
What are Access Lists?
The increasing need for companies to share information results in more
Internet connections and the creation of more extranets. Consequently, a
higher awareness of security and bandwidth conservation is developed. Access
lists (acls) can be used to increase security by denying unwanted traffic access
to your network. They can also be used to restrict permission across a WAN link
to a defined traffic group resulting in bandwidth optimization. However, Cisco
does NOT recommend access lists as a standalone security mechanism. They
should be used to supplement normal security features.
Simply stated, access lists are a method of filtering traffic. Cisco's IOS supports
statements that can be applied to a router to control traffic. Access lists allow
you to define a specific group of traffic and apply a condition based upon the
defined traffic group. Using acls, traffic can be permitted or denied based on
this traffic grouping.
One common access list application involves filtering traffic on a router's
interface for bandwidth conservation, filtering telnet on virtual terminal lines,
configuring Dial On Demand Routing (DDR), and configuring policy based
routing using route maps to control the flow of routing updates.
Cisco's IOS supports multiple protocol type access lists. Access lists can be
configured for IP, IPX, or AppleTalk traffic. Depending upon the type of acls
used, you can filter traffic based upon protocol type, port number, source
address, destination address, and various other criteria. This lesson will focus
on the most common type of acls, ip acls.
1. Define access lists and explain how they can aid in network performance.
Access lists are a method of filtering traffic. Cisco's IOS supports statements that
can be applied to a router for the purpose of controlling traffic. Common application
of access lists include filtering traffic on a router's interface for bandwidth
conservation, filtering telnet on virtual terminal lines, configuring dial on demand
routing (DDR), and configuring policy based routing using route maps to control the
flow of routing updates.
Introduction to How Access Lists Work
Now that we understand what acls are, let's view how they work. To effectively
use acls you must fully understand how they operate. For acls to operate, you
must create the access list, and apply the access list to a router interface. As a
preparation step you should plan the list with paper and pencil and step
through a mental test of the access list to determine if it will yield the expected
results. This step is not necessary to making an operational access list, but is
critical to making it successful!
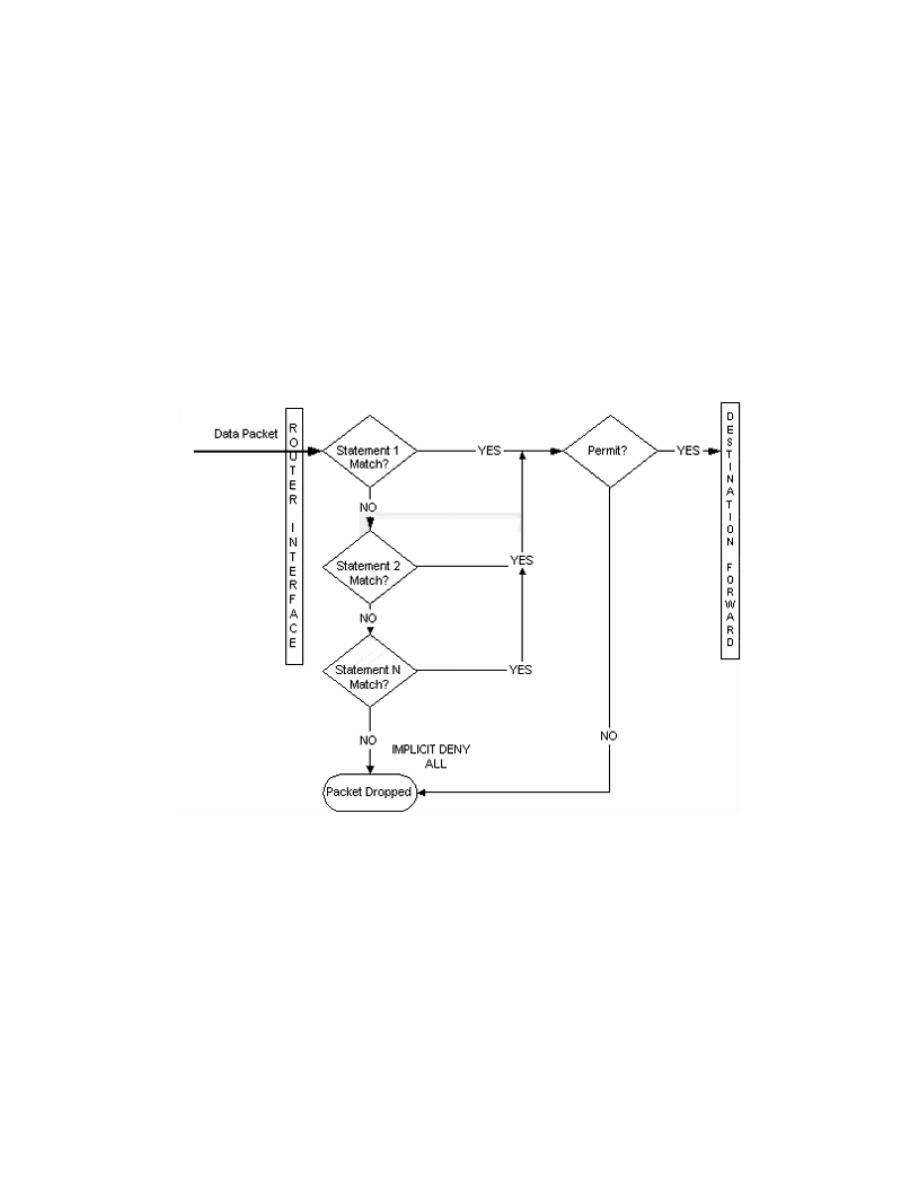
Creating Access List Statements
Access lists consists of permit and/or deny statements. These statements are
executed in a top down fashion. As traffic encounters the access list, the access
list is parsed top to bottom, looking for a match. The first match encountered
will determine if the traffic is permitted or denied. Therefore, the order of your
access list statements is extremely important. Access list should be built from
most specific to least specific. This will keep unintentional matching to a
minimum. If no match is found, there is an implicit "deny everything" at the
end of all access list statements. the figure below illustrates this process.
Top-down access list statement execution.
Applying Access Lists to Interfaces
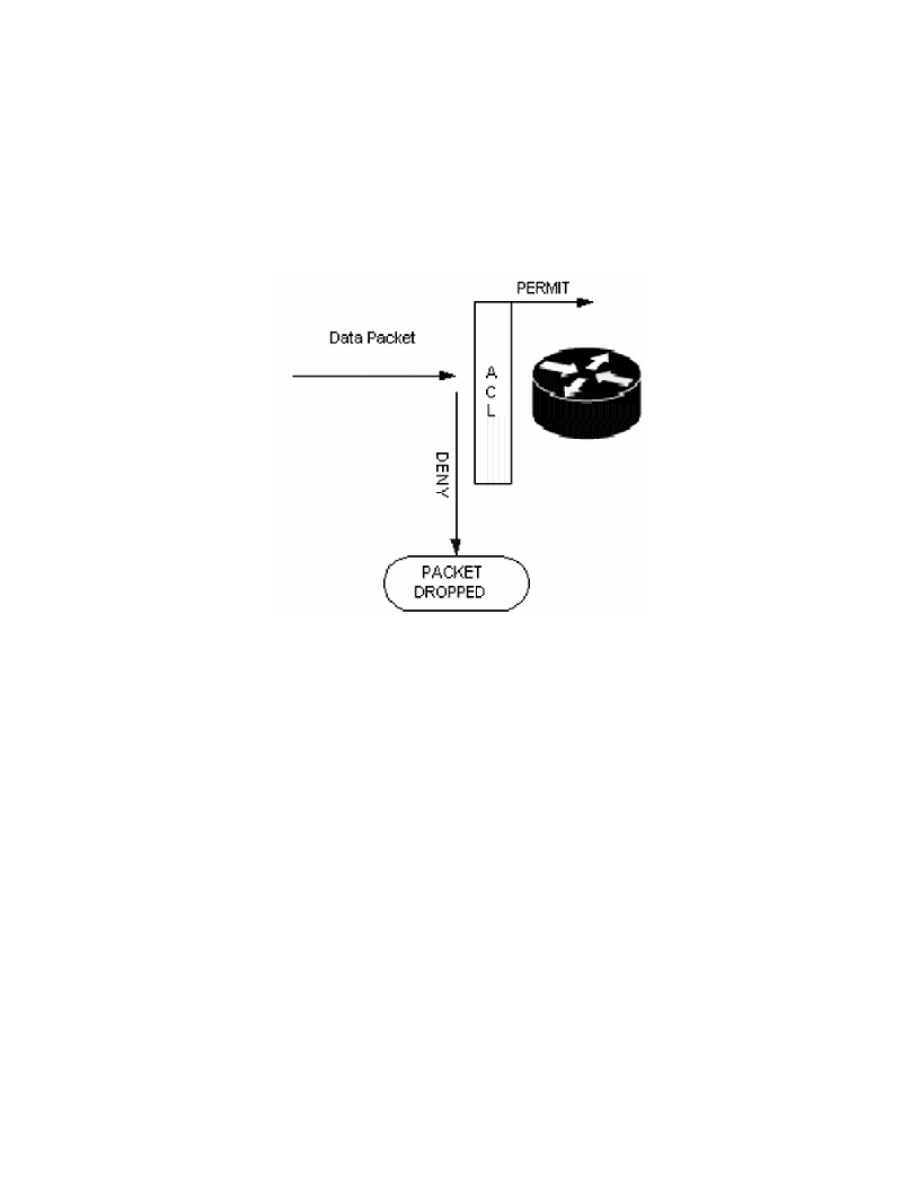
After the access list has been created with statements, it must be applied to a
router interface so that traffic encountering that router interface will be
permitted or denied based upon the list conditions. When applying an access
list you must also specify if the access list applies to traffic coming in to or
going out of the router interface. Remember, all directions are from the router's
perspective. Virtual interfaces, such as vty lines in the router used for telnetting
purposes, can also have access lists applied to control traffic flow. the figure
below shows inbound access list flow.
Inbound access list flow.
When you use an outbound access list, the packet must enter the router and do
a lookup in the routing table to determine the destination interface. If an access
list has been applied to the interface to deny the packet, then routing
processing has been wasted. It is best to use an inbound access list whenever
possible, because the routing look up for denied traffic is inefficient. the figure
below shows outbound access list flow.
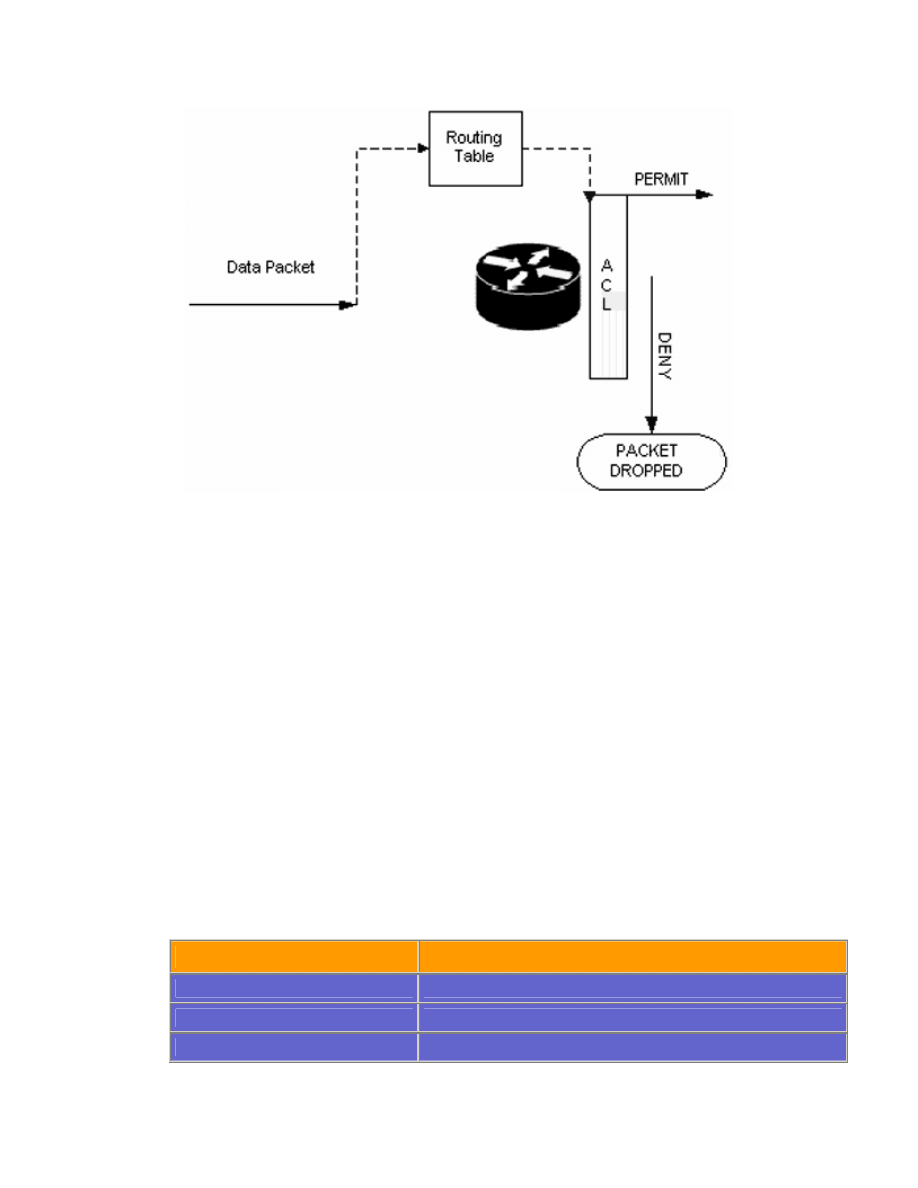
Outbound access list flow.
Configuring acls using Cisco's IOS
In Cisco's IOS the syntax to create an acls is: (config)#Access-list <access
list number> [permit | deny] {specified traffic}. This command is
executed in global configuration mode.
To build multiple statements in the same access list, use the same access list
number. The access list number represents what type of access list you are
creating. There are predefined ranges of numbers to denote what type of
protocol traffic the access list is configured to filter. For example, if the access
list number is 1-99 or 100-199, then the access list is an IP access list, as
shown in the following table. When the access list is applied, a match against
the specified traffic will be determined and the operation (permit or denied) will
be executed.
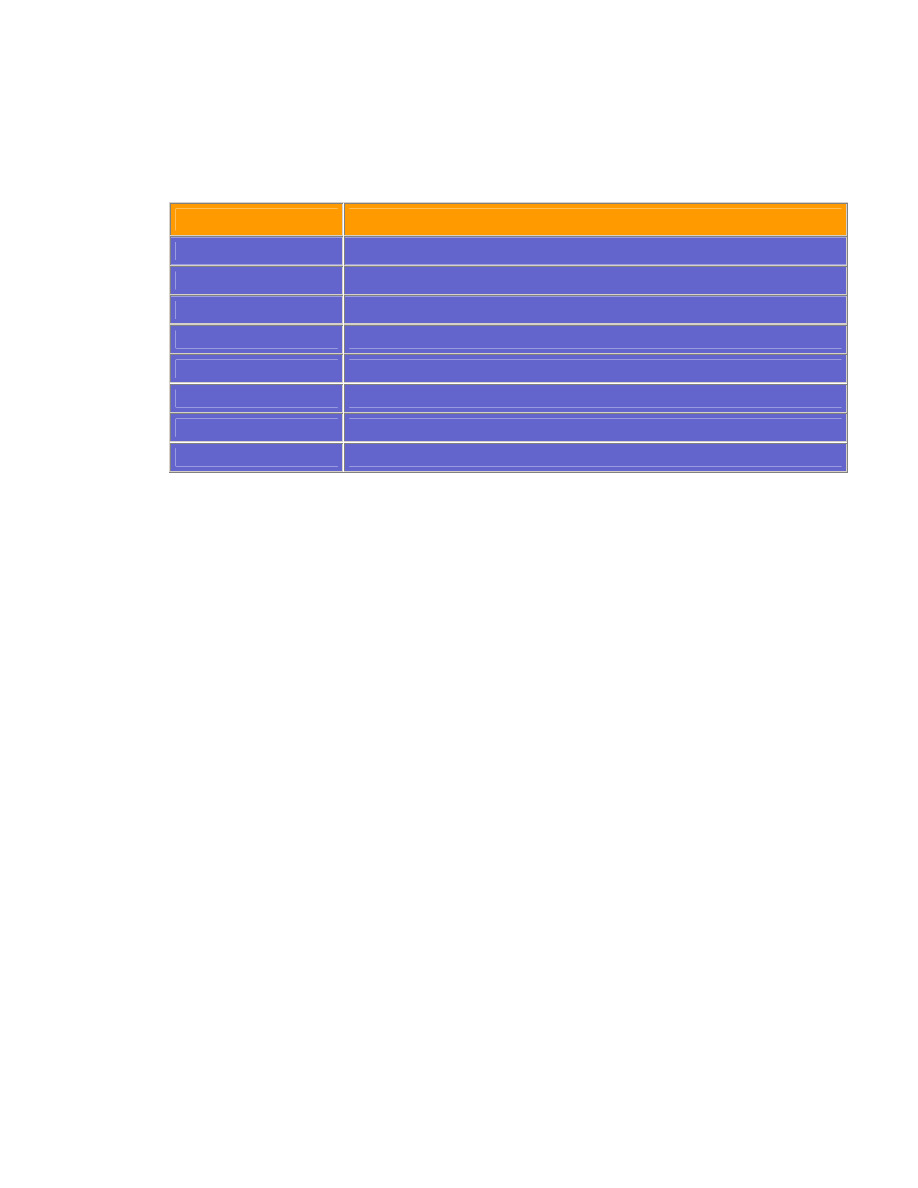
Protocol
ACL Number Range
IP Standard
1-99
IP Extended
100-199
IPX Standard
800-899
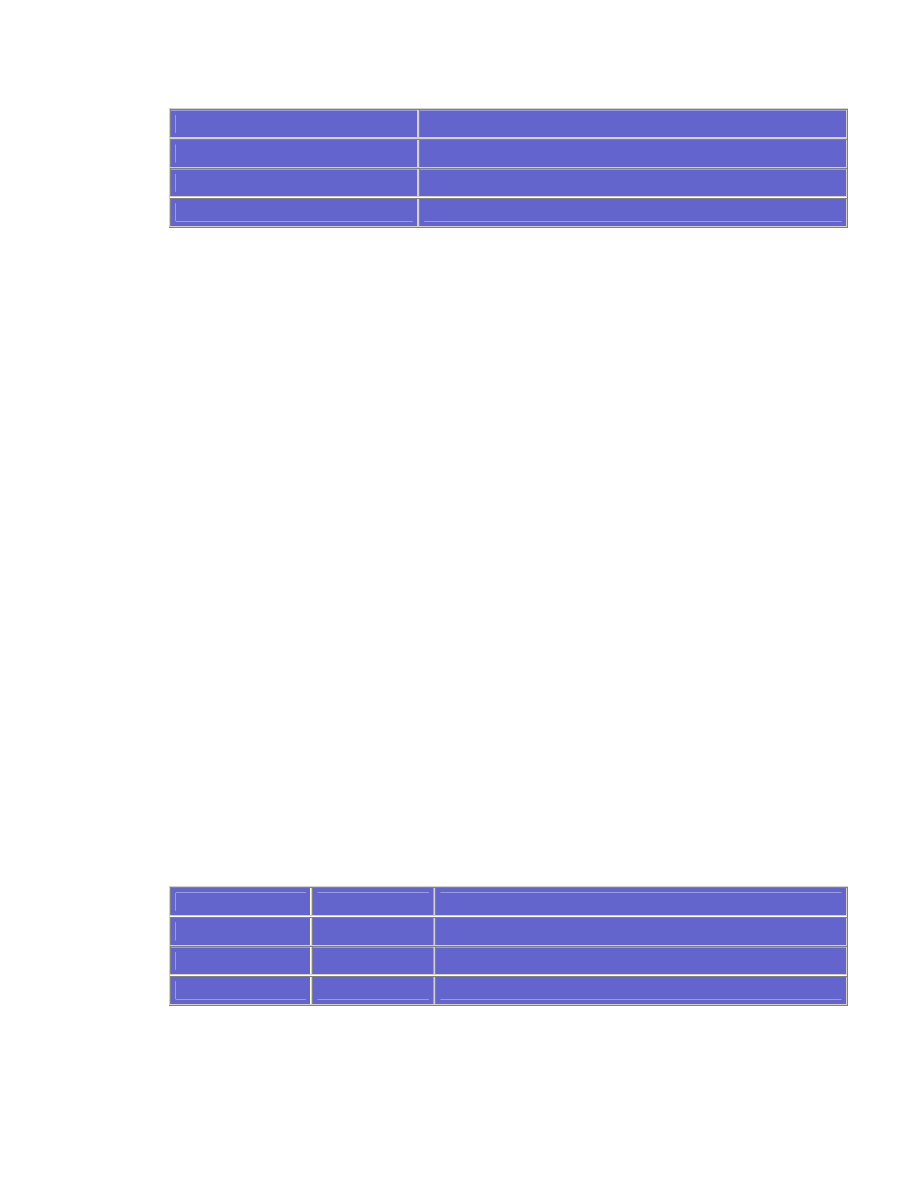
IPX Extended
900-999
IPX SAP filters
1000-1099
AppleTalk
600-699
DECnet
300-399
To apply the list to an interface: (config-if)#{protocol type} Access-
group <access-list number> [in | out]. This command is executed in
interface configuration mode.
The protocol type parameter specifies what type of protocol traffic is being
evaluated with the access list. Examples of protocol types are IP, IPX, and
AppleTalk.
The access list number in this command references the access list number you
want to apply to this router interface. You have to specify which access list you
want to apply to the interface, as you are able to configure multiple access lists
per router.
The last parameter [in | out] specifies which direction you want to apply the
access list. If you want all traffic coming in to the router interface to be filtered,
choose in. If you want to filter traffic going through your router, out of the
applied interface, then choose out. NOTE: You never truly filter traffic
originating from a router, only traffic going through the router in the outbound
direction.
Wildcard Masks
When configuring access lists, a wildcard mask is used instead of a normal
subnet mask. In a wildcard mask the bit values are swapped, thus a one means
to ignore and a zero means to check the corresponding bit value. If you have
difficulty calculating a wildcard mask, simply calculate the subnet mask and
"flip the bits." For example, if we wanted to create an access list that denied all
traffic in the entire class B subnet 128.90.0.0 the wildcard mask is calculated as
follows:
IP Address
128.90.0.0
10000000. 01011010. 00000000. 00000000
Subnet Mask
255.255.0.0
11111111. 11111111. 00000000. 00000000
"FLIP THE BITS"
Wildcard Mask
0.0.255.255
00000000. 00000000. 11111111. 11111111
In this example the first 16 bits will be checked for matches. If the ip address
matches these bits then the condition (permit or deny) will be applied to the
traffic. Let's take a look at a more complex example. Suppose you wanted to
deny a range of addresses within a class B subnet, 128.90.32.0 to
128.90.32.31. First, find the common bits. Then determine the wildcard mask
by checking the common bits (zero) and ignoring the other bits (one).
Decimal
Binary
128.90.32.0
10000000. 01011010.00100000.00000000
128.90.32.1
10000000. 01011010.00100000.00000001
128.90.32.2
10000000. 01011010.00100000.00000010
128.90.32.3
10000000. 01011010.00100000.00000011
128.90.32.30
10000000. 01011010.00100000.00011110
128.90.32.31
10000000. 01011010.00100000.00011111
Wildcard Mask
Check common bits, 0 =check and 1=ignore
0.0.0.31
00000000.00000000.00000000.00011111
In some instances you may need to permit a specific host or permit all traffic.
The wildcard mask to check all bits, thus indicating a specific host, would be all
zeros. In Cisco's IOS you can use the keyword host or the 0.0.0.0 wildcard
mask to denote a single host. The default wildcard mask for access list ip
addresses is 0.0.0.0 (host). The three statements that follow are the same;
only traffic from 192.168.7.1 is permitted. Access-list 1 permit
192.168.7.1 0.0.0.0 Access-list 1 permit 192.168.7.1 host Access-
list 1 permit 192.168.7.1 To denote all traffic you can use the keyword any
or 0.0.0.0 ip address and 255.255.255.255 wildcard mask. The following
statements are identical and permit all ip traffic. Access-list 2 permit
0.0.0.0 255.255.255.255 Access-list 2 permit any
Generally speaking, there are two types of acls, standard and extended.
Standard acls are easy to understand and easy to configure, they filter based
on more generic traffic group information. Extended acls are more difficult to
configure, but allow you to filter based upon more specific traffic group
information, allowing for greater granularity.
How an ACLS operate -
Access lists consists of permit and/or deny statements. These statements are
executed in a top down fashion. As traffic encounters the access list, the access list is parsed top to bottom,
looking for a match. The first match encountered will determine if the traffic is permitted or denied.
Overview of Standard IP Access Lists
Standard IP acls filter traffic based upon source ip address only. The number
range for standard ip acls is 1-99. Standard ip acls filter the entire TCP/IP
protocol suite. There is no method using standard ip acls to filter only a specific
port or protocol. Two of the benefits of standard acls are that they are easy to
understand and easier to maintain.
The Cisco IOS command to configure a standard ip access list:
(config)#Access-list <1-99> [permit | deny] <source ip address>
<wildccard mask>. To apply the access list to an interface: config-if)#ip
access-group <1-99> [in | out]. When applying the access-group command
to an interface, the default filtering direction is outbound. To better understand
how standard access lists operate, let's look some examples.
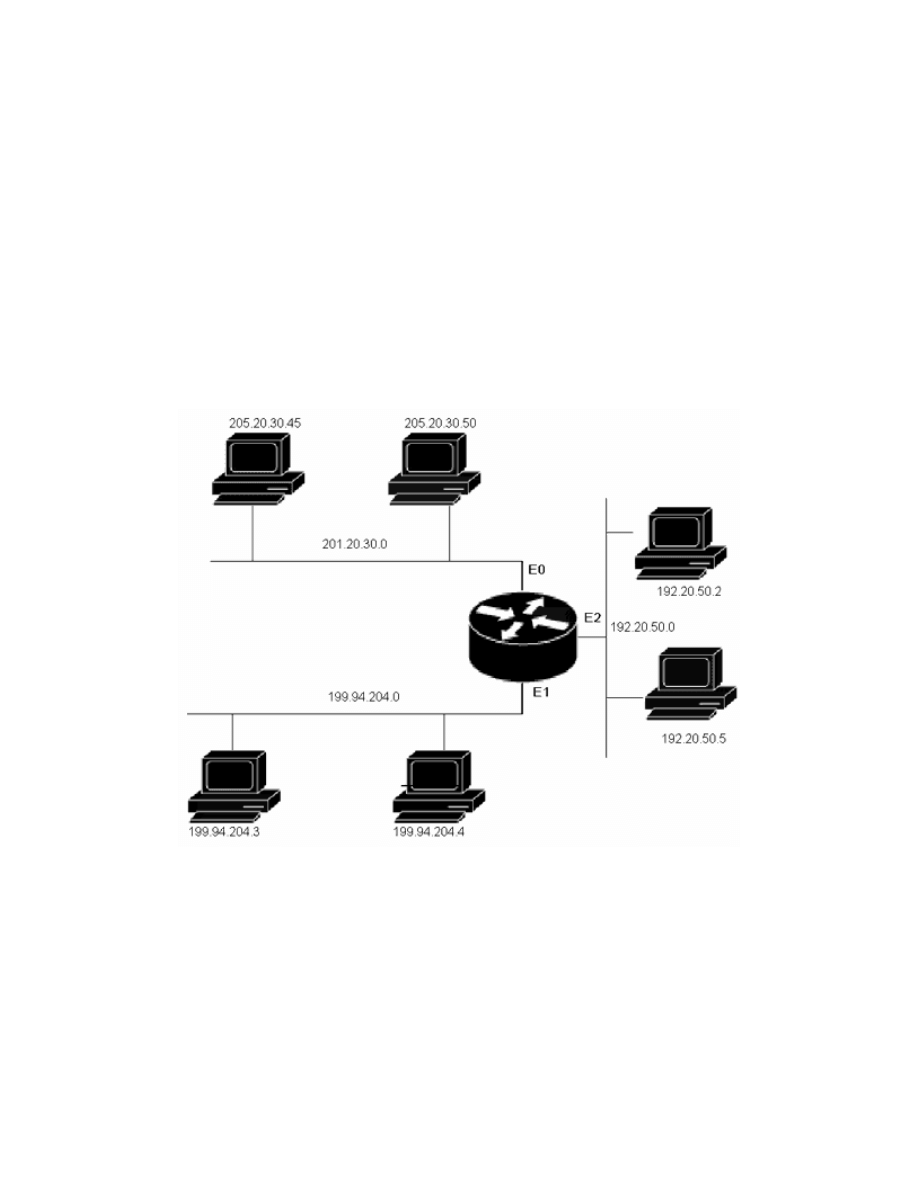
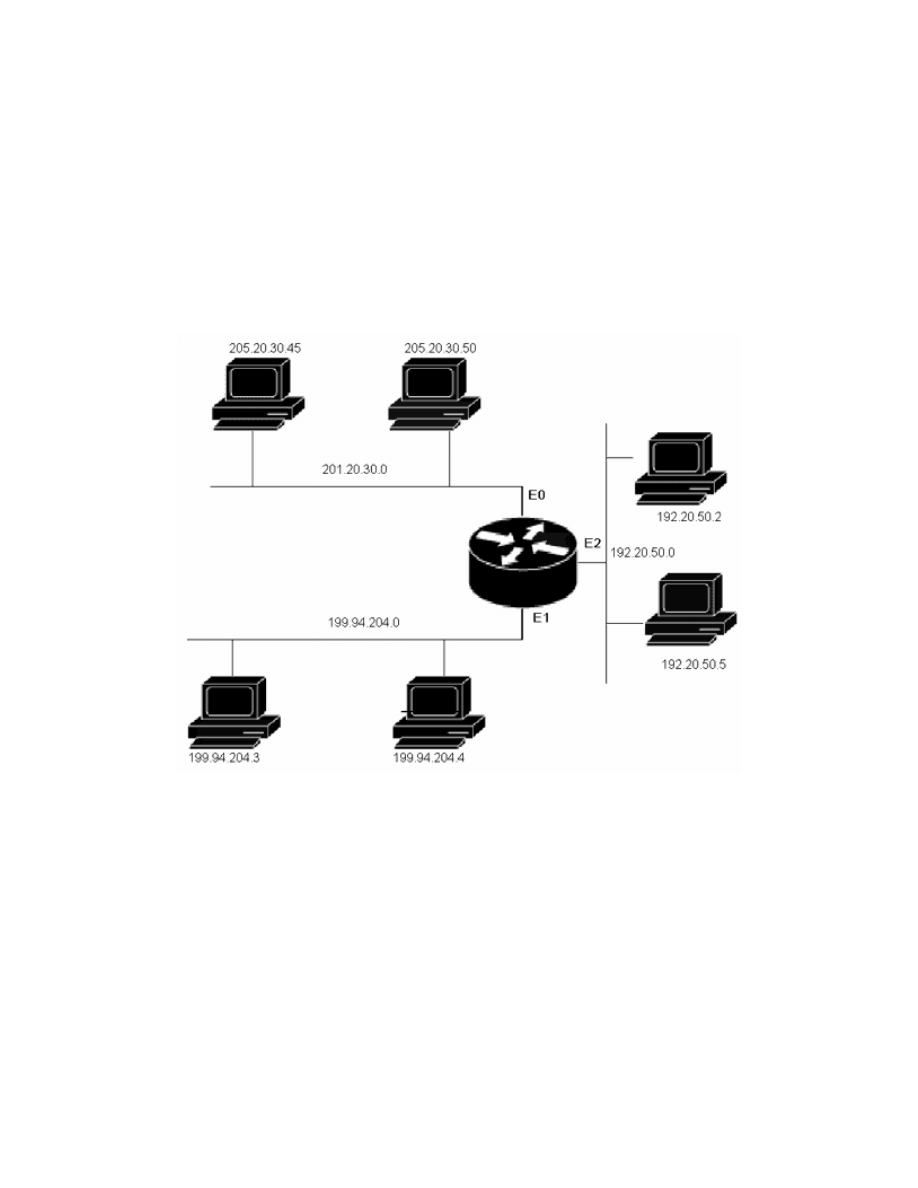
Example One: employees on network 205.20.30.0 are complaining of slow
response due to high traffic volume. As a network administrator you want to
limit IP access to the 205.20.30.0 network by only allowing traffic from the host
192.20.50.2, and any host from the 199.94.204.0 network. the figure below
shows you network 205.20.30.0.
Network 205.20.30.0.
To solve this problem, create an access list: (config)# access-list 10
permit 192.20.50.2 0.0.0.0 ! all zeros in the wildcard mask permits the
specific host 192.20.50.2. (config)# access-list 10 permit 199.94.204.0
0.0.0.255! wild card mask 0.0.0.255 permits traffic from any host on the
199.94.204.0 network. config)# access-list 10 deny 0.0.0.0
255.255.255.255 ! Blocks all other ip traffic. To apply it to the interface:
(config)# interface e0 (config-if)# ip access-group 10 out.
Example Two: using the same network diagram. In your network, you would
like to isolate subnet 192.20.50.0 from the rest of the company. This access list
denies a specific subnet. To solve this problem, create an access list:
(config)# access-list 20 deny 192.20.50.0 0.0.0.255 !Denies all traffic
from subnet 192.20.50.0. (config)# access-list 20 permit any !Permits all
other ip traffic. To apply it to the interface: (config)# interface e2
(config-if)# ip access-group 20 in.
Place standard acls as close to the destination as possible, since they only filter
based upon source ip address. Otherwise, you may unintentionally keep traffic
from reaching other devices.
Explain how standard IP access list works -
Standard ip access lists filters traffic based upon source ip address
only. The number range for standard ip access lists is 1-99. Standard ip access lists will filter the entire TCP/IP
protocol suite. There is no method using standard ip acls to filter only a specific port or protocol. The benefits of
standard access lists are that they are easy to understand, thus easier to maintain.
Introduction to Extended IP Access Lists
Extended acls allow for more exact filtering, based on source and destination
addresses. Unlike standard acls, this allows you to filter traffic coming from a
particular address going to a particular address, resulting in more accurate
filtering. Extended acls also allows you to filter based on port numbers. The
following table shows what port number correlates with what ftp or dns traffic.
However, extended acls is more difficult to maintain. The number range for
extended acls is 100-199.
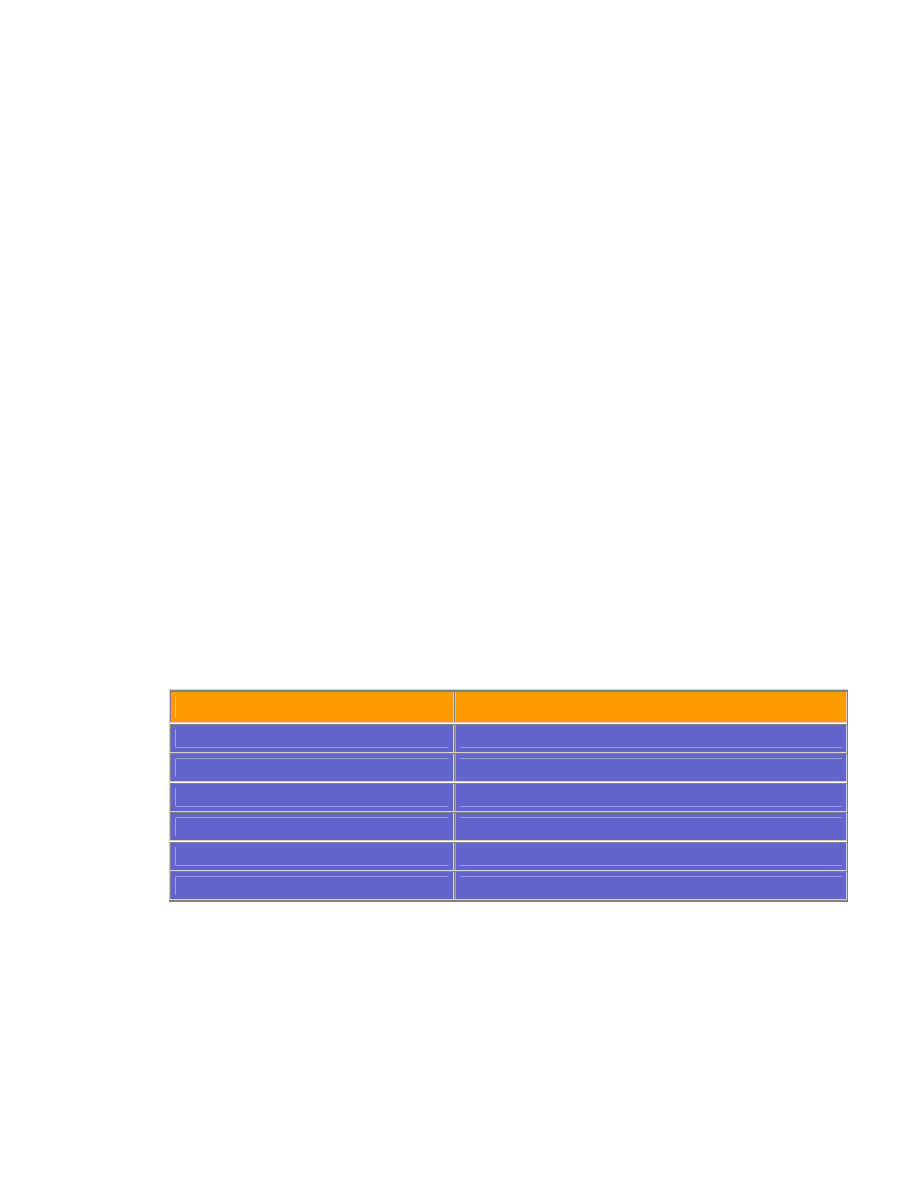
Port Number
Description
20
FTP data
21
FTP program connection
23
Telnet
25
SMTP
53
DNS
69
TFTP
The Cisco IOS command to configure an extended ip access list is: (config)#
access-list <100-199> [permit | deny] [ip | tcp | udp | icmp | gre
| igrp] <souce ip address><source wildcard mask> [lt | gt | eq |
neq] <destination ip address><destination wildcard mask>. You can
also set option parameters of established, which allows traffic if the
acknowledgement bits are set or log, log sends a logging message to the
console. To apply to an interface: (config-if)# ip access-group <100-199>
[in | out]. When applying the access-group command to an interface, the
default filtering direction is outbound. To better understand how extended
access lists operate, let's look some examples.
Example One: based on the network diagram in the figure below. In this
example, we only want hosts residing on the 199.94.204.0 to output IP traffic
to hosts 205.20.30.45 and 192.20.50.2. This illustrates how access lists can be
used to control traffic flow.
Network diagram.
To solve this problem, create an access list: (config)# access-list 110
permit ip 199.94.204.0 0.0.0.255 205.20.30.45 0.0.0.0 !Allows ip traffic
from subnet199.94.204.0 to host 205.20.30.45. (config)# access-list 110
permit ip 199.94.204.0 0.0.0.255 192.20.50.2 0.0.0.0 !Allows ip traffic
from subnet 199.94.204.0 to host 192.20.50.2. To apply it to
interface:(config)#interface e1 (config-if)#ip access-group 110 in.
Example Two: using the same network diagram. We want to decrease the
amount of ftp traffic in our network. To control this traffic, we will deny ftp
traffic from subnet 205.20.30.0 to 199.94.204.0 and allow all other ip traffic.
To solve this problem, create an access list: (config)# access-list 120
deny ftp 205.20.30.0 0.0.0.255 199.94.204.0 0.0.0.255 eq 21
(config)# access-list 120 deny ftp 205.20.30.0 0.0.0.255

199.94.204.0 0.0.0.255 eq 20 !Deny ftp traffic from subnet 205.20.30.0 to
199.94.204.0. Ftp uses two ports for communication, so both ports need to be
denied for all ftp traffic to be filtered. (config)# access-list 120 permit ip
any any !Allow all other ip traffic. To apply it to interface:(config)#interface
e0 (config-if)#ip access-group 120 in.
Place extended acls as close to the source address as possible, because
extended acls filter based on source and destination address. This allows
filtered traffic to be dropped sooner, decreasing bandwidth consumption.
Removing Standard and Extended ACLs
To remove standard and extended access list type "no" before the configuration
command. (config)# no access-list 1 (config)# no access-list 100
There is no way to delete a single statement in an access list. When you type
"no" and the access-list <acl number> the entire access list is removed. This
can be troublesome if you make a typing error. To correct this you have to
remove the entire access list and rebuild all the statements.
Also, remember that the order of the statement in your acls is critical. Say you
have an active acls in your network, and you would like to add a new subnet as
the second permit statement in a ten-statement access list. The only way to
add the subnet in the proper order is to delete the access list and rebuild it.
Using named access lists, which we will discuss later, solves this problem.
Remove the access list from the interface, instead of deleting it, if you think
you might need to apply it again. To remove the acl from the interface, go into
interface configuration mode and type "no" before the configuration command.
(config-if)# no ip access-group 100 in
EXPLAIN HOW EXTENDED ACLS OPERATES -
Extended access lists allow for more exact filtering.
Extended acls allows for filtering based upon source and destination addresses. Unlike standard acls, this give
you the ability to filter traffic coming from a particular address going to a particular address resulting in more
accurate filtering. Extended acls allow you to also filter based upon port numbers. So you have the ability to filter
specifically ftp or dns traffic. With the obvious advantage to using extended acls the disadvantage would be that
it more difficult to maintain. The number range for extended access lists is 100-199.
2. When configuring an extended IP access list, when do you want to set the established parameter?
When you need to allow traffic that has the acknowledgement bit set.
Overview of Named IP Access Lists
Named access lists allow you to label an access list descriptively. Each acl name
must be totally unique. If you create a standard named access list called
ENGINEERING, you cannot create an extended acl with the same name.
Naming the acl helps identify its purpose. Named access lists are useful in a
large network with many access lists. Remember that access list numbers are
in groups of 100, which limits how many numbered lists you can have. If you
have more than 100 standard or extended access lists, use named lists. An
added benefit is the ability to modify a named access list by removing a single
statement.
The Cisco IOS command to configure a named ip access list: (config)# ip
access-list [standard | extended] <name> (config {std- | ext-
}nacl)# [permit | deny] {specified traffic}. To apply to an interface:
(config-if)# ip access-group <name> [in | out]. To delete a specific
statement, type "no" before the permit or deny statement. Removing an
individual statement will not remove the entire list.
The following is a configuration example. Create a list:(config)# ip access-
list standard TEST (config-std-nacl)# permit 192.168.7.2 (config-
std-nacl)# permit 192.178.4.0 0.0.0.255 (config-std-nacl)# deny
all. Apply the list: (config-if)# ip access-group TEST in. To remove the
list: (config)# ip access-list standard TEST (config-std-nacl)# no
permit 192.168.7.2.
Explain the benefits of a name access list -
Named access lists allow you to label an access list descriptively.
Each acl name must be totally unique. Naming the acl can help the administrator readily identify its purpose.
Using named access lists are also a good feature if you are in a large network using many access lists.
Remember that the range of access list number are in groups of 100, so if you have more than 100 standard or
extended access list then you have to use named lists. The added benefit of using named acls, is the ability to
modify an access list by removing a single statement.
Guidelines
To implement successful acls, remember the following guidelines:
Plan
Your acl should be well thought out, and planned in advanced.
Create
Be sure to select the correct access list range number for your type
of acl. Arrange acl statements from most specific to least specific.
Order is critical, be careful not to make typing errors. An implicit
"deny all" follows every acl.
Apply
Apply standard acls close to the destination.Apply extended acls
close to the source. Traffic originating from the router cannot be
filtered. There can only be one acl per interface, per protocol, per
direction.
Recommendation Always create acls using a text editor, then cut and paste into the
router. This makes modifying numbered acls easier.
Verification
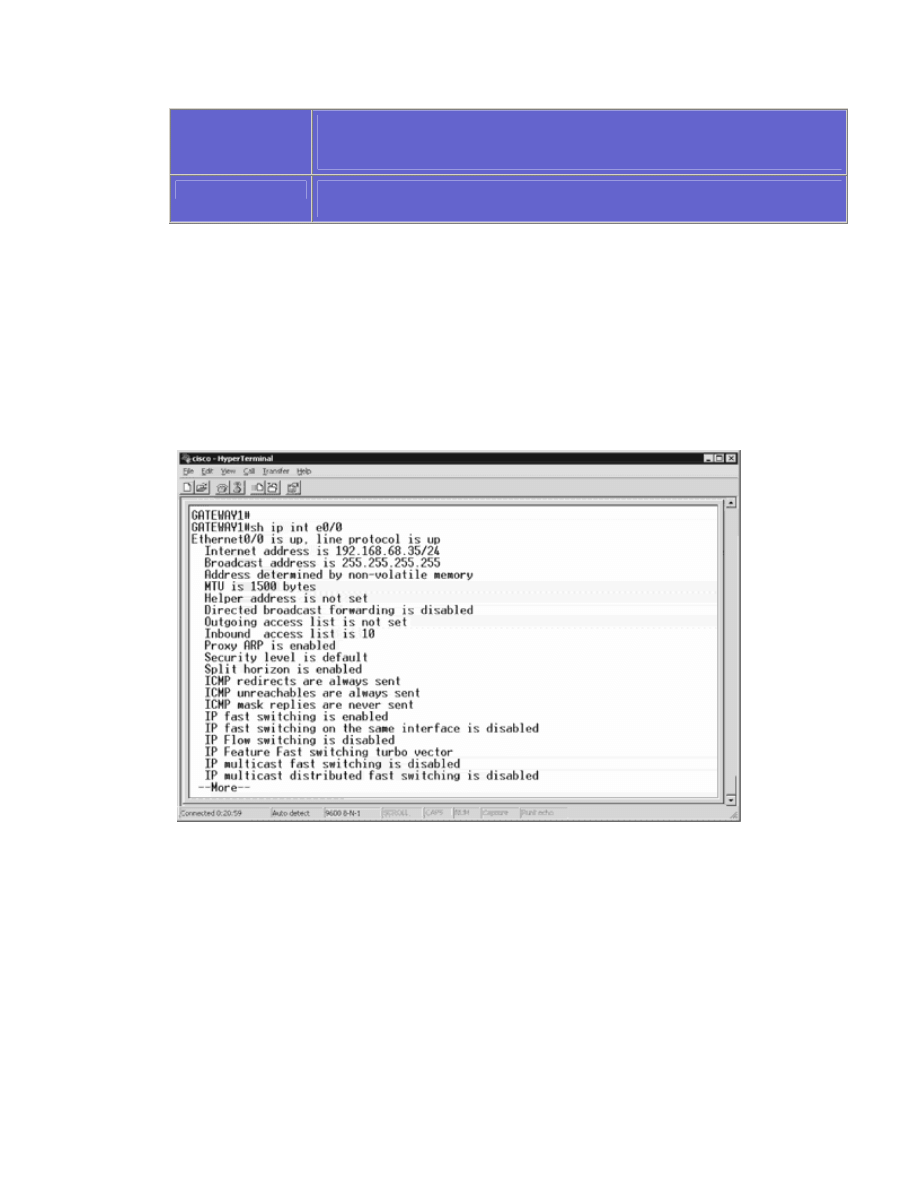
To verify your access list configuration use the show ip interface and show
access-lists commands available in the IOS. Show ip interface will display
the direction and number of access list applied to that interface, as shown in
the figure below.
Output display of show ip interface command.
Show access-lists displays all access lists configured on the router, ans shown
in the figure below. You can also view each access lists if the acl number is
indicated.
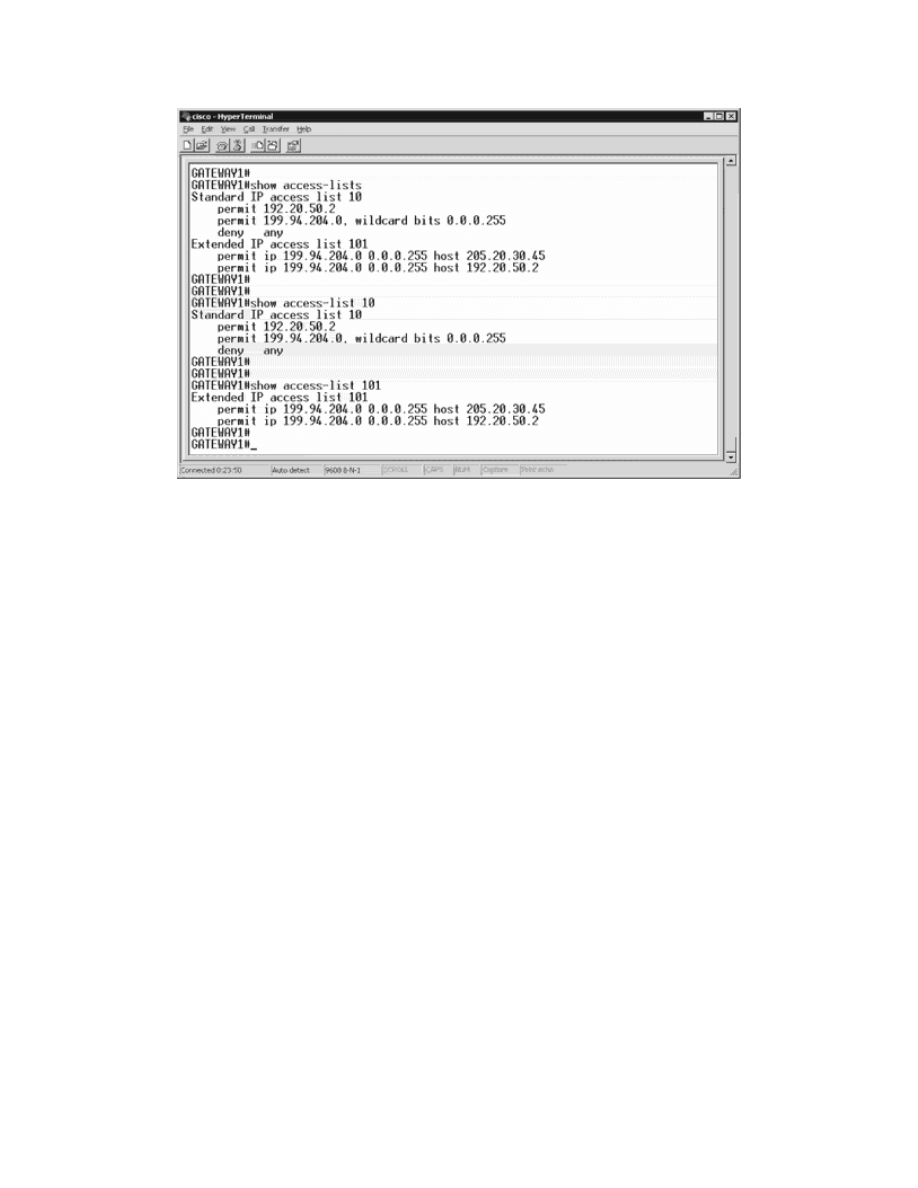
Output displays for show access-lists command.
Other Applications
Acls can be used on a router's virtual interfaces, in addition to the physical
interfaces. Most routers use five default virtual terminal lines (vty) for telnet.
Traffic can be filtered on these lines for security purposes. To do this, set the
same restriction on all virtual lines using an access list. Configure the access list
as detailed in previously, and then apply the list to the vty lines. The command
to apply an acl to vty lines is: (config)#line vty 0 4 (config-line)#
access-class <acl number> [in | out]. Remember to create the access list
first, and then apply the list to the vty lines using the access-class command.
the figure below illustrates this concept.
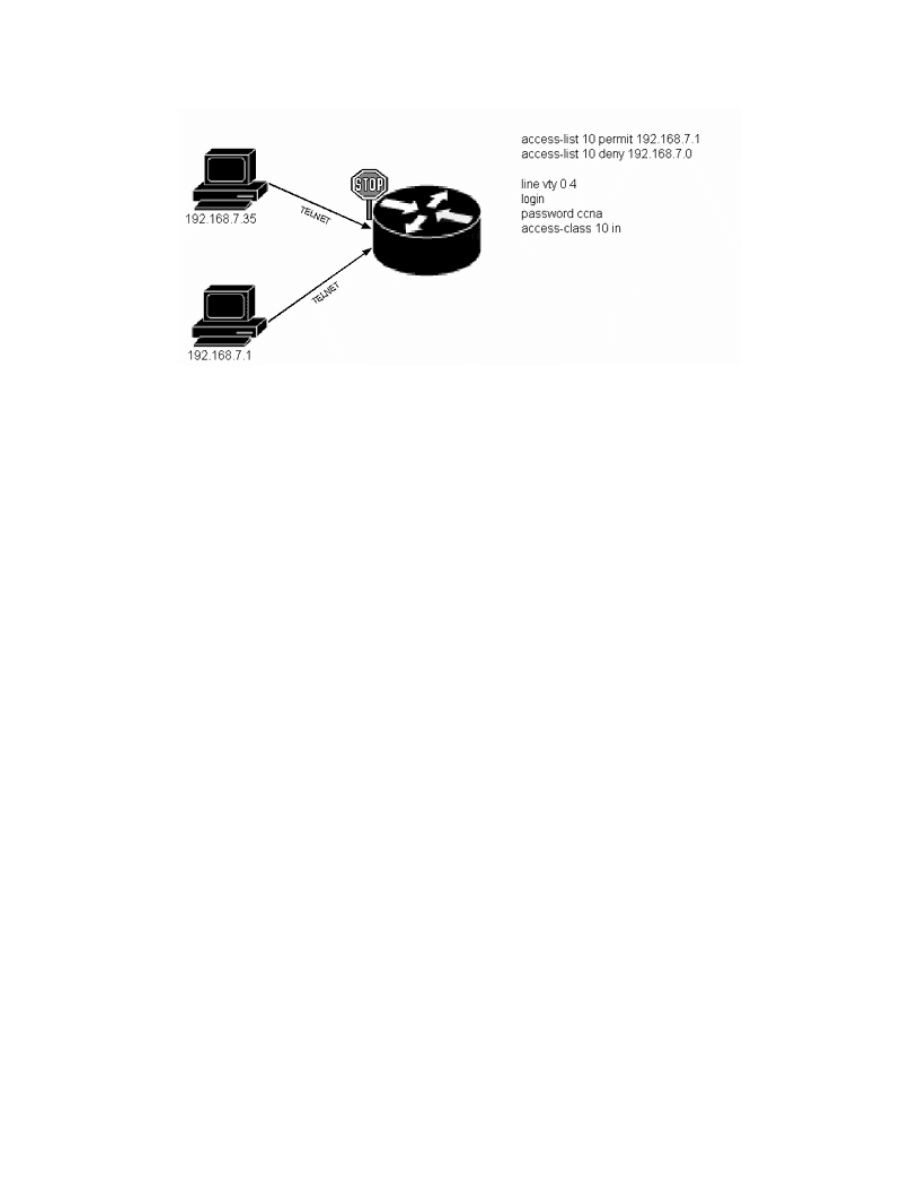
Applying an acl to vty lines.
Only device 192.168.7.1 is able to telnet into the router. When device
192.168.7.35 attempts to telnet to the router, the source address matches the
second access list statement and the telnet traffic is denied. In your network,
the permitted device could be the network administrator, and all other devices
will not be able to telnet into the router. Note: The access list shown can be
implemented with fewer statements; the deny statement can be removed with
the same results.
•
Explain the two routing protocols, the method of best route determination, and how they
update other routers in their network.
1. Explain the two routing protocols, the method of best route determination, and how they update other
routers in their network.

Overview
There are two methods of sending routing information over an IPX network.
The original and still most common method is to use Router Information
Protocol or RIP (not to be confused with the RIP protocol for TCP/IP, although it
operates in a similar fashion). The second, and newer of the two, is the
NetWare Link Services Protocol, or NLSP. NLSP is a link-state routing protocol
that works in a similar fashion to OSPF in the TCP/IP world and features
advantages like faster convergence time, greater network size support, and
uses less bandwidth.
The RIP Routing Protocol
RIP is a distance vector route discovery protocol. It uses hop counts (the
number of routers a packet must pass through to get to a destination network)
combined with Time Ticks (the amount of time in 1/18-of-a-second intervals
that it will take to get there) to determine the best route for a network. RIP has
a maximum of 15 hops to get to a destination before the packet is discarded.
RIP sends period broadcast messages to other routers that show what networks
it knows about (minus the route to the network it is sent out on). RIP
information is sent in the Data field of the IPX packet, with a socket type of
0x0453.
Every 60 seconds, RIP routers on an IPX network send out a broadcast
message that includes their entire routing table (minus the network of the
interface it is sent out on) over each interface configured for IPX. Each neighbor
router that receives this RIP update adds one hop to the network's hop count,
updates its own routing table with this information, and sends out this updated
table to its neighbors. As you can probably imagine by now, a large IPX
network using RIP can generate quite a bit of broadcast traffic on a regular
basis.
RIP also works with the Service Advertising Protocol (SAP) to discover and
advertise network services for NetWare clients. For example, when an IPX client
boots up, it usually sends out a SAP "Get Nearest Server" broadcast request. If
there are no servers on that particular LAN segment to respond first, the IPX
router checks its SAP and RIP tables to determine the nearest file server
(Service Type 0x0004) and what its internal IPX number is. Remember that an
internal IPX number is the same as a network address, as far as the routers are
concerned.

Cisco routers by default use RIP for routing IPX networks. The Cisco IOS
configuration command "IPX Routing" actually starts up the RIP and SAP
process on the router.
RIP is a distance vector protocol based on hop counts and time ticks. RIP sends out a periodic broadcast of its
complete routing table. NLSP is a link state protocol that selects routes based on hop counts, time ticks, and
other information like the line speed of segments in the path of the network. NLSP only sends out changes to a
route when necessary, and after network listings expire.
Wyszukiwarka
Podobne podstrony:
Access Lists
ACL IOS IPv4 Access Lists
Dungeons and Dragons 3 5 Accessory Color Character Sheets with Multiple Spell Lists
All About Access Control Lists
04 QueryByExample Access
Access 2002 Projektowanie baz danych Ksiega eksperta ac22ke
access 4 progress check unit 6,7,8, Access 4 Progress Check 6
Access 3 Test 7 A
Configuration Guide WAN Access(V100R006C00 02)
access programowanie w vba
Access to History 001 Gas Attack! The Canadians at Ypres, 1915
Ćwiczenie nr 1 (Access 2007)
Open Access and Academic Journal Quality
access 3
CISCO Accessible Theme8
Access 2003 dla każdego
więcej podobnych podstron