13
ehsan 08
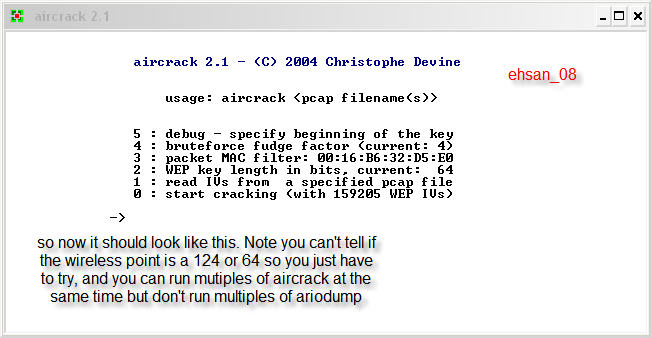
aircrack 2.1 - <C> 2004 Christophe Devine
usage: aircrack <pcap filename<s>>
5 : debug - specify beginning of the key 4 : bruteforce fudge factor <current: 4> 3 : packet MAC f ilter: 00:16:B6:32:D5:E0 2 : WEP key length in bits, carrent: 64 1 : read IUs fron a specified pcap file 0 : start cracking <with 159205 WEP IUs>
so now it should look like this. Notę you can't tell if the wireless point is a 124 or 64 so you just have to try, and you can run mutiples of aircrack at the same time but don't run multiples of ariodump
Wyszukiwarka
Podobne podstrony:
ehsan 08 aircrack 2.1 * Got 159205? unique IUs ! fudge factor = 2 * Elapsed time [00:00:05] ! tried
airodump 2.1BEIE3 airodump 2.1 - <C> 2004 Christophe Deoine usage: airodump <nic index>
airodump 2.1 airodump 2.1 - <C> 2004 Christophe Deoine usage: airodump <nic index> <n
airodump 2.1 airodump 2.1 - <C> 2004 Christophe Deuine usage: airodump <nic index> <n
Przestępstwa o charakterze terrorystycznym - konsekwencje WTC. 08.01.2004 rządowy projekt zmiany kk,
84094 Scale Aircraft Modelling 15 08 The Best for Modelling and Reference JM 5-14M _WiwW-nwfl* lu .i
Spy Planes and Electronic Warfare Aircraft (1983) AN ILLUSTRATED GUIDE TOand Ęjictronic Warfare Arcr
Dynamics of a controlled anti-aircraft missile... 291 t [s] t [s] Fig. 13. Time-de
295 Dynamics of a controlled anti-aircraft missile... 6. Dziopa Z., 2008, The Mode
281 Dynamics of a controlled anti-aircraft missile... The launcher is a perfectly stiff body with ma
283 Dynamics of a controlled anti-aircraft missile... Motion of the controlled launcher mounted on a
285 Dynamics of a controlled anti-aircraft missile... The ąuantłties ip^v and present in the above f
więcej podobnych podstron