9818247287
SAN Security Protocols and Mechanisms
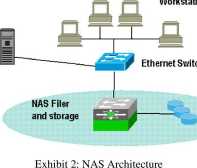
Storage or shortly NAS. NAS architecture consist of a dedicated device named Filer which is actually a stripped down and optimized host for very fast network file sharing. Two most typically supported file Systems on Filers are NFS (Network File Systems) for a Unix world and CIFS (Common Internet File System) for the Microsoft world. . While NAS solution has its main advantage in simplicity in maintenance and installation, its main drawback is limited file and operating system support or support of futurę new file systems. Architecture of a NAS is illustrated in Exhibit 2.
The latest mechanism of attaching storage remotely with a błock level access is commonly referred as Storage Area Network or SAN. SAN consist of hosts, switches and storage devices. Hosts eąuiped with Host Bus Adapters (HBA) are attached via optical cable to a storage switches which act as a fabric between the hosts and the storage devices. SAN architecture is illustrated in Exhibit 3.
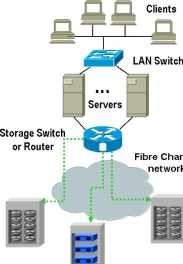
Exhibit 3: SAN Architecture
Wyszukiwarka
Podobne podstrony:
SAN Security Protocols and Mechanisms_2_ Storage Area Networks Security Protocols and Mechanisms Ind
SAN Security Protocols and Mechanisms Storage Area Networks Security Protocols and Mechanisms 1 Intr
SAN Security Protocols and Mechanisms 12 One host or storage device could also belong to a multiple
SAN Security Protocols and Mechanisms 20 6 Futurę directions Storage security is still evolving topi
SAN Security Protocols and Mechanisms 10 networks, allowing a commodity IP network to function in a
SAN Security Protocols and Mechanisms 3.3 Access Control and Authentication Another critical aspect
SAN Security Protocols and Mechanisms 13 4.1.3 Fibrę Channel Security Protocols To address additiona
SAN Security Protocols and Mechanisms 14 4.1.3.1.2 Fibrę Channel Authentication Protocol Fibrę Chann
SAN Security Protocols and Mechanisms 15 4.1.3.2FC-SP per frame confidentiality and integrity Recogn
SAN Security Protocols and Mechanisms 16 FC-2 Payload: 0-528 Transmission
SAN Security Protocols and Mechanisms 17 • Data Origin Authentication The IPsec re
SAN Security Protocols and Mechanisms endpoints can be determined, the true source and destination e
SAN Security Protocols and Mechanisms 19 An iSCSI node must also support Internet Key Exchange (IKE)
SAN Security Protocols and Mechanisms Index of Exhibits Exhibit 2: NAS
SAN Security Protocols and Mechanisms The invention of a Fibrę Channel (FC) has opened a complete ne
SAN Security Protocols and Mechanisms iSCSI enables SCSI-3 commands to be encapsulated in TCP/IP pac
SAN Security Protocols and Mechanisms Exhibit 6: Fibrę Channel Protocol Stack The lowest level (FC-0
SAN Security Protocols and Mechanisms FCIP transports Fibrę Channel data by creating a tunnel betwee
EuroFlow standardization of flow cytometry protocols 1996 step, one or morę washing steps and an ery
więcej podobnych podstron