Alcatel-Lucent Scalable IP Networks Lab Guide
Version 2.0.1
2009-02-13
1
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
Table of Contents
.............................................................................11
...............................................................................13
............................................................................................21
List of Figures
Figure 1 Two Enterprises linked to a common ISP ............................................................ 11
Figure 2 Two ISPS............................................................................................................. 13
Figure 3 Static routes CE to PE and P, PE to CE ............................................................... 21
Figure 4 OSPF in each ISP ................................................................................................. 26
Alcatel-Lucent
for
internal
use
only
--
Do
Not
Distribute
Lab 1 Hardware Configuration
Section 1.1 – System Identification
Objective:
In this exercise the student will configure the date and time on the router. Once
completed, the student will change the system name of the router to reflect its node
number.
1. Log in to your node
Login to your node using the default login (admin) and password (admin).
2. Set the system time and date
SR#
admin set-time <YYYY/MM/DD hh:mm>
SR#
show time
↵
3. Change the system name
Change the system name to RX (X=your node number).depending on which router
you are logged into
SR#
configure system name <RX>
The CLI system prompt will now display the system name.
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
Section 1.2 – System Configuration
Objective:
In this exercise the student will simply verify their current router configuration This will
involve executing a “show” command to view the contents of the BOF (Boot only file)
system.
1. Simply execute the following command
a. Verify that the IP address is the management IP address used to login to the router
b. Verify the Management Ethernet port configuration settings.
RX#
show bof
===============================================================
BOF
(Memory)
==============================================================
primary-image ftp://*:*@<IPAddress>/.. /7750_40r5/i386-both.tim
primary-config
Address>/../SIM02/R01/config.cfg
address 192.168.119.129/24 active
static-route 128.0.0.0/1 next-hop 192.168.119.1
autonegotiate
duplex full
speed 100
wait 4
persist on
console-speed 115200
=============================================================
2. Saving your configuration
RX#
admin save
This will save the configuration to the config.cfg file shown above in the bof output
To save the configuration to a different file name, the exact location and name of the
file must be specified
RX#
admin save
- save [<file-url>] [detail] [index]
<file-url> : <local-url>|<remote-url> - [255 chars max]
local-url - [<cflash-id>/][<file-path>]
remote-url - [{ftp://|tftp://}<login>:<pswd>@
4
IP Management
Address
Ethernet Port
Parameters
Configuration
file
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
<remote-locn>/][<file-path>]
cf1:|cf1-A:| cf3:|cf3-A:|cf3-B:
<detail> : keyword - Adds default configuration
<index> : keyword - Forces a save of the index file
The location here can be a compact flash location, ftp server or tftp server
5
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
Section 1.3 – Hardware
Objective:
In this exercise the student will configure Input/Output Modules (IOM), Media
Dependent Access (MDA) and the ports. The student will then ensure that the ports are
properly configured as far as mode and MTU. The configurations are slightly different
between the physical router and the router simulator.
IOM/MDA Configuration
1. In this step the student is not actually configuring the IOM card. The student is
configuring the card slot. The IOM card itself already knows what it is. This
command shows what type of cards it should expect to see installed.
RX#
show
card
↵
Configure the appropriate slot with the equipped card.
RX# configure card <slot>
↵ (where slot is 1-10 depending on the
router)
RX>config>card# card-type iom-20g
↵ (this can be different,
Please verify the correct card in the slot by doing a ‘show
card’)
RX>config>card#
no shutdown
↵ (by default all cards are shutdown)
2. The next step is to configure the daughter card slots on the IOM
RX# show mda
↵ (
command to show all MDAs installed on all cards
)
RX>config>card# mda 1
↵
RX>config>card>mda# mda-type m60-10/100eth-tx
↵ (
this can be different,
Please verify the correct mda in the slot by doing a ‘show mda <card
>’)
RX>config>card>mda# no shutdown
↵
3. Confirm that the configurations were correctly done by using the following
commands. The equipped card type and the provisioned card type listed in the CLI
window should be identical.
RX#
show
card 1
↵
6
RX#
show
mda 1/1
↵
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
RX#
show
mda 1/2
↵
4. Note: The cards and MDAs can be configured incorrectly; there is no visible warning
to determine if these components were wrongly configured other than the default
alarm logs (see Configuring Alarms Section 1.4). Although the router will accept an
incorrect configuration, any service on the incorrectly configured cards/MDAs will
not work correctly
5. Once the cards are correctly configured then configure the ports on the MDAs.
Unlike the cards where it was a hierarchical configuration structure, the ports are not
configured as part of the MDA hierarchy. The student must exit back to the root and
then enter into the port configuration mode. The ports are identified by first
identifying the IOM, then the MDA and then the port (1/1/1). By default, the ports on
a 60 port 10/100 card are network mode with a MTU of 1514. The default settings
will suffice for the remainder of this course.
RX>config>port 1/1/1
↵
RX>config>port#>
no shut
↵
RX>config#
port 1/1/[1..4] no shut
↵
(This command will enable you to configure a string of ports at one time. In this case,
this command will turn all 4 ports administratively on.)
6. Use the following commands to verify that the configurations at the port level are
correct and functioning properly.
RX# show port
↵
RX#
show port 1/1/1 detail
↵
(The “detail” extension on a show command will display everything possible about the
item specified. This command is very useful in troubleshooting.)
7
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
Section 1.4 – Logs
Objective:
In this exercise the student will configure log-ids and verify their operation. The student
will then set up a relationship within the log-id to identify the source of the information
(the logger) and the destination of the information that they wish to capture.
1. Create a Log ID and associate the Log to memory
RX#
configure log log-id 21
↵ (the range is 1-100 however 99,100 are
reserved)
RX>configure>log>log-id$
description “Main Stream Log”
↵
RX>configure>log>log-id$
from main
↵
(This is the source of the information
that you wish to capture)
RX>configure>log>log-id$
to memory
↵
(This is the destination)
RX>configure>log>log-id$
info detail
↵
RX>configure>log>log-id$
exit
↵
RX#
show log log-id 21
↵
2. Using the same configuration steps that you have just completed for step 1, repeat the
process to configure three other log files using the following parameters:
Description:
Security Log File
Log
–id:
22
Log
Source:
security
Destination
memory
Description:
Debug-Trace
Log-id:
23
Log
Source:
debug-trace
Destination:
session
Description:
Change
Log
Log-id:
24
Log
Source:
change
Destination:
memory
3. Verify the log files configuration and output
8
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
a. Observe the log file configuration
RX# configure log
↵
RX>configure>log>
info
↵
b. Observe the security log
To test the security logging, open another session to the same router that you are
logged into. Try logging in to the router using a wrong login/password
On the active session, now execute a
RX#
show log log-id 22
↵
Observe the failed login attempts
c. Observe the Change log
RX#
show log log-id 24
↵
Observe all the events in the change log. What kind of events are logged here?
d. Observe the Debug log
Note: This will be viewed when debug events are turned up in succeeding labs
e. Observe the Main log
RX#
configure port 1/1/5 no shut
↵
RX#
exit
↵
RX# show log log-id 21
↵
RX#
configure port 1/1/5 shut
↵
f. Logout from the active ssh/telnet session first then open a new session to the
node and now type
RX#
config log
↵
RX#
info
↵
Compare the output of the info command to the output obtained at the beginning of this
step. Is there a difference and why?
4. Configuring and viewing alarms
9
Alarms on the 7x50 are not directly displayed. Two log files (log id 99 and log id 100)
are configured automatically on startup to capture alarm events for layer 1 and layer 2.
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
To view these alarms execute
RX>
show log log-id 99
↵
RX>
show log log-id 100
↵
Appropriate parameters can be used in order to display specific information.
5. Save your configs
RX> admin save
10
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
Lab 2 IP Addressing and Routing
Section 2.1 - ISP addressing with Enterprise Customers
Objective:
In this exercise the student will design and implement an IP network addressing scheme
to support the communications between the routers as shown in the diagram below. This
is a paper exercise
Figure 1 Two Enterprises linked to a common ISP
11
Ent. A.1
30 hosts
Ent. B.2
300 hosts
Ent. B.1
90 hosts
Ent. A.2
60 hosts
ISP
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
Two enterprises, A and B are connected to a central Tier 2 ISP. A.1 and A.2 are two of
Enterprise A’s locations connected to the Tier 2 ISP and B.1 and B.2 are two of
Enterprise B’s locations connected to the same Tier 2.
The ISP has a public IP addressing space of 138.120.16.0/20. The Enterprises A and B
lease their IP addressing from their ISP. Enterprise A requires an IP addressing scheme
that can scale to at most 30 nodes in location A.1 and 60 nodes in location A.2. The
Enterprise B requires an IP addressing scheme with at most 90 nodes in location B.1 and
less than 300 nodes in location B.2. The ISP can only lease 500 IP addresses (among the
two enterprises) and will utilize the last part of its assigned sub-network to both the
enterprises.
Your tasks are to
1) Extract a 500 host sub-network from the last part of the ISP IP network address of
138.120.16.0/20.
2) Divide the resulting sub-network into unequal sub-networks satisfying all the site
requirements for each of the enterprise locations. Note: The sub-networks
assigned to each location do not have to be a single aggregate block so long as
they satisfy the number of addresses required.
3) Wherever possible optimize address spaces among Enterprise locations.
Hint: Divide the assigned ISP IP sub-network into equal blocks satisfying the smallest
requirement and then combine the smaller blocks into aggregate or non aggregate
blocks.
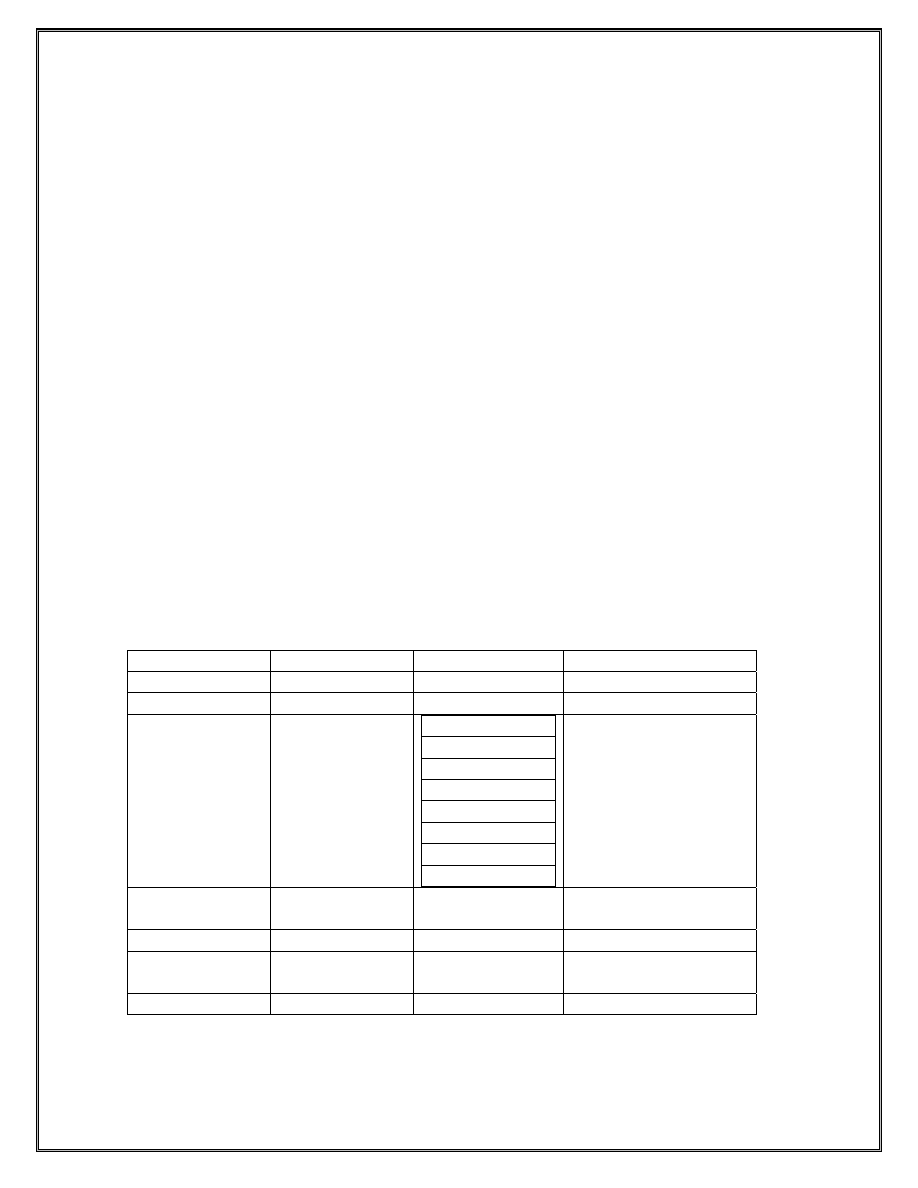
Entity
Number of Host
Addresses
IP Network
ISP Network
4094 138.120.16.0/20
Subnetwork Assigned to
Enterprise A and B
510
Enterprise A
Location A.1
Location A.2
Enterprise B
Location B.1
Location B.2
12
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
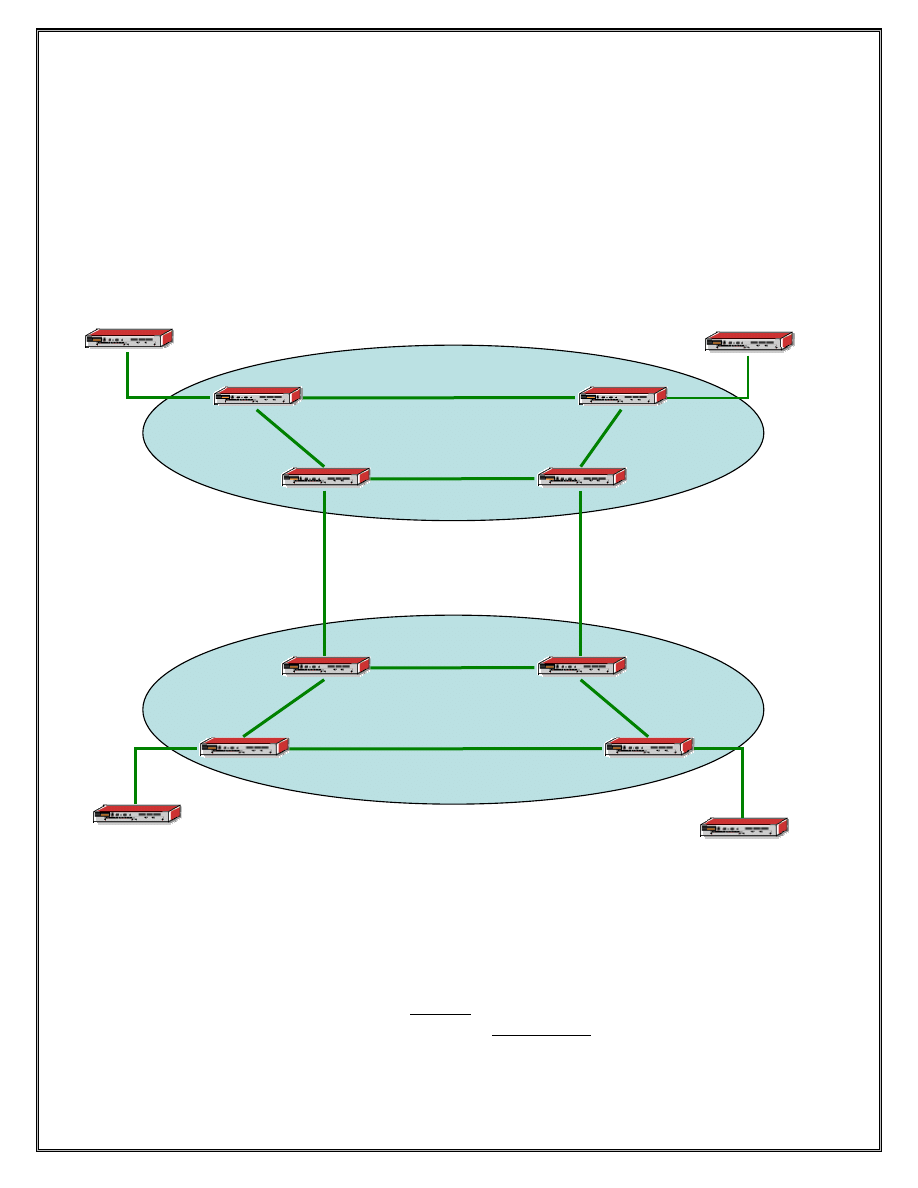
Section 2.2 – ISP addressing with P, PE and CE routers
Objective:
In this exercise the student will design and implement an IP network addressing scheme
to support the communications between the routers as shown in the diagram below. The
IP addressing schema will be used further in the subsequent lab exercises.
CE4/R12
Figure 2 Two ISPS
There are two ISPs shown in the above diagram. ISP 1 consists of routers P1, P2, PE5
and PE6. ISP 2 consists of routers P3, P4, PE3 and PE4.
P1 and P2, P3 and P4 are considered provider routers and serve as transit points to other
provider routers. PE1 and PE2, PE3 and PE4 are provider edge routers and connect to the
ISP customers. These routers provide Internet and other network access to the ISP
customers.
13
ISP 1
ISP 2
P1/R1
P2/R2
P3/R3
P4/R4
PE2/R6
PE3/R7
PE1/R5
PE4/R8
CE1/R9
CE3/R11
CE2/R10
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
CE 1 and CE2 are customer edge routers that represent customers of ISP 1. CE3 and CE4
are routers that represent customers of ISP2. These routers provide traffic from the ISP to
the various customer entities
Each ISP is assigned the following public address space by IANA
ISP 1
140.10.0.0/24
ISP 2
150.10.0.0/24
Your task is to design an IP sub-network based on the address space provided and assign
the sub networks to the various routers based on the following requirements which are the
same for both ISPs. Note: All students assigned to each of the ISP must collaborate
together.
Requirements
1. The first 32 addresses in the assigned IP space for both ISPs are reserved for system
and other internal loopback addresses on the P, PE. Each of the routers in the ISP and
will require a system address from this block
2. The next 64 addresses in the assigned IP space for both ISPs are reserved for future
use.
3. All customer routers on both ISPs are connected to at most 60 hosts. So each ISP
needs to assign two 60 host addressing schemes to represent all the customers.
4. All inter router links including CE-PE router links within each ISP are point to point
links, however for the sake of convenience, they should be assigned ‘/30’ based
addresses.
5. ISP 1 and ISP2 provider routers are physically connected to each other but are not
peering to each other.
Enter the addresses in the table below.
ISP Number 1
Router
Port
Interface name
IP Address
PE1
System
toP1
toPE2
toCE1
P1
System
toP3
Not
used
toP2
toPE1
PE2
System
toP2
14
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
toPE1
toP1
P2
System
toPE2
toP4
Not
used
toP1
CE1
System
Not
used
toPE1
Aggregate
CE2
System
Not
used
toPE2
Aggregate
ISP Number 2
Router
Port
Interface name
IP Address
PE3
System
toP3
toPE4
toCE3
P3
System
toP1
Not
used
toP4
toPE3
PE4
System
toP4
toPE3
toCE4
P4
System
toPE4
toP3
toP2
Not
used
CE3
System
Not
used
toPE3
Aggregate
CE4
System
Not
used
toPE4
Aggregate
15
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
Section 2.3 – Layer 3 Interfaces
Objective:
In this exercise the student will configure the layer 3 interfaces as per the IP addressing
scheme listed in the tables in the previous exercise.
1. Using the following command take a look at any existing interfaces on the router.
Notice that the system interface is already created. This interface exists by default
and cannot be removed. The only requirement is to assign the system interface with
an IP address. The system interface will be automatically used by the various routing
protocols as the router-id.
XXX>show router interface
↵
2. Assign the IP address to the system interface as per the above table on the PE and P
routers.
XXX>config>router
↵
XXX>config>router#
interface system
↵
XXX>config>router>if#
address xxx.xxx.xxx.xxx/32
↵
XXX>config>router>if#
exit
↵
3. Assign the IP addresses to the rest of the interfaces on the CE, PE and P routers. The
difference between these interfaces and the system interface is the fact that the non-
system interfaces require the addition of a physical port.
a. The system interface, being a loopback or virtual interface, does not have a
physical port assigned to it.
b. Other non-system interfaces can also be created as loopback interfaces (as
shown below) and also not required the addition of a physical port. However
they need to be explicitly configured as a loopback interfaces by specifying
the command “loopback”.
c. The customer networks on the CE router can be specified as a loopback
interface for the purpose of aggregation, however on the loopback interface, a
single host address in the customer network needs to be defined.
Interface Type
Name
Loopback
Subnet Mask
Port Config
Normal “Any
String”
No /8-/31 Required
System
system
Implicit /32
None
loopback
Loopback “Any
String”
Explicit
/8-/31
16
XXX>config>router#
interface Hosts
↵
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
XXX>config>router>if$
address xxx.xxx.xxx.xxx/yy
↵
XXX>config>router>if$
loopback
XXX>config>router>if$
exit
↵
4. Continue until all the interfaces have been assigned an IP address and the interface
has been associated to the correct port. Once completed, use the show command to
see the status of the router interfaces that have just been created. The administrative
and operational status should both be up. If an interface shows operationally down,
this could be indicative of a physical problem. Use the info command to view the
configuration of the router interfaces to ensure that they have all (with the exception
of the System interface) been associated with a port.
XXX>show router interface
↵
XXX>config>router
↵
XXX>config>router#
info
↵
5. Using the show command, check the route tables of all the CE, PE and P routers in
your ISP. Notice the routes that now appear in the route table and take note of their
protocol type. The PE routers should see 4 routes in the route table while the P
routers should see 4 routes in the route table.
XXX>show router route-table
↵
Is there a difference between the outputs of the ‘show router interface’ command and
the ‘show router route-table’ command? What is the difference?
__________
6. Using the ping command, check connectivity from a router to the distant end of each
of its interfaces to the neighboring routers. For example, on the PE routers check the
connectivity to the distant end of the interface connecting it to the P router and on the
CE router, check the connectivity to the PE router.
17
XXX>ping xxx.xxx.xxx.xxx
↵
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
Section 2.4 – Testing for ICMP and ARP
Internet control messaging protocol is an IP protocol used to report on errors delivering
an IP datagram. When a destination address is unreachable, the router that cannot find the
destination sends an ICMP destination unreachable to the source of the IP datagram. ARP
is a mechanism used to find out the MAC address corresponding to a specific IP address,
if one does not exist in the source’s ARP cache.
1. To verify ICMP messages are being generated, turn on debug for ICMP packets on all
core routers. To turn debug icmp on (if you had to open a new session to your node
via telnet or ssh you may need to create your log-id for sending debug information to
your session (Lab 1.4 Step-1):
XXX> debug router ip icmp
↵
2. From the edge devices, attempt to ping the IP address of the far-end interface to your
core router, using your edge’s system interface address as the source address. Observe
the debug ICMP messages on the core routers.
3. To verify ARP operation by the router, turn on debug IP ARP on the routers in any
ISP (P1-P2, P3-P4, PE1 and PE2, PE3 and PE4) routers. Execute the following
command on each of the routers
XXX> debug router ip no icmp
↵
XXX> debug router ip arp
↵
XXX> clear router arp all
↵
XXX> show router arp
↵ (This should be empty now)
4. NOTE: Wait until all students are at this point before proceeding.
From any PE router, attempt to ping the system interface IP address of all the other
directly connected routers. Observe the debug ARP message. Verify the ARP entry
for the neighboring interface has been added
XXX> show router arp
↵
How many ARP entries are on each router at this point? __________
18
5. From any P router, attempt to ping the network interface IP address of all the other
connected routers. Observe the debug ARP message. Verify the ARP entry for the
neighboring interface has been added
XXX> show router arp
↵
How many ARP entries are on each router at this point? __________
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
19
Explain
________________________________________________________________________
________________________________________________________________________
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
Lab 3 Dynamic IP Routing
Section 3.1 – Static Routes
Objective:
In this exercise the student will configure a static route from the PE to the P router and
from the P router to the PE router that will allow both routers to ping the system interface
of each other. At this point, the operator can only ping the interfaces that are directly
connected to the router. This is because those are the only networks that are known by
the router. Should the operator at the PE router attempt to ping the system interface of
the P router it will fail as the PE router has no route to the destination (it is not shown in
the route-table).
1. The first step is to define the network that the operator wishes to reach. In this case it
will be the address of the system interface of the distant router. Once that is defined
then the router must be informed of which interface to send the information out of to
reach the distant network. Note, when defining the “next-hop” interface information,
the IP address used is the distant IP address of the interface not the local IP address of
the router interface. Log in to the PE router and configure a static route using the
following command structure. The first IP address defined is the destination network
plus mask. In this case it is the system interface of the P router. The second IP
address defined is the IP address of the P end of the interface that connects the P to
the PE.
XXX>configure router static-route xx.xx.xx.xx/yy next-hop
xx.xx.xx.xx
2. The next step is to log on to the P routers and configure a static route to the system
interface of the PE router. The command structure is the same as above. The only
thing that will change is the IP addresses.
3. Once completed, verify connectivity between the P and PE routers in your pod by
pinging the system interface of the other router.
XXX>ping xxx.xxx.xxx.xxx
↵
4. View the contents of the routing table and answer the following questions.
XXX>show router route-table
↵
a. How many routes in the table? ________
b. What is the preference and metric value of each type of routing entry?
________________________________________________________________________
________________________________________________________________________
___________________________________________________
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
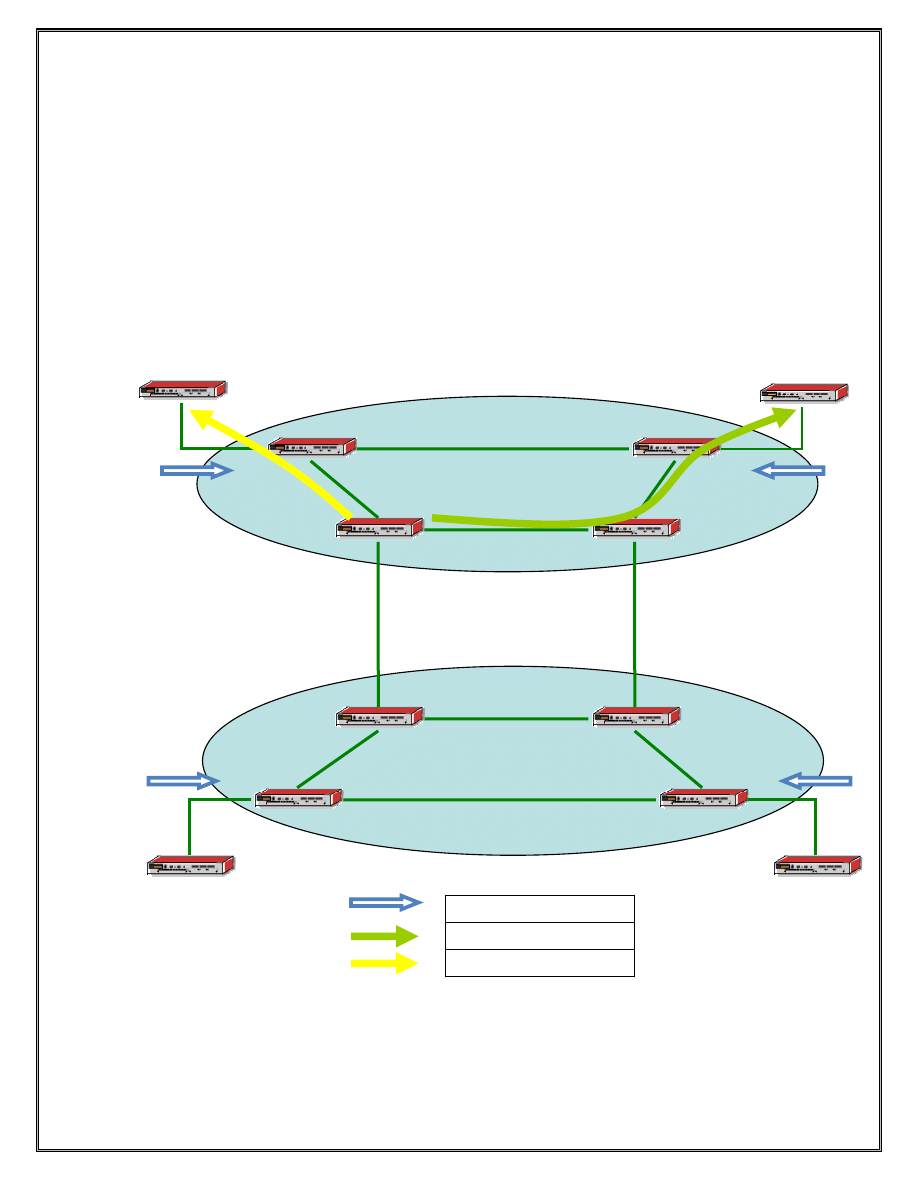
Section 3.2 – Default Routes and Router Logic
utes and Router Logic
Objective:
Objective:
In this exercise the student will configure a default route on the Customer Edge CE
router. The purpose of this default route is to allow IP connectivity from the CE router to
the rest of the routers in the network. This is possible due to the fact that the CE router
has only one interface towards the ISP core. Therefore, if the destination is not local, it
must be out that interface.
In this exercise the student will configure a default route on the Customer Edge CE
router. The purpose of this default route is to allow IP connectivity from the CE router to
the rest of the routers in the network. This is possible due to the fact that the CE router
has only one interface towards the ISP core. Therefore, if the destination is not local, it
must be out that interface.
CE4/R12
CE4/R12
Figure 3 Static routes CE to PE and P, PE to CE
Figure 3 Static routes CE to PE and P, PE to CE
21
ISP 1
ISP 2
P1/R1
P2/R2
P3/R3
P4/R4
PE2/R6
PE3/R7
PE1/R5
PE4/R8
CE1/R9
CE3/R11
CE2/R10
Static Route Type 1
Static Route Type 2
Static Route Type 3
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
For this exercise, the CE devices will configure default routes towards their
connected PE router. Each P and PE router will configure static routes for the CE
networks (the aggregate networks that were created as part of the subnetwork exercise
in Section 2.2) connected to their local ISP. For example P1 and PE1 will each
configure a static route to CE1 networks and another static route to the CE2 networks.
Note that each P and PE router will configure 2 static routes for each CE.
1. To configure a default route is to configure a static route. The only difference is the
destination network and mask information. In a default route, the wild card network
and mask is used to match all network prefix values that do not match anything else
in the route-table. Use the following configuration on the edge router of your pod.
For the next hop use the interface as defined on the previous page.
XXX>configure router static-route 0.0.0.0/0 next-hop xx.xx.xx.xx
↵
2. Log on to the core (P and PE) routers and configure static routes for each CE
customer network address of the CE routers in your local ISP. For each network,
there are 2 paths through your ISP. For this exercise, you will enter both static routes
into each P/PE router. The difference will be the metric value that is used. The value
of the metric is the total number of routers (including the local router) traversed to
reach the destination device.
XXX>configure router static-route xx.xx.xx.xx/yy next-hop
xx.xx.xx.xx metric z
↵
3. Use the show command to verify the existence of the default and static routes.
XXX>show router route-table
↵
How many routes are there in the P/PE router’s routing table? _______
Explain?
_____________________________________________________________________
_____________________________________________________________________
4. Once everyone has completed the default route configuration log on to the CE router
and ping and traceroute the various system interfaces of the various routers within the
network. Log into the P and PE router and try to ping the configured host address on
both the CE routers in the ISP
XXX>ping xxx.xxx.xxx.xxx
↵
Which devices were reachable? _______________________________
Which devices were not reachable? ______________________________
22
XXX>traceroute xxx.xxx.xxx.xxx
↵
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
What path is being taken to the other CE within your local ISP?
____________________________________________________________________
5. Shut down the link directly between the PE devices.
XXX>configure port X/Y/Z shutdown
↵
Which devices are still reachable? _______________________________
23
Explain?
_____________________________________________________________________
_____________________________________________________________________
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
Section 3.3 – IP Filters
Objective:
In this exercise the student will configure an IP filter on the routers to block ICMP echo-
request access to an IP address range.
To configure an IP filter, we must first determine the address and protocol types that we
will be allowing access to, and the direction where the filter will be applied. In this case,
we will be blocking access to any of the CE customer host addresses from the protocol
ICMP (IP Protocol type 1). We will block access in the INGRESS direction on the CE
interface towards the PE.
CE Routers Only:
6. Create and describe the filter ip instance on the CE device
XXX> configure filter ip-filter 77 create
↵
XXX>config>filter>ip-filter$ description “Block ICMP to Customer
network”
↵
7. Set the default-action to forward
XXX>config>filter>ip-filter$ default-action forward
↵
8. Deny access to all host address range only for ICMP echo-requests. Note: We will
match in the ingress direction.
XXX>config>filter>ip-filter$ entry 10 create
↵
XXX>config>filter>ip-filter>entry$ match dst-ip xx.xx.xx.xx/yy
↵
XXX>config>filter>ip-filter>entry$ match protocol 1 icmp-type echo-
request
↵
XXX>config>filter>ip-filter>entry$ action drop
↵
XXX>config>filter>ip-filter>entry$ exit all
↵
9. From the PE, ping the attached CE’s configured loopback host IP address.
Successful? _____
Explain:
_____________________________________________________________________
_____________________________________________________________________
10. Apply the filter on the CE to the router interface connected to the PE device
XXX> configure router interface toPEx
↵
24
XXX
>config>router>if$ ingress filter ip 77
↵
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
11. From the PE, ping the attached CE’s configured host loopback address. Successful?
_____
12. From the CE, ping the attached PE’s system IP addresses. Successful? _____
Explain:
_____________________________________________________________________
_____________________________________________________________________
PE Routers only: Do not start until CE Router section is completed.
13. Create and describe the filter ip instance on the PE device
XXX> configure filter ip-filter 77 create
↵
XXX>config>filter>ip-filter$ description “Block ICMP to System
Address”
↵
14. Set the default-action to forward
XXX>config>filter>ip-filter$ default-action forward
↵
15. Deny access to the system IP address only for ICMP echo-requests. Note: We will
match in the ingress direction, so the packets will destined to the system IP address.
XXX>config>filter>ip-filter$ entry 10 create
↵
XXX>config>filter>ip-filter>entry$ match dst-ip xx.xx.xx.xx/yy
↵
XXX>config>filter>ip-filter>entry$ match protocol 1 icmp-type echo-
request
↵
XXX>config>filter>ip-filter>entry$ action drop
↵
XXX>config>filter>ip-filter>entry$ exit all
↵
16. Apply the filter to the router interface connected to the CE device
XXX>configure router interface toCEx
↵
XXX>ingress filter ip 77
↵
17. From the PE, ping the attached CE’s loopback host IP address. Successful? _____
25
18. From the CE, ping the attached PE’s system IP address. Successful? _____
Explain:
_____________________________________________________________________
_____________________________________________________________________
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
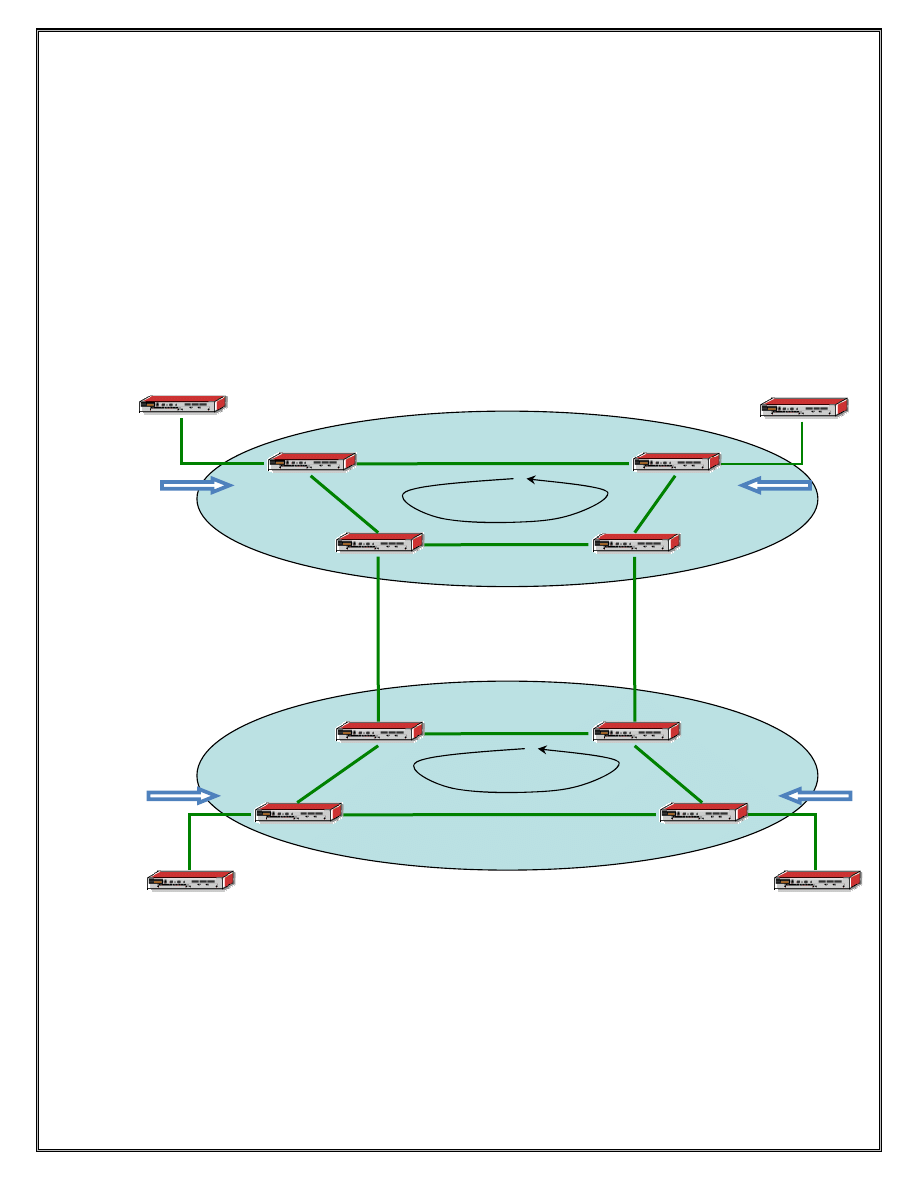
Lab 4 Open Shortest Path First (OSPF)
Section 4.1 – Single Area OSPF
Objective:
In this exercise the student will configure a single area OSPF network for each ISP. This
lab will demonstrate the different databases that are created by the OSPF routing
protocol.
CE4/R12
Figure 4 OSPF in each ISP
NOTE: Remove all static routes configured in the P and PE devices in the previous
labs. DO NOT remove the static routes to CE networks on the PE.
26
ISP 1
ISP 2
P1/R1
P2/R2
P3/R3
P4/R4
PE2/R6
PE3/R7
PE1/R5
PE4/R8
CE1/R9
CE3/R11
CE2/R10
OSPF
OSPF
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
1. The first step is to enable the OSPF routing process on the router
XXX#
configure router ospf
↵
2. Next define the area that the interfaces will be placed in. Remember that the area
must match between routers connected on the same interface for OSPF to establish an
adjacency. The objective of this exercise is to configure a single area OSPF network;
therefore, all students should use the same area number.
XXX#>config>router>ospf$
area 0
↵
3. Now enter into this area all the interfaces that you want OSPF to operate on and send
out its advertisements. In this case, place all the PE and P router interfaces inside the
local ISP into the OSPF process area 0. Note that ISPs rarely exchange routes with
each other using an IGP protocol of any sort.
XXX#>config>router>ospf>area$
interface system
↵
XXX#>config>router>ospf>area>if$
exit
↵
XXX>config>router>ospf>area> interface toPE1
XXX>config>router>ospf>area>if$
interface-type point-to-point
↵
Continue until all the interfaces on the PE and P routers, within the ISP, are entered
into the OSPF process in area 0.
XXX>show router route-table
↵
a.
How many routes in the table? ________
b.
What is the preference and metric value of each OSPF Route?
_________________________________________________________________
_________________________________________________________________
_________________________________________________________________
_________________________________________________________________
4. Use the show command to look at the OSPF neighbors of the P routers.
XXX>show router ospf neighbor
↵
a. How many neighbors do you see on the P devices? _____ PE? _____ CE? _____
b. What is the state of their adjacency? ____ Why?
____________________________________________________________________
____________________________________________________________________
Use the following command to show the ospf link state database. This database is a
listing of all LSAs that have been received by the router. It is these LSAs that the SPF
algorithm uses to create the forwarding table.
XXX#
show router ospf database detail
↵
27
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
a. What types of LSAs are in the database?
_______________________________________________________________
_______________________________________________________________
b. Is the database consistent on all the ISP routers? _______
5. Once everyone has completed the OSPF configuration login to the P router and ping
the other PE router system interfaces.
XXX>ping xxx.xxx.xxx.xxx
↵
Which devices were reachable? _______________________________
Which devices were not reachable? ______________________________
Explain?
_____________________________________________________________________
___________________________________________________________________
6. To reach the CE networks from any of the PE and P routers, the CE networks need to
be distributed into OSPF running on PE and P routers. The static routes to the CE
networks are defined on the PE routers and need to be distributed on the PE routers.
To do this:
a. the PE router must be configured as an ASBR (Autonomous System Border
Router). The ASBR configuration under OSPF enables a router running the OSPF
routing protocol to distribute networks external to the OSPF domain into OSPF.
In this case the static routes to the CE networks are not part of the ISP OSPF
domain.
On the PE router
XXX#>config>router>ospf#
asbr
↵
b. A routing policy on the PE distributes the static routes into OSPF
On the PE router
XXX# configure router policy-options
↵
XXX>config>router>policy-options# begin
↵
XXX>config>router>policy-options# policy-statement Export_Routes
↵
XXX>config>router>policy-options>policy-statement$ entry 10
↵
XXX>config>router>policy-options>policy-statement>entry$
from protocol static
↵
XXX>config>router>policy-options>policy-statement>entry#
action accept
↵
XXX>config>router>policy-options>policy-statement>entry>action#
back
↵
XXX>config>router>policy-options>policy-statement>entry# back
↵
XXX>config>router>policy-options>policy-statement# back
↵
XXX>config>router>policy-options# commit
↵
XXX>config>router>policy-options# exit all
↵
XXX>config>router>ospf# export Export_Routes
28
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
7. From the PE and the P routers, ping all the CE networks (i.e. ping the CE host
loopback address) within the ISP
Which devices were reachable? _______________________________
Which devices were not reachable? ______________________________
Explain?
_____________________________________________________________________
___________________________________________________________________
29
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
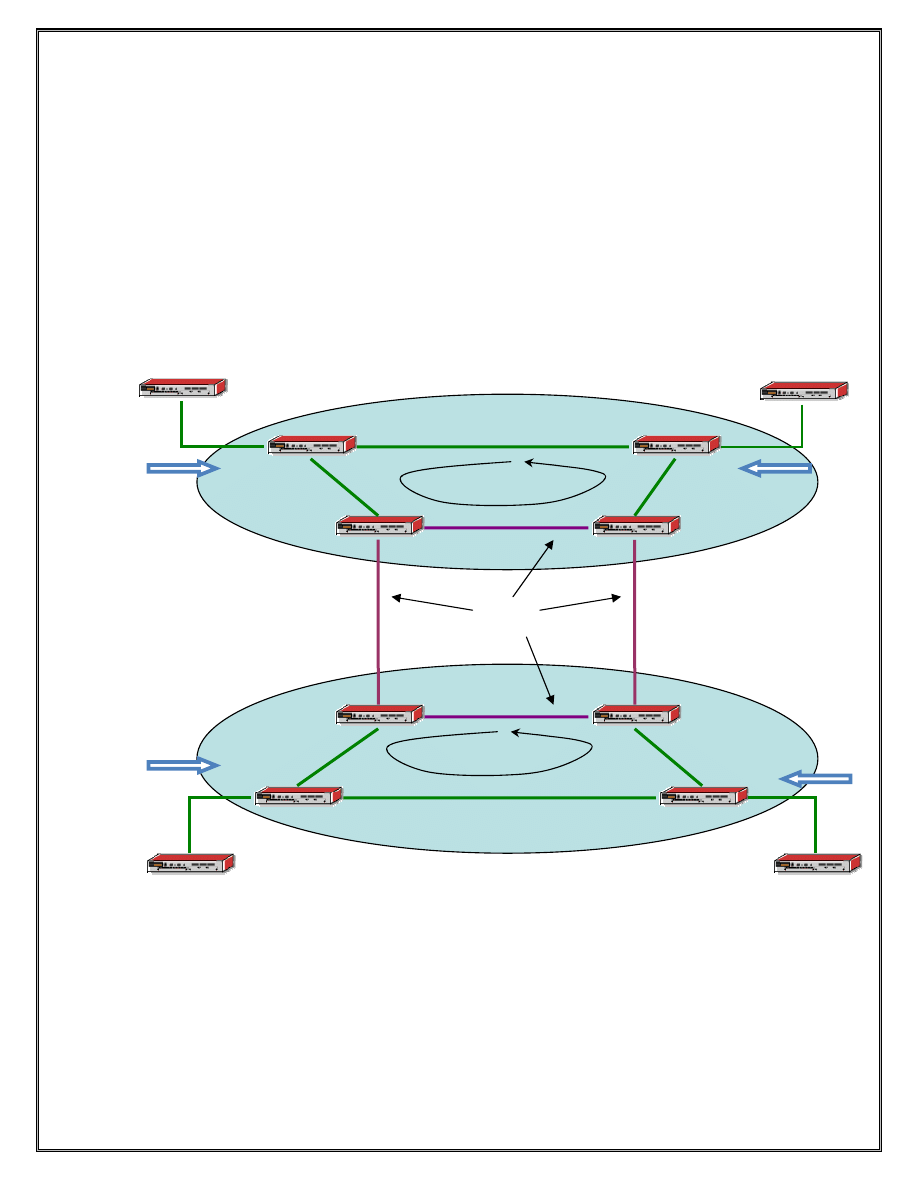
Lab 5 BGP Routing
Section 5.1 – BGP Routing
Objective:
In this exercise the student will configure their ISP as a BGP Autonomous System. The
student will then configure the BGP routing protocol to connect the Autonomous Systems
together and exchange routing information.
CE4/R12
Figure 5 BGP between ISPs and within ISPs
30
ISP 1
ISP 2
P1/R1
P2/R2
P3/R3
P4/R4
PE2/R6
PE3/R7
PE1/R5
PE4/R8
CE1/R9
CE3/R11
CE2/R10
OSPF
OSPF
BGP
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
1. Assign your AS number to your P and PE routers (R1-R8).
XXX#>config>router# autonomous-system 6500n
(n = ISP#)
↵
2. P1 and P3, P2 and P4 will be configured as external BGP peers (eBGP). Note that
eBGP peers typically use the next-hop interface IP address as the neighbor address.
Since the ISPs will now be peering (share an IP network) between them, assign the
link between P1 and P3 host addresses from 145.0.0.10/31 and the link between P2
and P4 will be assigned hosts from the 145.0.0.20/31 network.
XXX#>config>router# bgp group eBGP
↵
XXX#>config>router>bgp>group$ neighbor xx.xx.xx.xx
↵
XXX#>config>router>bgp>group>neighbor$ peer-as <remote AS>
↵
3.
P1 and P2, P3 and P4 will be configured as internal BGP peers (iBGP). Note that
iBGP peers typically use the system interface IP address as the neighbor address.
XXX#>config>router# bgp group iBGP
↵
XXX#>config>router>bgp>group$ neighbor xx.xx.xx.xx
↵
XXX#>config>router>bgp>group>neighbor$ peer-as <local AS>
↵
4.
At this point, each P router should have one internal and one external BGP session.
xxx# show router bgp summary
↵
5.
We can see the advertised routes for reach neighbor using the following command.
xxx# show router bgp neighbor xx.xx.xx.xx advertised-routes
↵
a. How many routes are advertised to each neighbor? _____
b. Explain
____________________________________________________________
__________________________________________________________
6.
BGP, like other distance vector protocols, requires an export policy to advertise-
routes to other BGP peers. The most accepted way to originate a route from an ISP is
to create a black-hole static route for all aggregates to be advertised. This will ensure
these routes always exit to eliminate IGP related route flapping. Create the black-hole
static route for the aggregate of your local ISP. A black hole indicates that traffic for
a particular route will be discarded unless a more specific route exists in the routing
table. A black hole static-route only makes sense from an aggregation view point. For
e.g if there are the following routes in the routing table
XXX# configure router static-route xx.xx.xx.xx/yy black-hole
preference 250
↵
31
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
8.
Execute the following set of commands on the core routers (R1-R4). This will export
all static routes to the eBGP peers.
XXX# configure router policy-options
↵
XXX>config>router>policy-options# begin
↵
XXX>config>router>policy-options# policy-statement Export_Routes
↵
XXX>config>router>policy-options>policy-statement$ entry 10
↵
XXX>config>router>policy-options>policy-statement>entry$
from protocol static
↵
XXX>config>router>policy-options>policy-statement>entry#
action accept
↵
XXX>config>router>policy-options>policy-statement>entry>action#
back
↵
XXX>config>router>policy-options>policy-statement>entry# back
↵
XXX>config>router>policy-options>policy-statement# back
↵
XXX>config>router>policy-options# commit
↵
XXX>config>router>policy-options# exit all
↵
XXX#configure router bgp group eBGP
↵
XXX#>config>router>bgp>group$ export Export_Routes
↵
NOTE: Wait for all nodes to be fully configured before proceeding.
7.
Notice that there are routes being advertised now that the policy is applied.
xxx# show router bgp neighbor xx.xx.xx.xx advertised-routes
↵
How many routes are in the routing table of R1-R4? ________________
Explain?
_____________________________________________________________________
___________________________________________________________________
9. Log on to the PE routers and ping the other P router system interfaces of the other ISP
XXX>ping xxx.xxx.xxx.xxx
↵
Which devices were reachable? _______________________________
Which devices were not reachable? ______________________________
Explain?
_____________________________________________________________________
___________________________________________________________________
32
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
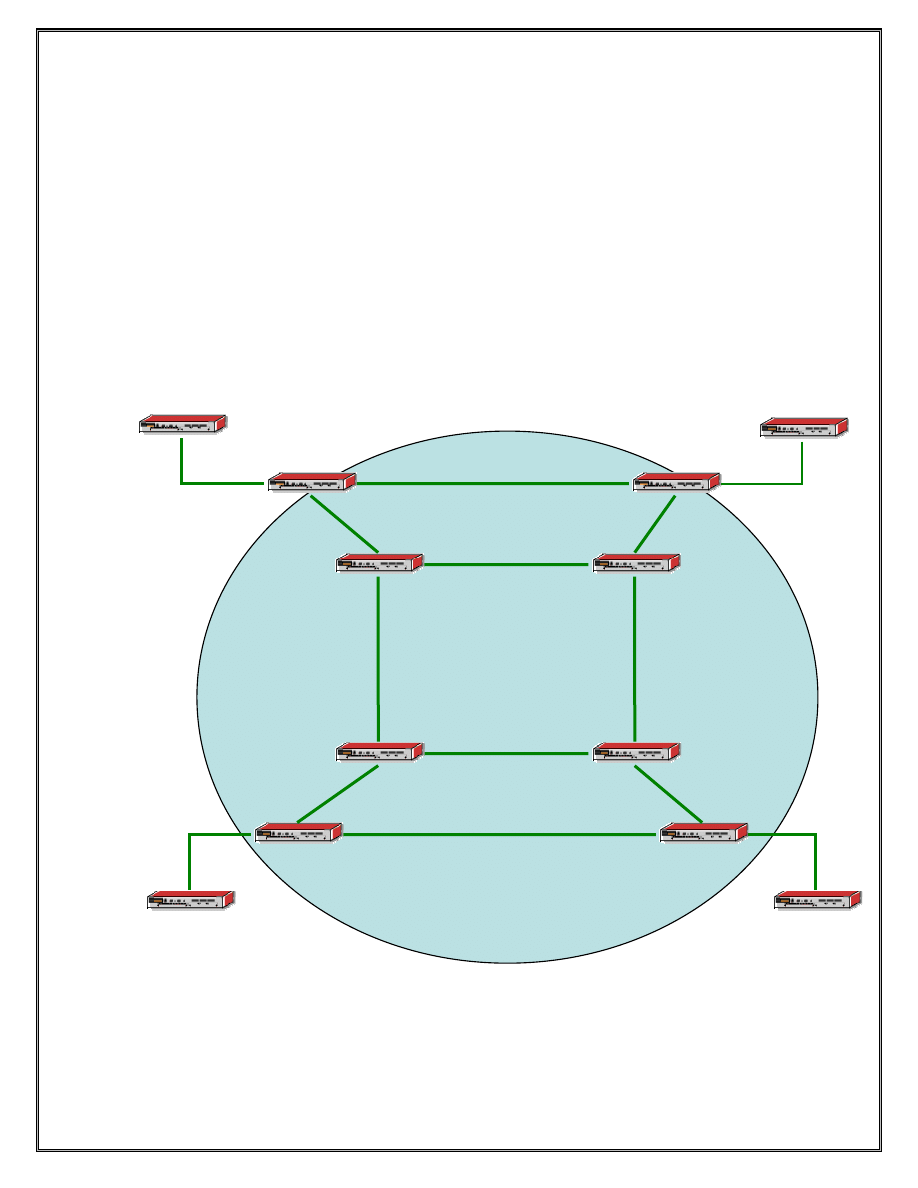
Lab 6 Services
Section 6.1: Services Framework
Objective:
In order to complete the next group of labs, we need to create a topology to support the
services we will deploy. The two service providers from the previous sections have
merged into one and are offering a VPLS service across their network. As long as routes
exist to the system addresses of all the PE devices in the provider network, a VPLS
service can be created. The new service provider is running OSPF as the IGP for their
core network.
CE4/R12
Figure 6 Service Provider core network
33
P1/R1
P2/R2
P3/R3
P4/R4
PE2/R6
PE3/R7
PE1/R5
PE4/R8
CE1/R9
CE3/R11
CE2/R10
OSPF
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
Running an IP/MPLS-based service requires a Label Distribution Protocol (we’ll use
LDP for ease of deployment) and a full mesh of Service Distribution Paths (SDPs).
Follow the steps below.
Reference Terminology:
R1-R4 = Provider Routers = P1-P4
R5-R8 = Provider Edge Routers = PE1-PE4
R9-R12 = Customer Edge Routers = CE1-CE4
Part 1: Provider Router Configuration (P1-P4)
1) In the previous lab, routing between ISPs is provided by BGP. Since the ISPs have
merged, they will be merged into one routing domain, running OSPF as their IGP.
The interfaces between R1 and R3 and between R2 and R4 must be added to OSPF to
make this a single routing domain.
2) The MPLS signaling protocol that will be used in the following section is LDP. LDP
must be enabled on ALL interfaces that will be required to perform MPLS Label
exchange.
XXX#>configure router ldp interface-parameters interface toP_
↵
XXX#>config>router>ldp>if-params>if$
exit
↵
XXX#>configure router ldp no shut
↵
Where toP_ is the router interface to all neighboring routers
Part 2: Provider Edge Router Configuration (PE1-PE4)
1) LDP must be enabled on ALL router interfaces in the provider core to allow labels to
be exchanged across the Provider and Provider Edge routers.
XXX#>configure router ldp interface-parameters interface toP_
↵
XXX#>config>router>ldp>if-params>if$ exit
↵
XXX#>configure router ldp no shut
↵
Where toR_ is the router interface to the P and PE routers only
LDP is an MPLS signaling protocol; therefore once all routers in the network have been
correctly configured for LDP, LSPs will be created dynamically based on the system
addresses of each node in the network.
34
3) Configure a full mesh of SDPs (Service Distribution Paths) between the PE routers
only. This will allow the distribution of services across all PE routers in the networks.
When you’ve completed this section, each PE node will have a total of 3 SDPs to
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
each of the other 3 PEs. The SDP is identified by an integer and we will use the router
number (5, 6, 7 or 8) of the far end PE to identify the SDP. So, PE1 (R5) will have 3
SDPs numbered 6, 7 and 8 to each of the other three PEs.
XXX#>configure service sdp x mpls create
↵
XXX#>config>service>sdp$ far-end xxx.xxx.xxx.xxx
↵
XXX#>config>service>sdp$ ldp
↵
XXX#>config>service>sdp$ no shutdown
↵
Where x is the router number of the destination node
Where xxx.xxx.xxx.xxx is the system IP address of the far-end device
Part 3: Customer Edge Router Configuration (CE1-CE4)
In the following service labs, the Customer Edge devices will be configured as traditional
routers. Each CE router has an interface in the same IP subnet. The VPLS service will
join these four routers in the same way an Ethernet switch would join them. The
following configuration is required on each CE device
1) Create the router interface on the interface connecting the CE to the service enabled
PE devices.
XXX#>configure router interface servicesCE_
↵
XXX#>config>router>if$ address 192.168.1.x/24
↵
XXX#>config>router>if$ port X/Y/Z
↵
XXX#>config>router>if$ no shutdown
Where x is the local router number
Where X/Y/Z is the physical network port connecting the CE to the neighboring
PE.
2) Create OSPF area 0 and add the Router Interface created in step 1, and the system
interface to it. .
XXX#>configure router ospf area 0
↵
XXX#>config>router>ospf>area$ interface system
↵
XXX#>config>router>ospf>area>if$ back
↵
XXX#>config>router>ospf>area# interface serviceCE1
↵
XXX#>config>router>ospf>area>if$ back
↵
Part 4: Verification
NOTE: Wait till your peer nodes are also at this step before proceeding.
35
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
1) LDP is the protocol used for signaling which tunnel labels will be PUSHed,
SWAPped, POPped while data traverses the LSP. To view which labels will be used,
and their function use the following command
XXX# show router ldp bindings active.
↵
a. How many PUSH actions on the P, PE, and CE devices?
_______________________ Explain?
_______________________________________________________________
_______________________________________________________________
__________
b. How many SWAP actions on the P, PE, and CE devices?
_______________________ Explain?
_______________________________________________________________
_______________________________________________________________
__________
c. How many POP actions on the P, PE, and CE devices?
_________________________ Explain?
_______________________________________________________________
_______________________________________________________________
__________
2) CE Connectivity:
a. How many OSPF adjacencies are there on your CE device? _____
b. Ping the other CE devices in the network (ping 192.168.1.x).
Explain the results?
________________________________________________________________________
________________________________________________________________________
36
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
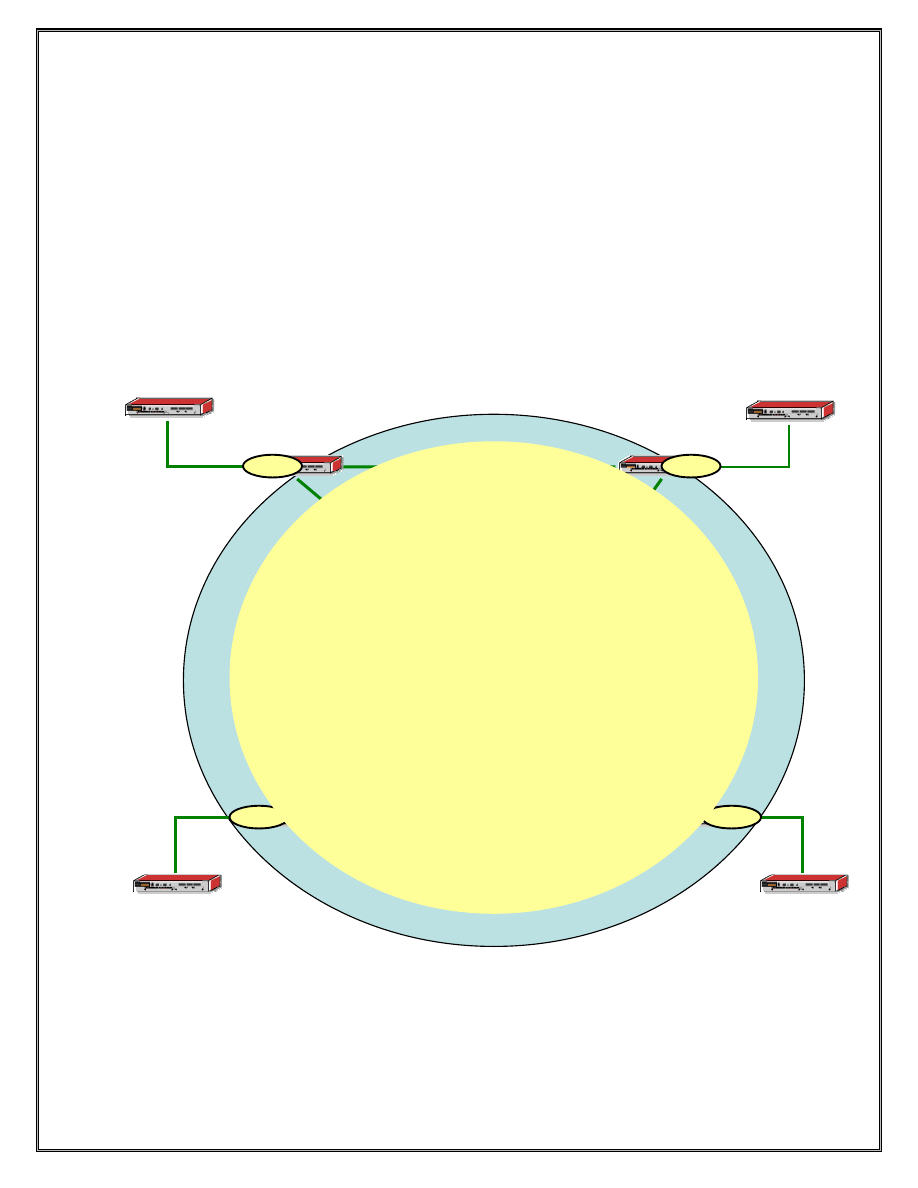
Section 6.2: VPLS Example
Objective:
A VPLS is a layer 2 service that can connect multiple sites in one LAN. It’s like creating
a virtual Switch out of a network of Service Routers. In this lab, we will create a VPLS
across all the PE nodes. The PE devices will connect to each other with a full mesh using
mesh-sdp. Note that after the service reference topology has been configured, adding
services from edge to edge does not require any further modification of the P devices.
CE4/R12
Figure 6 VPLS service in each ISP between PE and P routers with SAP connections to CE routers
Part 1: Provider Edge Router Configuration (R5-R8)
1) Create the VPLS service.
37
P1/R1
P2/R2
P3/R3
P4/R4
PE2/R6
PE3/R7
PE1/R5
PE4/R8
CE1/R9
CE3/R11
CE2/R10
SAP
SAP
SAP
SAP
VPLS 1
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
XXX#>configure service vpls 1 customer 1 create
↵
XXX#>config>service>vpls$ no shutdown
↵
2) SDPs are used to distribute services across multiple service routers, and therefore,
bind a transport tunnel to the service. You will need to create a mesh-sdp between
each PE router (R5-R8) to allow full communication across the PE routers. Each PE
router should have 3 mesh-SDPs at the conclusion of this step. Note that a mesh-sdp
will not forward a frame out another mesh-sdp, allowing for a loop free service
topology within the core.
XXX#>configure service vpls 1 mesh-sdp x create
↵
XXX#>config>service>vpls>mesh-sdp$ back
↵
Where x is the sdp # to the other PE routers. (R5=5, R6=6. R7=7, R8=8)
3) Service Access Points are used to attach CE devices to services on PE devices.
XXX#>configure service vpls 1 sap X/Y/Z create
↵
Where X/Y/Z is the physical port connecting the CE device to the PE
a. Were you successful at adding the SAP? _______
b. Explain?
_______________________________________________________________
_______________________________________________________________
c. Correct the problem.
XXX#>configure port X/Y/Z shutdown
↵
XXX#>configure port X/Y/Z ethernet mode access
↵
XXX#>configure port X/Y/X no shutdown
↵
Part2: Verification
NOTE: Wait till your peer nodes are also at this step before proceeding.
a. View the in-use Service LDP bindings on the P and PE routers. (U after label
indicates in-use)
XXX# show router ldp bindings fec-type services.
↵
38
a. How many Ingress Labels on PE? ___ P ___ Why?
_______________________________________________________________
_______________________________________________________________
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
b. How many Egress Labels on PE? ___ P ___ ? Why?
_______________________________________________________________
_______________________________________________________________
b. Network Connectivity:
a. How many OSPF adjacencies are there on your CE device? _____
b. Are you able to ping the other CE devices in the lab? _____
c. Are you able to ping the system IP address of the P device from the CE
device? ____
d. Explain the results?
_______________________________________________________________
_______________________________________________________________
c.
Services: Use the following command to determine the health of your services.
XXX#> show service service-using
↵
a. How many services are there on each device in your POD? ______
b. What is their status? ______
c. Use the following command to find out more information about your service:
XXX#> show service id 1 base
↵
d. On each PE device, we can see the MAC database per service using the
following command.
XXX#> show service id 1 fdb detail
↵
i.
How many local MAC addresses are in your table? ____
ii.
How many remote MAC addresses are in your table? ____
e. On the PE devices (R5-R8), shutdown the SDP to the PE device in the
clockwise direction from you.
XXX#>configure service sdp x shutdown
↵
Where x is the SDP to the remote PE device (R5=5, R6=6, R7=7, R8=8)
i. How many OSPF adjacencies are there on your CE device? _____
39
ii. Ping the system IP addresses of all other CE devices in the lab.
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
iii. Explain the results?
_________________________________________________________
_________________________________________________________
f. On the P routers, observe the impact of step d.
XXX#>show router ldp bindings active
↵
i. How many labels are there? _____________
ii. Is there any difference compared to what was seen in previously in
step a? ________________
40
Explain.
__________________________________________________________________
__________________________________________________________________
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
Solutions
Exercise 1.3: Hardware
Sample Relevant Config
#--------------------------------------------------
echo "Card Configuration"
#--------------------------------------------------
card 1
card-type iom-20g
mda 1
mda-type m60-10/100eth-tx
ingress
mcast-path-management
shutdown
exit
exit
exit
exit
#--------------------------------------------------
Exercise 1.4: Logs
Sample Relevant Config
#--------------------------------------------------
echo "Log Configuration"
#--------------------------------------------------
log
log-id 21
description "Main stream log"
from main
to memory
exit
log-id 22
description "Security Log File"
from security
to memory
exit
log-id 23
description "Debug-trace"
from debug-trace
to memory
exit
log-id 24
description "Change Log"
from change
to memory
exit
exit
41
Exercise 2.1
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
Divide up the ISP address space into equal space 512 host addresses
138.120.16.0/22
138.120.20.0/22
138.120.24.0/22
138.120.28.0/22 - divide into 138.120.28.0/23 and 138.120.30.0/23
Take the last 138.120.30.0/23 and divide that into
138.120.30.0/27
A.1 30 hosts
138.120.30.32/27 A.2 62
hosts
138.120.30.64/27
138.120.30.96/27 B.1 92
hosts
138.120.30.128/26
138.120.30.192/26 B.2 316
hosts
138.120.31.0/24
Exercise 2.2
Divide 140.10.0.0/24 into 8/27 address spaces
140.10.0.0/27
Reserved
Reserved
140.10.0.32/27
Unused
140.10.0.64/27
Unused
140.10.0.96/27 Split
140.10.0.96/30
140.10.0.100/30
140.10.0.104/30
140.10.0.108/30
140.10.0.112/30
140.10.0.116/30
140.10.0.120/30
140.10.0.124/30
All interface addresses
140.10.0.128/27 Aggregate
140.10.0.128/26
Assigned to Customer
space
140.10.0.160/27
140.10.0.192/27 Aggregate
140.10.0.192/26
Assigned to customer
space
140.10.0.224/27
42
Exercise 2.3
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
5. Is there a difference between the outputs of the ‘show router interface’ command
and the ‘show router route-table’ command? What is the difference?
Yes there is a difference. The route table shows me the networks that are connected to my
router and the logical interface it is connected to. The router interface command shows
me the host address assigned to the port from the network that is used on my router along
with the physical port it is bound to.
Relevant Configuration from P1
#--------------------------------------------------
echo "Router (Network Side) Configuration"
#--------------------------------------------------
router
interface "system"
address 140.10.0.1/32
exit
interface "t-R2"
exit
interface "to-R2"
address 140.10.0.5/30
port 1/1/2
exit
interface "to-R3"
address 140.10.0.109/30
port 1/1/3
exit
interface "to-R5"
address 140.10.0.118/30
port 1/1/1
exit
exit
Exercise 2.4
4. How many ARP entries are on each router at this point?
There are no ARP entries in my ARP table at this point. The routers do not know how to
reach the system addresses of other routers so no ARP responses are received.
5. How many ARP entries are on each router at this point?
I see entries for each of my directly connected peers. The MAC address belongs to the
remote router’s interface. ARP entries are populated because all routers know of their
directly connected networks and will respond to ARP requests accordingly.
Exercise 3.1
43
5. View the contents of the routing table and answer the following questions.
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
a. How many routes in the table?
There are routes for all my connected networks and an additional STATIC route
for each entry I put in.
b. What is the preference and metric value of each type of routing entry?
The LOCAL entries have a Metric and Preference of 0
The Static Routes have a Metric of 1 and a Preference of 5.
Exercise 3.2
3 How many routes are there in the P/PE router’s routing table?
Even though I entered 4 static routes total on the router, only 2 are active in my
routing table. The router preferred the static-route with the lowest metric.
4. Which devices were reachable?
I was able to ping the CE routers
Which devices were not reachable?
I was unable to ping the System addresses of routers 2 hops away as they do not have
routes to the remote CE system address in their table. The directly attached PE router
has a static
route to the local CE system address from a previous step.
What is the PATH to the other CE within your local ISP?
CE Æ PE Æ PE Æ CE
5. Shut down the link directly between the PE devices.
Which Devices are still reachable?
I am still able to PING the other CE in my ISP by using the alternate (floating) static-
route that replaced the last route. Once a interface goes operationally down, routers
flush routes from their routing table that use it as their next-hop.
Exercise 3.3
9.
From the PE, ping the attached CE’s configured loopback host IP address.
44
Successful?
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
YES. While the filter is created, it is not applied to any interface yet
11. From the PE, ping the attached CE’s configured host loopback address?
Successful?
YES
12. From the CE, ping the attached PE’s system IP addresses.
Successful?
NO. The filter is blocking icmp echo-requests in only one direction therefore ping
works one way, but not the other.
17. From the PE, ping the attached CE’s loopback host IP address.
Successful?
YES. ICMP echo-requests are not blocked to the Loopback segment, ONLY the
system IP.
18. From the CE, ping the attached PE’s system IP address.
Successful?
NO. The filter is now blocking ICMP echo-requests to both CE and PE system
addresses.
Sample PE Relevant Config
#--------------------------------------------------
echo "Filter Configuration"
#--------------------------------------------------
filter
ip-filter 77 create
default-action forward
description "Block ICMP to System Address"
entry 10 create
match protocol icmp
dst-ip 151.10.0.30/32
icmp-type echo-request
exit
action drop
exit
exit
exit
#--------------------------------------------------
echo "Router (Network Side) Configuration"
#--------------------------------------------------
interface "to-R12"
address 151.10.0.126/30
port 1/1/2
ingress filter ip 77
exit
45
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
Sample CE Relevant Config
#--------------------------------------------------
echo "Filter Configuration"
#--------------------------------------------------
filter
ip-filter 77 create
default-action forward
description "Block ICMP to System Addy"
entry 10 create
match protocol icmp
dst-ip 151.10.0.31/32
icmp-type echo-request
exit
action drop
exit
exit
exit
#--------------------------------------------------
echo "Router (Network Side) Configuration"
#--------------------------------------------------
interface "to-R8"
address 151.10.0.125/30
port 1/1/2
ingress filter ip 77
exit
Exercise 4.1
3 .
c. How many routes in the table?
There are 5 OSPF routes in my routing table. 3 System Addresses and 2 Inteface
networks that are not directly connected to my local system
d. What is the preference and metric value of each OSPF Route?
The OSPF routes vary in metric depending how “far” away they are (OSPF uses
cumulative cost based on bandwidth), but all have a preference of 10.
4.
c. How many neighbors do you see on the P devices? 2
PE? 2
CE? 0
d. What is the state of their adjacency?
The P and PE adjacencies are Established because there is a OSPF speaker on the
other end with the proper parameters configured.
There is no OSPF adjacency to the CE router listed as none was configured
46
e. What type of LSAs are in the database?
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
Only Type 1 Router LSA are present due to the interface being configured as point-
to-point
5. Which devices were reachable?
All the devices in the local ISP were now reachable.
Which devices were not reachable?
The devices in the remote ISP were not reachable because there is no routing protocol
between the 2 ISPs. Also, none of the CE Host Networks were reachable as the
routers did not have routes for these networks in their local routing table.
6. Which devices were reachable?
All networks and devices in the local ISP are now reachable.
Which devices were not reachable?
Devices in the remote ISP were not reachable because there is no routing protocol
between the 2 ISPs.
Sample Relevant Config
#--------------------------------------------------
echo "OSPFv2 Configuration"
#--------------------------------------------------
ospf
area 0.0.0.0
interface "system"
interface-type point-to-point
exit
interface "to-R4"
interface-type point-to-point
exit
interface "toLAN"
interface-type point-to-point
exit
exit
exit
exit
Exercise 5.1
5. How many routes are advertised to each neighbor?
47
There are no routes advertised to the neighbors because BGP does not originate
routes until an export policy is created and applied to the BGP instance.
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
8. How many routes are in the routing table of R1-R4?
There is 1 BGP route in each of R1-R4s routing tables, matching the best path to
the aggregate advertised by the remote ISPs.
9. Which devices were reachable?
From the PE routers, only the P routers in the local ISP were reachable
Which devices were not reachable?
All routers in the remote ISP were still unreachable. This is due to the local PE router
not participating in the BGP routing protocol and therefore it is not aware of the
aggregate route advertised from P to P router.
Sample Relevant Router Config
#--------------------------------------------------
echo "Static Route Configuration"
#--------------------------------------------------
static-route 140.10.0.0/24 black-hole
#--------------------------------------------------
echo "Policy Configuration"
#--------------------------------------------------
policy-options
begin
policy-statement "Export_Routes"
entry 10
from
protocol static
exit
action accept
exit
exit
exit
commit
exit
#--------------------------------------------------
echo "BGP Configuration"
#--------------------------------------------------
bgp
group "eBGP"
export "Export_Routes"
exit
group "ebgp"
neighbor 160.10.0.6
peer-as 65002
exit
exit
group "ibgp"
48
neighbor 140.10.0.2
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
peer-as 65001
exit
exit
exit
exit
Exercise 6.1
Part 4: Verification
1.
a. How many PUSH actions on the P, PE, and CE devices?
There are 7 PUSH operations on each P and PE device. There are no PUSH
operations on the CE as it is not running LDP
b. How many SWAP actions on the P, PE, and CE devices?
There are 7 SWAP operations on each P and PE device. There are no SWAP
operations on the CE as it is not running LDP
c. How many POP actions on the P, PE, and CE devices?
There is 1 POP operation on each P and PE device. There are no POP operations
on the CE device as it is not running LDP.
2.
a. How many OSPF adjacencies are there on your CE device?
None
b. Ping the other CE devices in the network (ping 192.168.1.x).
Nothing is reachable because there is no layer 2 connectivity from CE to CE
device without creating a service.
Exercise 6.2
3. Were you successful at adding the SAP?
No. The port must be in access mode before you can create a SAP on it.
Part 2: Verification
1.
g. How many Ingress labels?
49
There are now 3 Ingress labels on the PE devices. The P and CE device has no
service labels.
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
h. How many SWAP actions?
There are now 3 Egress labels on the PE devices. The P and CE device has no
service labels.
2.
a. How many OSPF adjacencies are there on your CE device?
3
b. Are you able to ping the other CE devices in the lab?
YES
c. Are you able to ping the system IP address of the P device from the CE
device?
NO. The O and PE devices are private from the service to which the CE
devices are connected on.
3.
a. How many services are there on each device in your POD?
1 per PE only
b. What is their status?
Operationally UP
d. On each PE device, we can see the MAC database per service using the
following command.
iii.
How many local MAC addresses are in your table?
1
iv.
How many remote MAC addresses are in your table?
3
e. On the PE devices (R5-R8), shutdown the SDP to the PE device in the
clockwise direction from you.
i. How many OSPF adjacencies are there on your CE device?
1
ii. Ping the system IP addresses of all other CE devices in the lab.
Only the CE device connected to the diagonally connected PE is
reachable because it is the only one with an active SDP in both
directions.
f.
i. How many labels are there?
50
Same as before
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
ii. Is there any difference compared to what was seen in previously
in step a?
NO. The LSPs created with LDP are still active, only the SDP used
to bind the LSPs to the service are shut down therefore no labels
will be withdrawn.
Sample PE Relevant Configuration
#--------------------------------------------------
echo "LDP Configuration"
#--------------------------------------------------
ldp
interface-parameters
interface "to-R1"
exit
interface "to-R6"
exit
interface "to-R5"
exit
exit
targeted-session
exit
exit
exit
#--------------------------------------------------
echo "Service Configuration"
#--------------------------------------------------
service
customer 1 create
description "Default customer"
exit
sdp 6 mpls create
far-end 140.10.0.6
ldp
keep-alive
shutdown
exit
no shutdown
exit
sdp 7 mpls create
far-end 151.10.0.1
ldp
keep-alive
shutdown
exit
no shutdown
exit
sdp 8 mpls create
far-end 151.10.0.30
ldp
keep-alive
shutdown
exit
51
no shutdown
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
exit
vpls 612 customer 1 create
stp
shutdown
exit
sap 1/1/2 create
exit
mesh-sdp 6:612 create
mesh-sdp 7:612 create
mesh-sdp 8:612 create
exit
no shutdown
exit
exit
52
Alcatel-Lucent
Confidential
for
internal
use
only
--
Do
Not
Distribute
Document Outline
- Lab 1 Hardware Configuration
- Lab 2 IP Addressing and Routing
- Lab 3 Dynamic IP Routing
- Lab 4 Open Shortest Path First (OSPF)
- Lab 5 BGP Routing
- Lab 6 Services
Wyszukiwarka
Podobne podstrony:
Adresowanie w protokole IP id 5 Nieznany (2)
hack tcp ip hns6ugel3kbdis6sfuw Nieznany
Fragmentacja datagramu IP przyk Nieznany
adresowanie w protokole ip [win Nieznany
81 ALCATEL LUCENT 1357 ULIS 2008
Alcatel Lucent Mobile Gateways for the LTE Evolved Packet Core v1 0 Lab Guide dl
Protokol TCP IP R08 5 id 834124 Nieznany
IP Maliny ed 2 id 219821 Nieznany
IP Telephony Design Guide Alcatel
Protokol TCP IP R04 5 id 834122 Nieznany
Protokol TCP IP R07 5 id 834123 Nieznany
Protokol TCP IP R08 5 id 834124 Nieznany
Adresy IP
w8 VLAN oraz IP w sieciach LAN
ADRESACJA W SIECIACJ IP
SNMP (IP)
więcej podobnych podstron