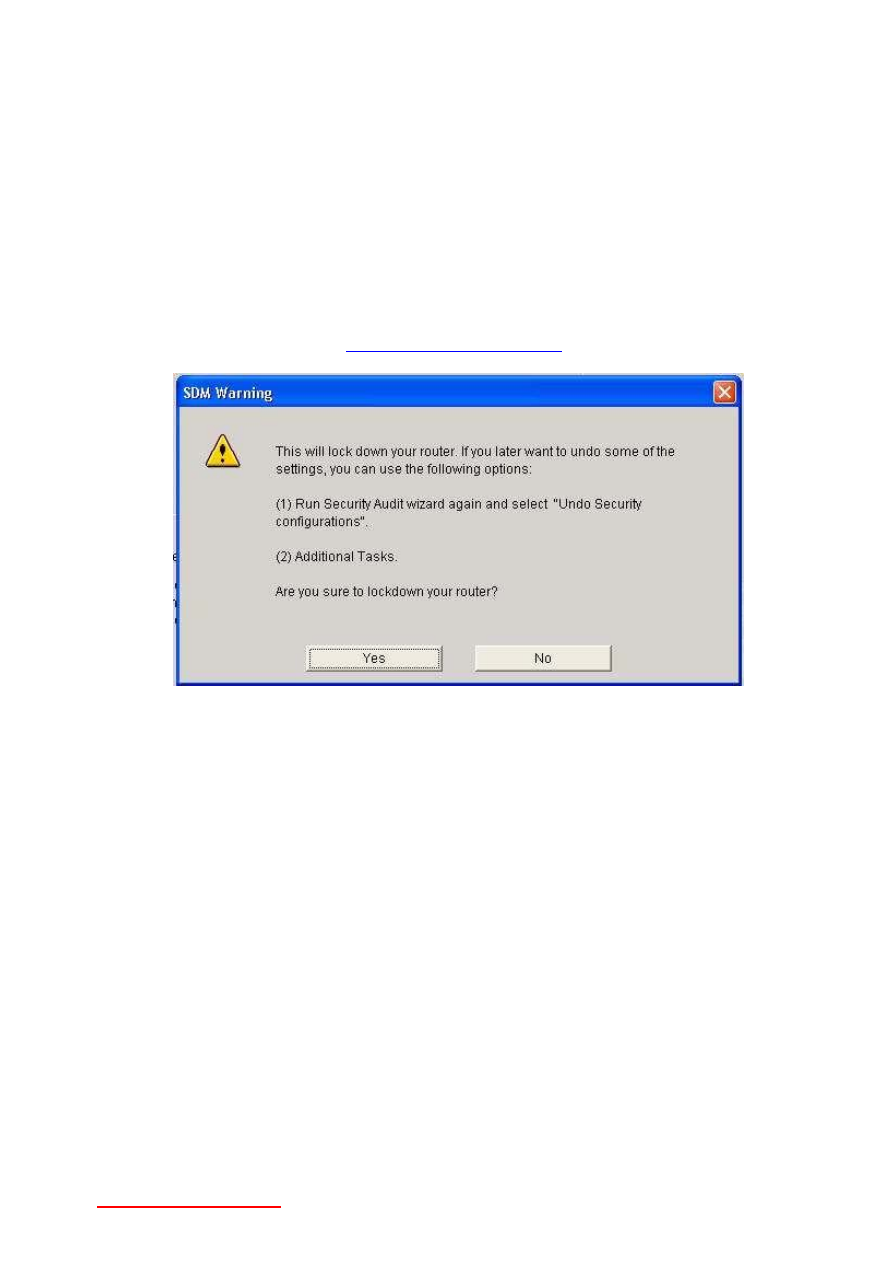
28-Question You're configuring one-step lockdown via SDM. According to SDM, can you undo any
of the lockdown settings once you run the lockdown feature?
www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
A. No, the lockdown is irreversible.
B. Yes, by running Security Audit Wizard and selecting "Undo Security Configurations".
C. Yes, by running the Additional Tasks option.
D. Yes, by choosing "Undo Lockdown".
Answer: B, C. . You can change some or all of the lockdown settings by using the Undo Security
Configurations section of the Security Audit Wizard or by using Additional Tasks, as shown below
in this SDM Screen Shot from my
CCNA Security Study Package
.
29-Question You're running Autosecure at the CLI and decide about halfway through the prompts that
you'd like to stop without saving any of your Autosecure configuration. Can you do this, and if
so, how? (Unplugging the router is not acceptable.)
Answer: Our old friend ctrl-c will do the job, as shown in the prompts you're shown after running the
auto secure command. Note the disclaimer shown at the top of this output!
R1#auto secure
--- AutoSecure Configuration ---
*** AutoSecure configuration enhances the security of
the router, but it will not make it absolutely resistant
to all security attacks ***
AutoSecure will modify the configuration of your device.
All configuration changes will be shown. For a detailed
explanation of how the configuration changes enhance security
and any possible side effects, please refer to Cisco.com for
Autosecure documentation.

www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
At any prompt you may enter '?' for help.
Use ctrl-c to abort this session at any prompt
.
30-Question As it relates to how they are spread, what is the major difference between a worm and a
virus?
Answer: The terms virus and worm are often used interchangeably, but they're not quite the same thing.
A major difference between the two is that a worm can spread from its entry point to the rest
of your network without the "help" of a human being.
A common worm attack is carried out by the worm finding your email address book and then
sending a copy of itself to every recipient in that book. The worm executes its code and then
continues to send copies of itself.
A virus can't be spread without an end user helping out, generally by forwarding an infected file or
attachment.
Practice Questions for AAA essentials
31-Question: Which statement below best describes AAA?
a) AAA is an automobile club
b) AAA is an architectural framework for configuring a set of three independent security
functions in a consistent manner.
c) AAA is a means for authorizing asymmetric (network) access
d) AAA is gives users total access to the network
Answer: B
32-Question: AAA provides which of the following benefits?
a) increased flexibility and
control b) Scalability
c) Standardized authentication methods, such as RADIUS, TACACS+, and Kerberos
d) Multiple backup
systems e) All of the
above
Answer: E
33-Question: Which statement below best describes the AAA philosophy?
a) AAA only allows you to set up group definitions for user access
b) AAA does not allow virtual profiles
c) AAA is designed to enable you to dynamically configure the type of authentication and
authorization you want on a per-user or per-service basis.
d) AAA does not support IPS services

www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
Answer: C
34-Question: Which three security protocols are used by AAA servers? (Choose three.)
a) RADIUS
b)
RADIUS+ c)
TACACS d)
TACACS+
e) Kerberos
f) ISAKMP
Answer: A, D, E
35-Question: Which statement below best describes the difference between RADIUS and
TACACS+?
a) RADIUS uses UDP while TACACS+ uses
TCP b) RADIUS uses TCP while TACACS+
uses UDP c) RADIUS and TACACS+ both use
TCP
d) RADIUS and TACACS+ both use UDP
Answer: A
36-Question: Which statement below best describes the difference between RADIUS and
TACACS+? (Choose Two.)
a) RADIUS encrypts only the password in the access-request packet, from the client to the
server
b) TACACS+ encrypts the entire body of the packet but leaves a standard TACACS+ header.
c) RADIUS and TACACS+ both encrypt the entire body of the packet
d) TACACS+ only encrypts the user password and challenge response and reply
Answer: A, B
37-Question: Which statement below is true?
a) RADIUS supports non IP protocols
b) TACACS+ does not support
AppleTalk c) TACACS+ offers
multiprotocol support d) RADIUS offers
multiprotocol support
Answer: C
38-Question: Which statement below is true regarding the RADIUS protocol?
a) RADIUS does not allow users to control which commands can be executed on a
router and which cannot; therefore, it is not as useful for router management or as
flexible for terminal services.

www.640-553.com Help you pass CCNA SECURITY EXAMS

www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
b) RADIUS allows users to control which commands can be executed on a router, once
properly authenticated, and as permitted in the authorization reply
c) RADIUS, using TCP, secures the authorization and accounting processes by
transmitting sensitive information in a secure tunnel once the connection is properly
authenticated.
d) RADIUS provides for flexible user and device authentication and access
authorization management
Answer: A

www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
Questions & Answers from The Bryant Advantage
1-Question: In terms of their position in the flow of traffic, what's the major difference between an
IPS and an IDS?
Answer: An IDS is not in the direct flow of network traffic. Instead, the traffic flows are mirrored to the
IDS. When infected traffic does hit the network, the IDS will see this and take appropriate
action.
In contrast, the Intrusion Prevention System (IPS) does sit in the middle of the traffic flow - in this
case, the IPS will actually be our Cisco router. When the IPS detects a problem, the IPS itself can
prevent the traffic from entering the network
2-Question: What is SDEE, and what do we use it for?
Answer:
3-Question: What is the highest stratum level in the NTP hierarchy? Can a Cisco router serve at
that level?
Answer: Stratum-0, and no. Typically that role is held by an atomic clock. Cisco routers are good,
but not atomic
4-Question:
What benefit does "GRE over IPSec" offer than IPSec by itself does not?
Answer: By combining GRE and IPSec, each protocol helps to compensate for the other's
limitation:
IPSec adds data integrity and confidentiality that GRE does not offer
GRE offers the ability to carry routing protocol traffic, which IPSec does not offer
Why call it "GRE over IPSec" rather than "IPSec over GRE"? Because the GRE
encapsulation happens first, and then that encapsulation is encapsulated again, by IPSec.
In effect, we have a GRE tunnel inside an IPSec tunnel.
5-Question: You're editing an ACL in SDM and notice some asterisks under source and
destination. What do those asterisks indicate?
Answer:
In SDM, asterisks indicate the ACL keyword any.
6-Question: What is "3704 filtering", and what does it have to do with network security?
Answer: RFC 3704 (an updated version of RFC 2827) recommends that packets from the following
network ranges be prohibited from entering your network:
0.0.0.0
/8
10.0.0.0
/8 (RFC 1918 Class A private range)
127.0.0.0
/8 (loopback address range)
172.16.0.0
/12 (RFC 1918 Class B private range)

www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
192.168.0.0
/16 (RFC 1918 Class C private range)
224.0.0.0
/4 (reserved for IP multicasts)
240.0.0.0
/4 (RFC 1918 Class E private range)
Blocking these address ranges for incoming traffic on your network's perimeter routers is
sometimes called "2827 filtering" or "3704 filtering", referring to the original and updated RFCs that
discuss this topic in a great deal of detail.
7-Question: The following three timers sound a great deal alike, but they have very different
functions. What purpose do each of these timers fill?
ip inspect finwait-time
ip inspect tcp synwait-time
ip inspect tcp idle-time
Answers:
ip inspect finwait-time defines the amount of time between one of the two endpoints of an established
TCP session starts to end the connection and the time that entry is removed from the state table.
Default is 5 seconds.
ip inspect tcp idle-time defines just what you think it would - the amount of time an idle TCP
connection is kept in the state table. Default is 3600 seconds.
ip inspect tcp synwait-time defines the time allowed for a TCP three-way handshake to reach the
Established stage. Default is 30 seconds. If this timer expires, the connection is terminated and the
entry removed from the router's state table.
8-Question: In regards to the IOS Firewall set, what is generic inspection? What's so "generic"
about it?
Answer; I'm not going to show you the entire IOS Help readout for the following command, but
believe me - it's a long, long list. On this particular router, I had over 150 options.
R1(config)#ip inspect name CCNP ?
802-11-iapp IEEE 802.11 WLANs WG IAPP
ace-svr ACE Server/Propagation
appfw Application Firewall
appleqtc Apple QuickTime
bgp Border Gateway Protocol
biff Bliff mail notification
bootpc Bootstrap Protocol Client
If you want to inspect all TCP and/or UDP connections, you can specify TCP and/or UDP as the
inspected protocol, rather than a more-specific entry. This is generic inspection and is configured by
entering tcp or udp at that same point in the ip inspect command.
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
tcp Transmission Control Protocol
udp User Datagram Protocol
This will inspect any TCP and/or UDP protocol traffic, even if the specific application isn't named in the
inspection rule. Generic inspection is designed to allow return traffic for all TCP and/or UDP
connections that are initiated on the inside network.
So why don't we just configure all TCP and UDP traffic to be inspected generically and leave it at
that?
Application-specific commands are not interpreted by generic inspection, and that means that the return
packets may not be allowed to enter the inside network. If the return traffic is using a different port
number than the original traffic, generic inspection may not allow that return traffic to enter the network.
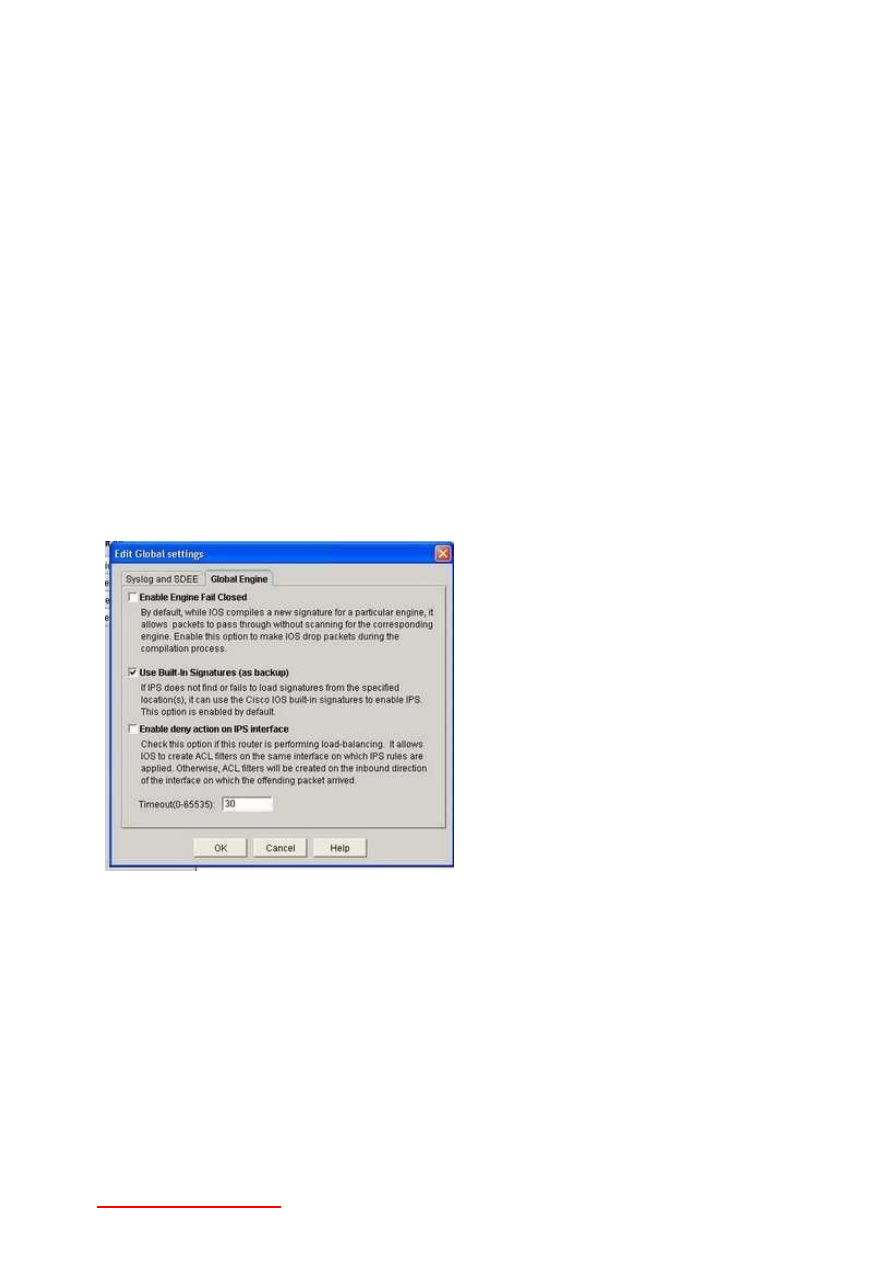
9-Question: What exactly is fail closed? Is it enabled or disabled by default?
Answer: The following illustration from my CCNP ISCW and CCNA Security study guides explains
it! The default settings are shown - note that Fail Closed is off by default.
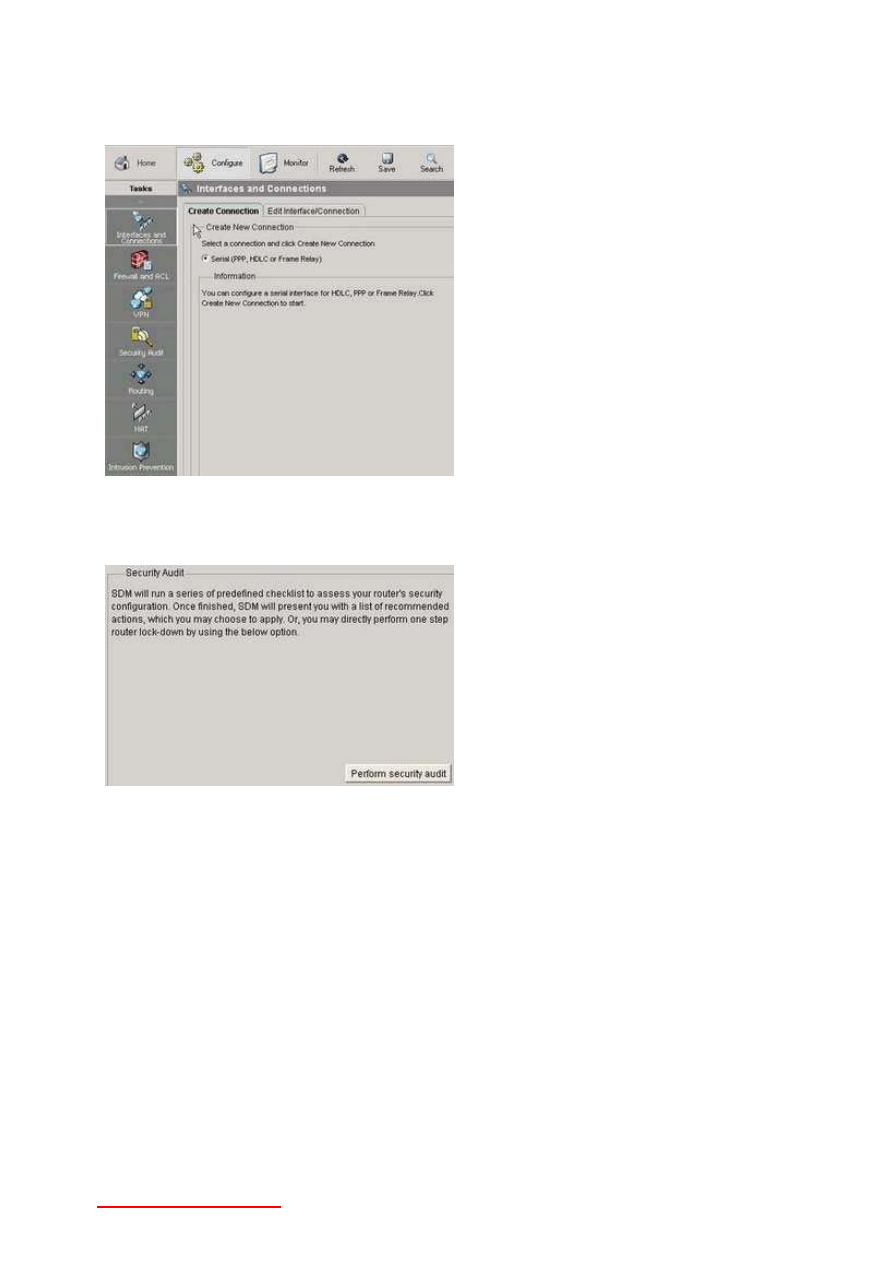
10-Question: You're in SDM and want to perform a one-step router lockdown. Take a look at the
following screen shot and tell me where you should click next.
www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
Answer: Click the Security Audit button. You'll see the following screen at that point - note the
mention of one-step lockdown.
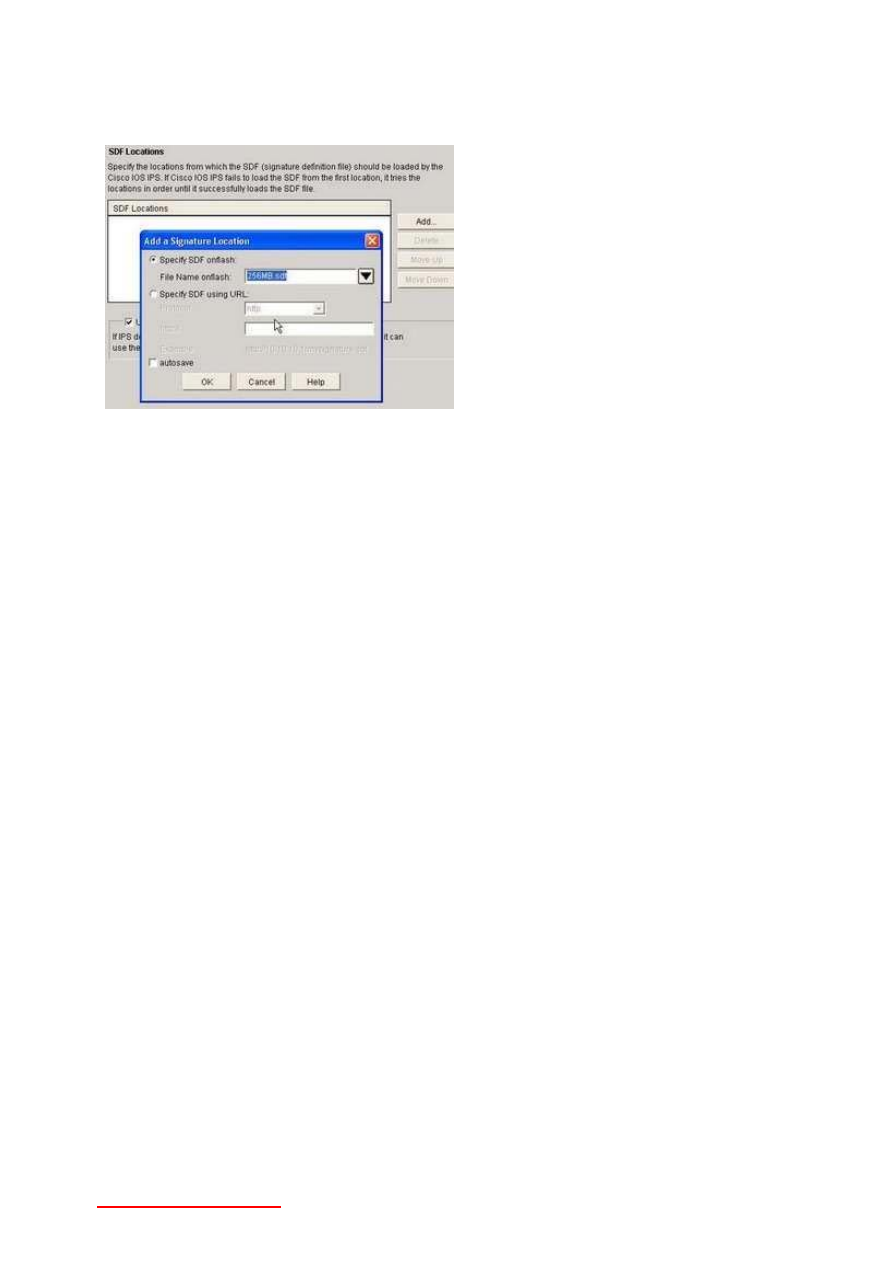
11-Question:
When you're configuring SDM, you have two options for the location of
SDF files. What are they?
Answer: You can specify a URL or Flash, as demonstrated by this screen shot from my
picture
www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
12-Question: What's the difference between symmetric and asymmetric encryption?
Answer: Symmetric encryption is an algorithm where the key that is used for encryption is also
used for decryption. The drawback to symmetric encryption is that the key is used for two purposes,
making it that much easier for an intruder to discover the key.
In contrast, asymmetric encryption involves two keys for both the sender and receiver. This public
key encryption scheme involves a public and private key for each user. Before starting the actual
encryption process, the public key should be certified by a third party called a Certificate Authority
(CA).
13-Question: What is the purpose of the 256MB.sdf file? What does the "256" refer to?
Answer: This is one of three preconfigured Signature Definition Files. Cisco's website recommends
running the Intruder Prevention System (IPS) with the preconfigured files - attack-drop.sdf,
128MB.sdf, and 256MB.sdf. The "128MB" and "256MB" refer to the amount of memory necessary
to use these particular files.
14-Question:
Which of the following does not use encryption?
A. SSH
B. SSL
C. NTP v 3
D. Telnet
E. SMTP v 3
Answer: D. The other four all use encryption in some form.
15-Question: How can you configure SDM to preview the commands before delivering them to the
router, and also give you a confirmation prompt when you leave SDM?
Answer: I personally check Preferences in SDM every time I use it, and I recommend you do the
same. Before proceeding to the Configuration section, go to the upper-left corner of the initial SDM
window and select Preferences, as shown here:
www.640-553.com Help you pass CCNA SECURITY EXAMS

CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
Then you can edit these three prefs to your heart's delight! (The following illustration was trimmed to
fit Blogger.)
16-Question: What is the anomaly method?
Answer: "This is the IPS method of identifying malicious traffic where differences from normal
traffic patterns are sought and detected."
17-Question:
What's the purpose of the attack-drop.sdf file?
Answer: The attack-drop.sdf file is a Signature Definition File that contains the latest
and greatest IPS signatures.
18-Question:
There are three basic methods IPS uses to identify potentially
malicious traffic. Name all three and give a brief definition of each.
Answer:
Both the IPS and IDS can base their identification of dangerous and malicious
traffic on the following:
Policy, where a configured policy may ban particular IP addresses, ports, or even websites
Signature, where byte patterns are considered along with other values.
Anomaly, where differences from normal traffic patterns are sought and detected.
19-Question:
In SDM, you might see a green square next to a signature. What does that
symbol indicate?
Answer: The green square indicates the signature is at its default setting. Here are the two
possibilities, as shown in this image from my CCNA Security Study Package. (Click the
image for a larger view.)
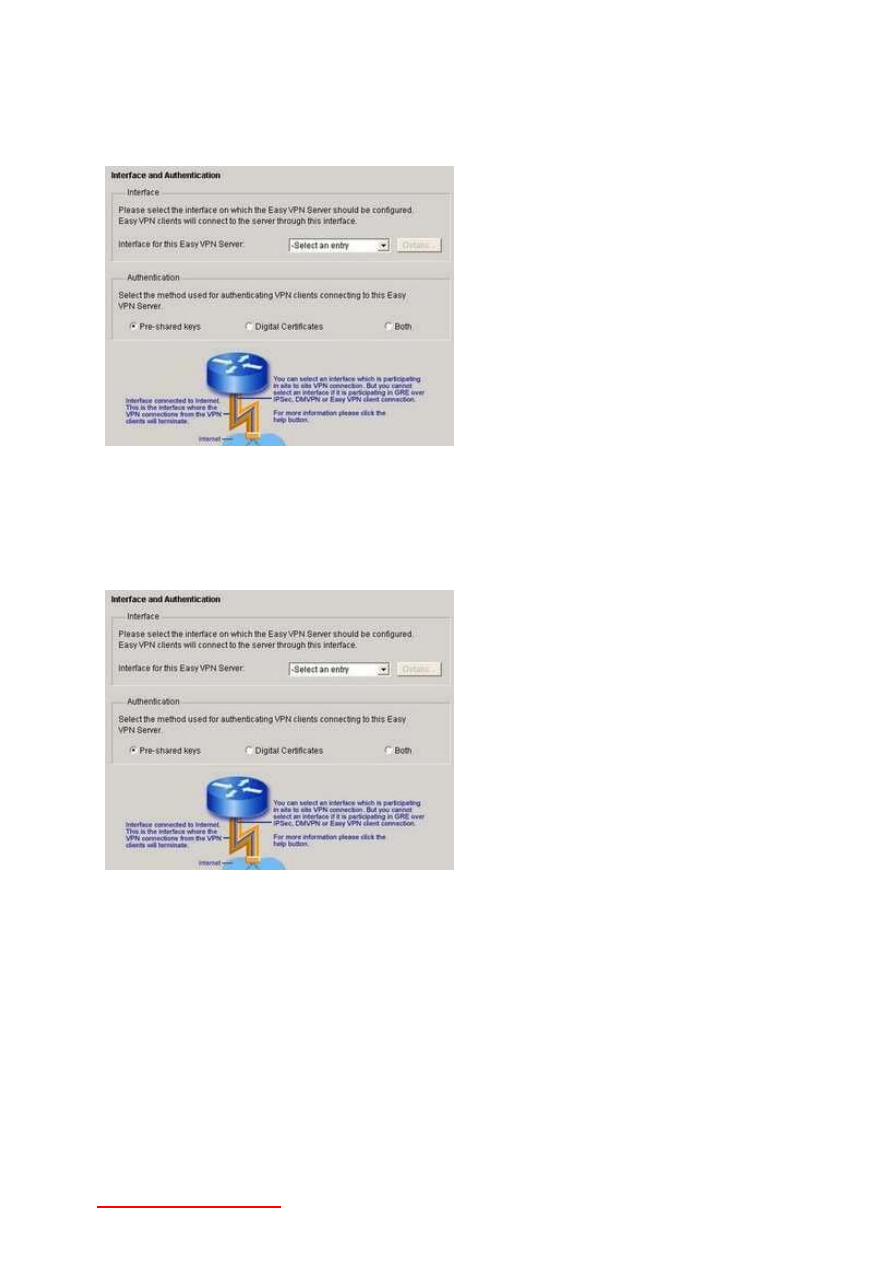
20-Question: You're working in SDM to configure an Easy VPN Server. You'll have three options
for authenticating your Easy VPN Clients. What are they?
Answer: The choices are Pre-shared key, Digital Certificates, and Both, as shown here in this
screen shot from my CCNA Security Study Package. (Click the image for a larger view.)
www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
21-Question: You're working in SDM to configure an Easy VPN Server. You'll have three options
for authenticating your Easy VPN Clients. What are they?
Answer: The choices are Pre-shared key, Digital Certificates, and Both, as shown here in this
screen shot from my CCNA Security Study Package. (Click the image for a larger view.)
22-Question:
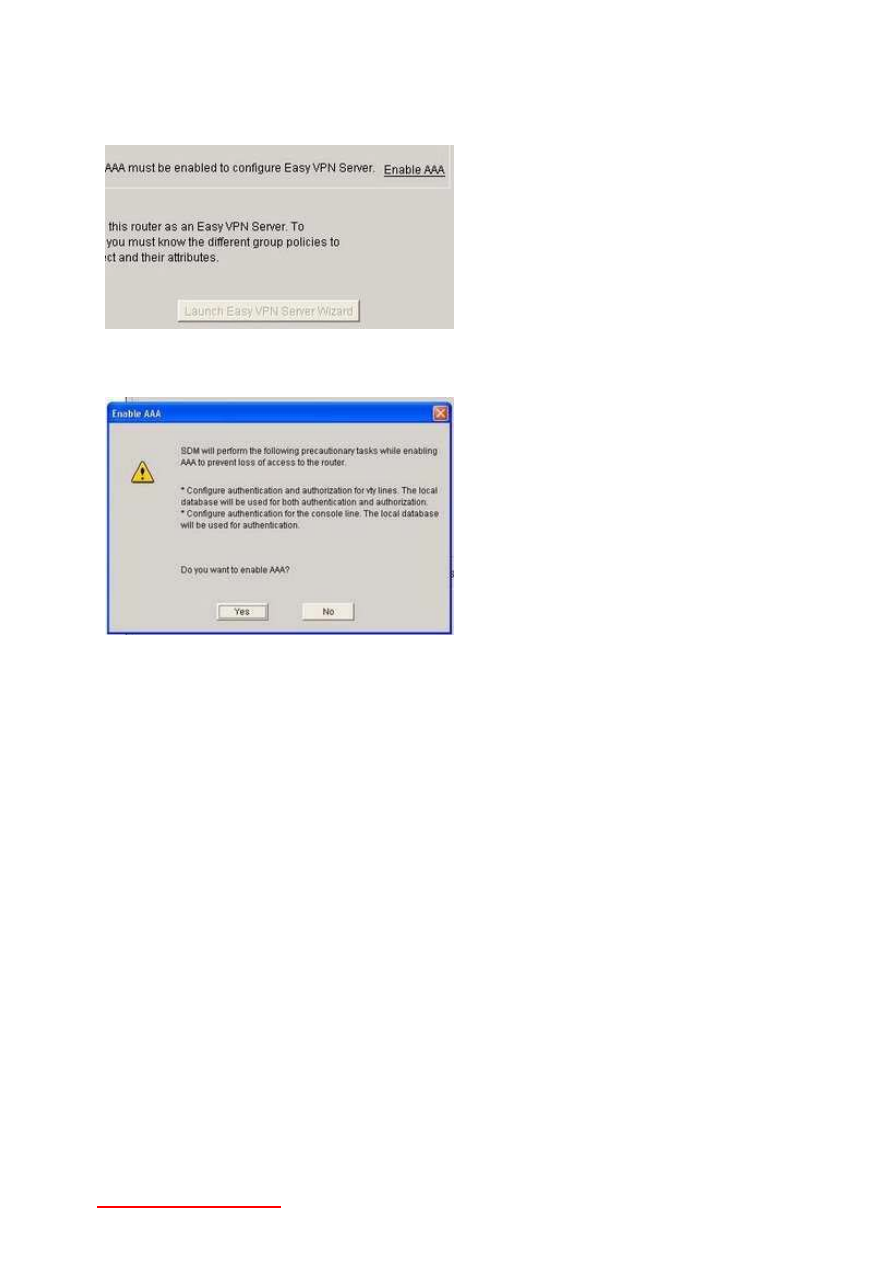
You're working in SDM to create a VPN. What service must be running on
the router to do so? (Hint: If the router isn't already running it, SDM will prompt you to
activate it.)
Answer: AAA must be running. As shown here, the Launch Easy VPN Server Wizard
button will not even be enabled if AAA is not running. Note that SDM has an Enable
AAA option on the right-hand side of the window.
www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
Clicking Enable AAA brings up the following prompt:
Answering Yes will enable AAA on the router and the Launch Easy VPN Server Wizard
button will then be enabled.
23-Question: What's the purpose of the ip inspect tcp idle-time command?
Answer: ip inspect tcp idle-time sets the amount of time an idle TCP connection is kept in the state
table. Default is 3600 seconds.
24-Question: When configuring a basic firewall in SDM, what are the three options for the
preconfigured security levels? Can you create your own custom security levels?
Answer: The options are High, Medium, and Low. In the Basic Firewall Wizard, you cannot create
your own custom security levels, but you can do so in the Advanced Wizard.
25-Question:
In terms of network security, what purpose does a honeypot serve?
Answer: A honeypot is a network device that is purposely left open to attack. The attack
methods are then analyzed in order to develop a defense against that attack type.
(Obviously, this will not be a production server!)
26-Question: You're configuring IPS in SDM, and you just enabled the Fail Closed option. What's
the net effect?
www.640-553.com Help you pass CCNA SECURITY EXAMS

CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
Answer: Here's the exact description of Fail Closed from SDM itself:
"By default, while IOS compiles a new signature for a particular engine, it allows packets to pass
through without scanning for the corresponding engine. Enable this option to make IOS drop
packets during the compilation process."
Fail Closed is disabled by default.
27-Question: In SDM, what does an asterisk indicate when it's used in a graphical
representation of an ACL?
Answer: An asterisk represents the ACL option "any".
28-Question: Name two major differences between the capabilities between the Basic and
Advanced Firewall Wizards in Security Device Manager.
Answer: The Advanced Wizard allows you to configure multiple outside interfaces as well
as a DMZ. The Basic Wizard allows neither of these.
Additionally, the Advanced Wizard allows you to define your own customized rules, where the
Basic Wizard does not. Here's a screen shot of SDM's Firewall And ACL menu that mentions
these differences. (Click the illustration to enlarge.)
29-Question: What are the two options you should expect to see IOS Help display in the
following command?
R1(config)#ip tcp intercept mode ?
Answer: You can run TCP interfcept in intercept or passive mode.
30-Question:
You're using the Authentication Proxy. Where can you store the
user-specific security profiles?
Answer: The profiles can be downloaded from a TACACS+ or RADIUS server.
www.640-553.com Help you pass CCNA SECURITY EXAMS

www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
31-Question:
Identify the true statements:
A. An IPS is in the direct path of network traffic flow. B.
An IDS is in the direct path of network traffic flow.
C. Both an IPS and IDS will be found in the direct path of network traffic flow.
D. Neither an IPS nor an IDS will be found in the direct path of network traffic
flow.
Answer: A. An Intrusion Prevention System will be in the direct path of traffic,
but an Intrusion Detection System will not be found there.
32-Question:
You've just written and applied an ACL, and you notice your
Network Time Protocol deployment is no longer working correctly. What port
should your ACL permit to allow NTP to begin working again?
Answer: NTP uses UDP port 123.
33-Question:
Describe an IP Spoofing attack.
Answer: You may remember from your ISDN studies that when an ISDN line
was pretending to be up, it was said to be spoofing.
When a network intruder uses the IP address of a trusted device in order to
gain access to your network, that's IP Spoofing.
IP Spoofing can be used against your network in several ways:
1. To inject a stream of malicious code and/or commands into your network
2. To trick legitimate network hosts into sending sensitive data to the attacker
3. As part of a reconnaissance attack, an attack that in itself may not be
damaging, but is used to gather information for future, more destructive
attacks.
34-Question:
Briefly describe the purpose of a "SYN cookie".
Answer: One defense against SYN attacks, a SYN cookie verifies the client address
before actually allocating resources to that client.
35-Question: Briefly describe the term "teardrop attack".
Answer: IP fragments with large payloads are the method of attack. Issues with the TCP
fragmentation reassembly code of Windows NT, 96, and 3.1x (among others) created this opening.

www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
36-Question: Which of the following queueing strategies gives priority to interactive, low-
bandwidth communications?
A. FIFO
B. PQ C.
CQ D.
DQ
E. WFQ..
Answer:
37-Question:
In a typical Network Management block, what switch layers are
represented?
A. Access
B. Distribution
C. Core
Answers: A, B. In addition to network management devices, both Access and
Distribution switches will be found here.
38-Question: What protocol number does the Encapsulating Security Payload use?
Answer: 50.
39-Question: What combination of hex characters at the beginning of an IPV6 address indicates a
broadcast?
A. DD
B. EE
C. FF
D. 00110011
E. None of the above.
Answer: E. None of those - IPv6 doesn't use broadcasts.
40-Question: On a low-speed link, how often does EIGRP send hello packets?
A. Every 5 seconds.
B. Every 15 seconds.
C. Every 60 seconds.
D. Every 90 seconds.
E. Every 300 seconds.
Answer:
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
41-Question: Briefly describe a "DDoS" attack.
Answer: A Distributed Denial-Of-Service attack is a typical DoS attack, but one that is carried out by
a large number of attackers rather than a single host.
42-Question: Which of the following possible points of network vulnerability are enabled by
default?
A. NTP
B. TCP / UDP Small Servers
C. BOOTP Server
D. CDP
Answers: C, D. You can turn BOOTP server off with the no ip bootp server command, and you can
disable CDP either globally or on a per-interface basis.
43-Question: What term is given to the network attack that occurs when an intruder gathers
information in preparation for a larger attack in the future?
Answer: That is a network reconnaissance attack. Recon attacks are generally not destructive in
themselves, since the actual point of a recon attack is to avoid notice. It's the information gathered
during the recon attack that we're concerned about, since that info can and probably will be used in
a future attack - and that attack will be destructive.
44-Question: You want to display a message to users who connect to your router via Telnet. What
command will you use to do so?
Answer: Use the banner login command.
45-Question: You're defining inspection rules on a Cisco firewall. What command are you using?
Answer: The global ip inspect command
46-Question:What SDM Wizard is in use below?
Answer: That brick wall in the middle is a firewall, so we know it's a firewall wizard. Since
www.640-553.com Help you pass CCNA SECURITY EXAMS

www.640-553.com Help you pass CCNA SECURITY EXAMS
CCNA Security Q&A
-------by Nar(Naresnet@gmail.com)
we're limited to one outside interface and there's no reference to a DMZ, this must be the
Basic Firewall Wizard. (The Advanced Firewall Wizard allows the configuration of multiple
outside interfaces and a DMZ)..
47-Question: What is the net effect of the following configuration?
R1(config)#access-list 110 permit tcp any
10.0.0.0 0.255.255.255
R1(config)#ip tcp intercept list 110
Answer: To configure an ACL to define the source and destination of packets that should
be subject to TCP Intercept, write the ACL and then apply it with the ip tcp intercept list
command. Most likely, you'll specify a source of "any", as I did in the above example.
48-Question: You're ensuring that only the devices in a VPN that should see the data in
unencrypted format will see the data that way. Which of the following are you practicing?
a) data confidentiality
b) data integrity
c) replay attack protection
d) data origin authentication
Answer: A.
Data Confidentiality means that only the devices that should see the data in an
unencrypted form will see the data that way.
Data Integrity means that the recipient of the data can guarantee that the received data is the
same as the transmitted data - in short, that the data was not altered during transport.
Data Origin Authentication guarantees that the data originated from a specific endpoint.
Anti-replay protection (sometimes just called "replay protection") protects against replay
attacks, a malicious repeat and/or delay of a valid transmission.
49-Question: Do each of the following terms describe TACACS+, RADIUS, both, or
neither? (Answers have been appended to each choice.)
A. encrypts the entire packet - TACACS+ only
B. combines the authentication and authorization processes - RADIUS only
C. supports PAD and ARAP - TACACS+ only
D. cannot control the authorization level of users - TACACS+ only
Wyszukiwarka
Podobne podstrony:
English, Intermediate Grammar Questions answers
101 veterinary technician questions answered
CCNA 2 Final Exam Answers V4 0 (B)
CCNA 2 Module 8 Exam Answers V4 0
CCNA 2 Final Exam Answers V4 0 (C)
CCNA 1 Module 2 Exam Answers V4 0
(autyzm) 100 Questions&Answers About Autism
101 veterinary practice management questions answered
CCNA INTERVIEW QUESTIONS
CCNA 1 Final Exam Answers V4 0
CCNA 2 Module 4 Exam Answers V4 0
CCNA 1 Module 4 Exam Answers V4 0
CCNA 2 Module 9 Exam Answers V4 0
CCNA 1 Module 3 Exam Answers V4 0
CCNA 2 Module 6 Exam Answers V4 0
CCNA 2 Module 2 Exam Answers V4 0
CCNA 1 Module 9 Exam Answers V4 0
CCNA 1 Module 7 Exam Answers V4 0
CCNA 1 Module 6 Exam Answers V4 0
więcej podobnych podstron