

V
V
T
T
I
I
ntegrity
ntegrity
S
S
ervices for
ervices for
N
N
etworking
etworking
Uri Blumenthal
Uri Blumenthal
Security Architect
Security Architect
Corporate Technology Labs
Corporate Technology Labs

3
*Third party marks and brands are the property of their respective owners
Agenda
Agenda
y
y
Research motivation
Research motivation
y
y
VISN research
VISN research
–
–
Integrity Measurement
Integrity Measurement
–
–
Memory Protections
Memory Protections
y
y
Potential Applications
Potential Applications
4
*Third party marks and brands are the property of their respective owners
'Shadow Walker' Pushes
Envelope for Stealth Rootkits
Eweek.com* July 28, 2005
… a kernel-level program capable of
hiding processes and elevating process
privileges. …explore the idea of memory
subversion to hide the rootkit in memory
with almost no performance impact.
… Shadow Walker will "raise the bar" for
rootkit detectors with a memory hook
engine that subverts the kernel memory
to hide the proof-of-concept driver
… CD Copy Protection Relies on
Hacker Rootkit
Techweb* Nov 2, 2005
Security researchers have identified a
Security researchers have identified a
rootkit
rootkit
…
…
within the copy protection
within the copy protection
scheme
scheme
…
…
to prevent music CDs from
to prevent music CDs from
being copied to computers
being copied to computers
Virus Attacks Cost $14.2B
Virus Attacks Cost $14.2B
+
+
+
Computer Economics - 2005 Malware Report
Checks for the presence of a debugger and
terminates itself if one is found on the compromised
computer. The same action is taken if it detects that
it's running in a virtual machine.
W32.Kiman.A worm
Discovered on: February 02, 2006
Discovered on: February 02, 2006
Symantec*
Symantec*
SecurityResponse
SecurityResponse
*
*

5
*Third party marks and brands are the property of their respective owners
Some Malware Examples
Some Malware Examples
y
y
3 of the top 10 malicious code
3 of the top 10 malicious code
samples reported to Symantec
samples reported to Symantec
*
*
disable security applications
disable security applications
+
+
–
–
Tooso.F
Tooso.F
(Trojan),
(Trojan),
Tooso.B
Tooso.B
(Trojan),
(Trojan),
KillAV
KillAV
(Trojan)
(Trojan)
y
y
Other well known malware
Other well known malware
–
–
W32.Witty.Worm: Attacks firewall, destroys data
W32.Witty.Worm: Attacks firewall, destroys data
–
–
W32.Beagle.DN@mm : Attempts to disable security apps
W32.Beagle.DN@mm : Attempts to disable security apps
–
–
W32.IRCBot.I : Attempts to end security processes
W32.IRCBot.I : Attempts to end security processes
–
–
W32.Aizu.G : Attempts to modify firewall settings
W32.Aizu.G : Attempts to modify firewall settings
–
–
W32.Bugbear.b@mm: Attempts to shut down popular
W32.Bugbear.b@mm: Attempts to shut down popular
antivirus and firewall apps
antivirus and firewall apps
+
Symantec Internet Security. Threat Report. Trends for January 05–
June 05. Volume VIII, Published September 2005
6
*Third party marks and brands are the property of their respective owners
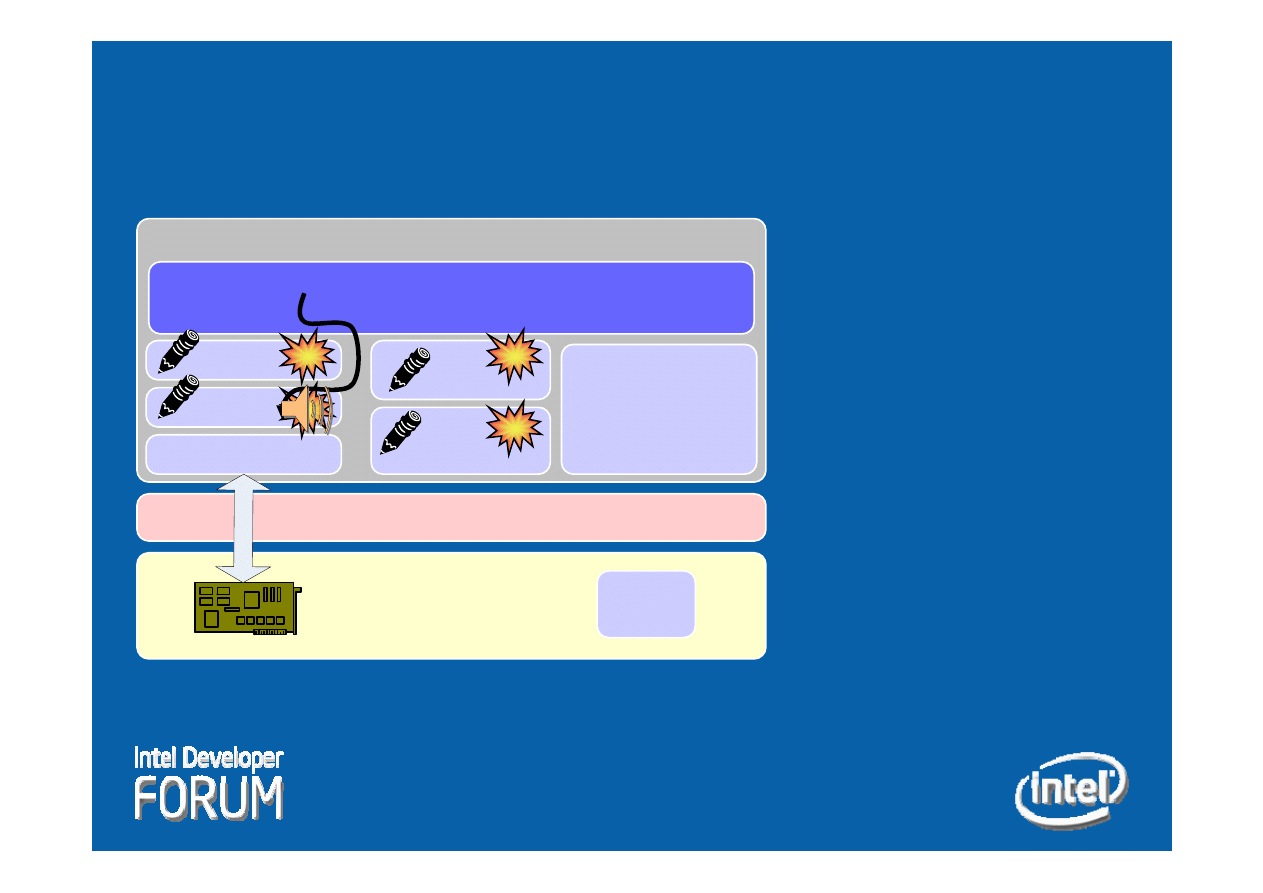
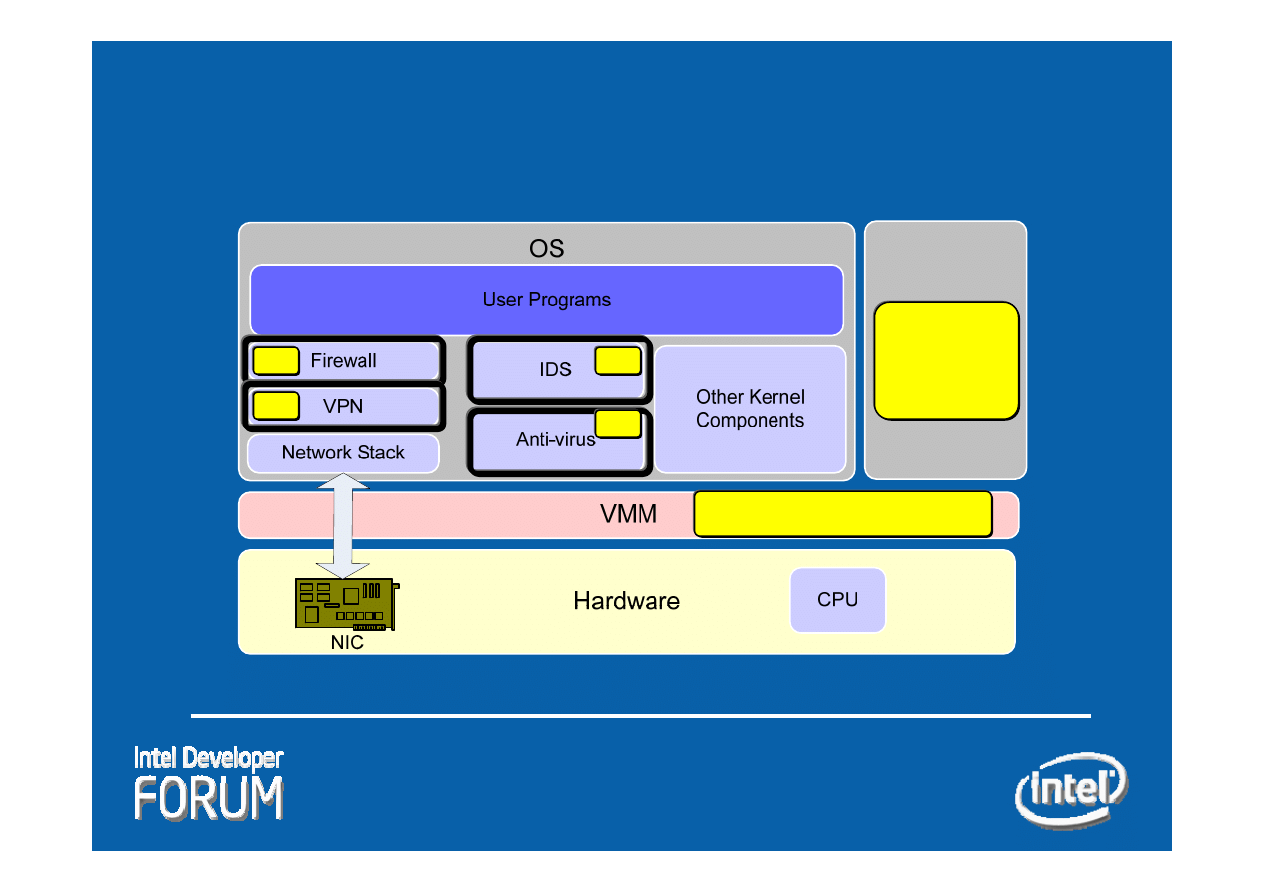
Hardware
BIOS
OS
NIC
Network Stack
VPN
Firewall
IDS
Anti-virus
Other Kernel
Components
User Programs
CPU
Effects Of Memory Based
Effects Of Memory Based
Attacks
Attacks
y
y
Disable
Disable
y
y
Circumvent
Circumvent
y
y
Eavesdrop
Eavesdrop
y
y
Modify
Modify

7
*Third party marks and brands are the property of their respective owners
New Attacks Require New
New Attacks Require New
Approach
Approach
y
y
Sophistication of attacks increasing
Sophistication of attacks increasing
cleanup costs
cleanup costs
y
y
Attacks target software security
Attacks target software security
applications
applications
y
y
Memory based attacks not completely
Memory based attacks not completely
addressed by today
addressed by today
’
’
s solutions
s solutions
y
y
Time between publication and exploit
Time between publication and exploit
decreasing
decreasing
New attacks target software integrity and presence
New attacks target software integrity and presence

8
*Third party marks and brands are the property of their respective owners
Agenda
Agenda
y
y
Research motivation
Research motivation
y
y
VISN research
VISN research
–
–
VISN Integrity Measurement
VISN Integrity Measurement
–
–
VISN Memory Protections
VISN Memory Protections
y
y
Potential Applications
Potential Applications

9
*Third party marks and brands are the property of their respective owners
VISN Approach
VISN Approach
y
y
What it is:
What it is:
–
–
Recognize the valid software agents on the
Recognize the valid software agents on the
platform and aid in protecting them
platform and aid in protecting them
–
–
Aid in mitigating memory based attacks
Aid in mitigating memory based attacks
y
y
What it is
What it is
not
not
:
:
-
-
A reactive system that tracks known attacks
A reactive system that tracks known attacks
using signatures
using signatures
-
-
Example
Example
-
-
A signature based host intrusion
A signature based host intrusion
detection system or an anti
detection system or an anti
-
-
virus program
virus program
10
*Third party marks and brands are the property of their respective owners
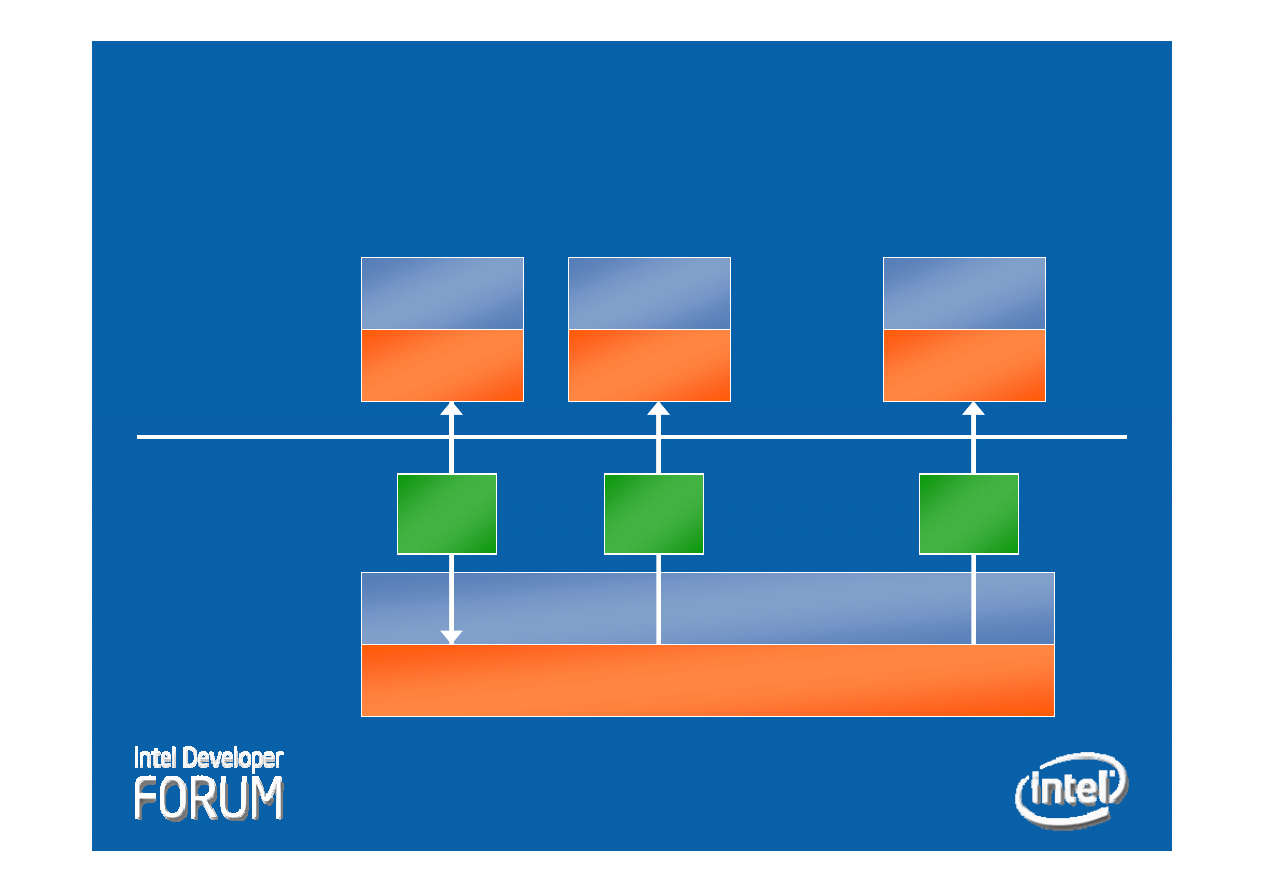
VT
VT
-
-
x Overview
x Overview
IA-32
Operation
Ring 0
Ring 3
VMX Root
Operation
VMX
Non-root
Operation
. . .
Ring 0
Ring 3
VM 1
Ring 0
Ring 3
VM 2
Ring 0
Ring 3
VM n
VMXON
VMLAUNCH
VMRESUME
VM Exit
VMCS
2
VMCS
n
VMCS
1

11
*Third party marks and brands are the property of their respective owners
Some Causes of VMEXIT
Some Causes of VMEXIT
y
y
Paging state exits allow page
Paging state exits allow page
-
-
table control
table control
–
–
Control Register 3 (CR3) accesses
Control Register 3 (CR3) accesses
–
–
INVLPG cause exits
INVLPG cause exits
–
–
Selectively exit on page faults
Selectively exit on page faults
–
–
CR0/CR4 controls allow exiting on changes to
CR0/CR4 controls allow exiting on changes to
selected bits
selected bits
y
y
Controls provided for asynchronous events
Controls provided for asynchronous events
–
–
Host interrupt control allows delivery to VMM
Host interrupt control allows delivery to VMM
even when guest blocking interrupts
even when guest blocking interrupts

12
*Third party marks and brands are the property of their respective owners
VISN Components
VISN Components
y
y
Software agent
Software agent
–
–
Integrity Manifest
Integrity Manifest
y
y
Isolated OS
Isolated OS
–
–
Integrity Measurement Module
Integrity Measurement Module
y
y
Virtual Machine Monitor (VMM)
Virtual Machine Monitor (VMM)
–
–
Memory Protection Module
Memory Protection Module
13
*Third party marks and brands are the property of their respective owners
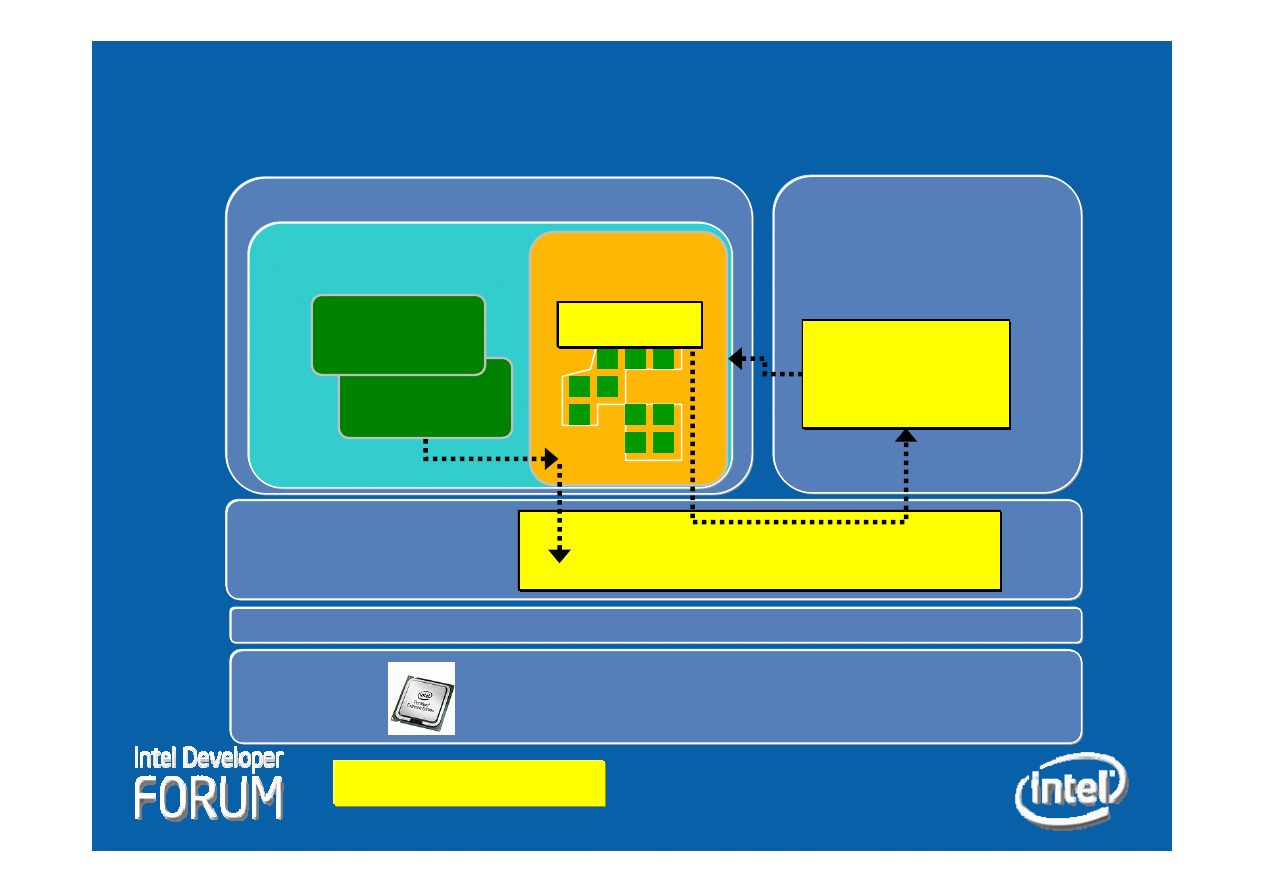
VMM
Integrity Services
and Memory Protections
Isolated environment
Protected
Driver
BIOS
9
Integrity
Measurement
Module
Manifest
Main OS
Other Driver
Malware
X
Kernel
VISN components
VISN Research Prototype
VISN Research Prototype
Hardware
99
99
9 99
99

14
*Third party marks and brands are the property of their respective owners
Integrity Measurement
Integrity Measurement
Module
Module
y
y
Purpose 1
Purpose 1
: Identify, locate and validate programs
: Identify, locate and validate programs
y
y
Purpose 2:
Purpose 2:
Detect modifications of registered
Detect modifications of registered
programs
programs
y
y
IMM is located in an isolated partition
IMM is located in an isolated partition
–
–
Protection offered by VT
Protection offered by VT
–
–
Uses VMM services for locating the agent
Uses VMM services for locating the agent
y
y
Integrity Manifest
Integrity Manifest
–
–
In memory
In memory
cryptographically supported identity
cryptographically supported identity
–
–
Binary format independent
Binary format independent
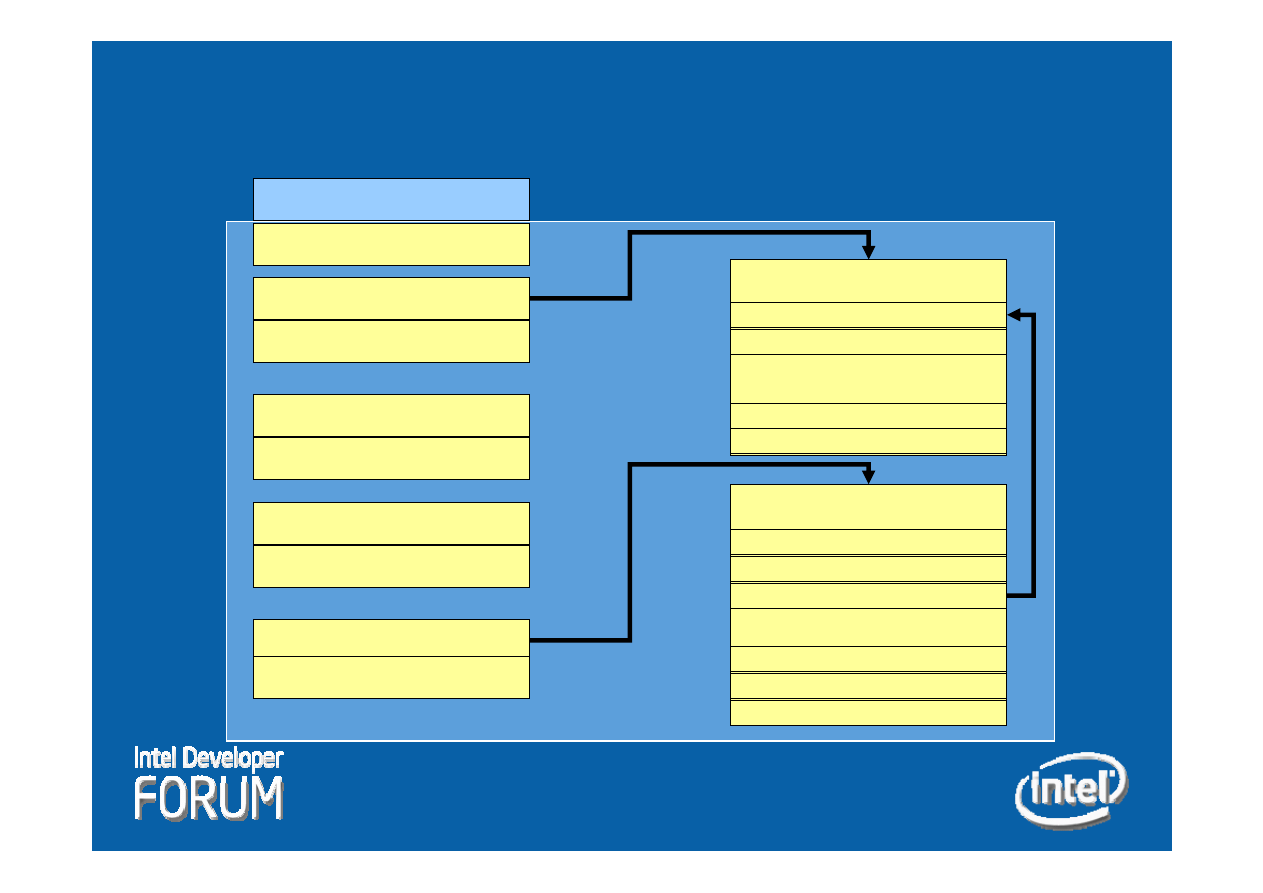
15
*Third party marks and brands are the property of their respective owners
VISN Integrity Manifest
VISN Integrity Manifest
Section Table Offset
Section Table Size
Signature
Size
Symbol Table Offset
Symbol Table Size
String Table Offset
String Table Size
Reloc Table Offset
Reloc Table Size
Section Table
Section Id, Type
Section ICV
Section Id, Type
Section ICV
…
Reloc Table
Reloc symbol
Section, Offset
…
Section, entry
Reloc symbol
Section, Offset
Section, entry
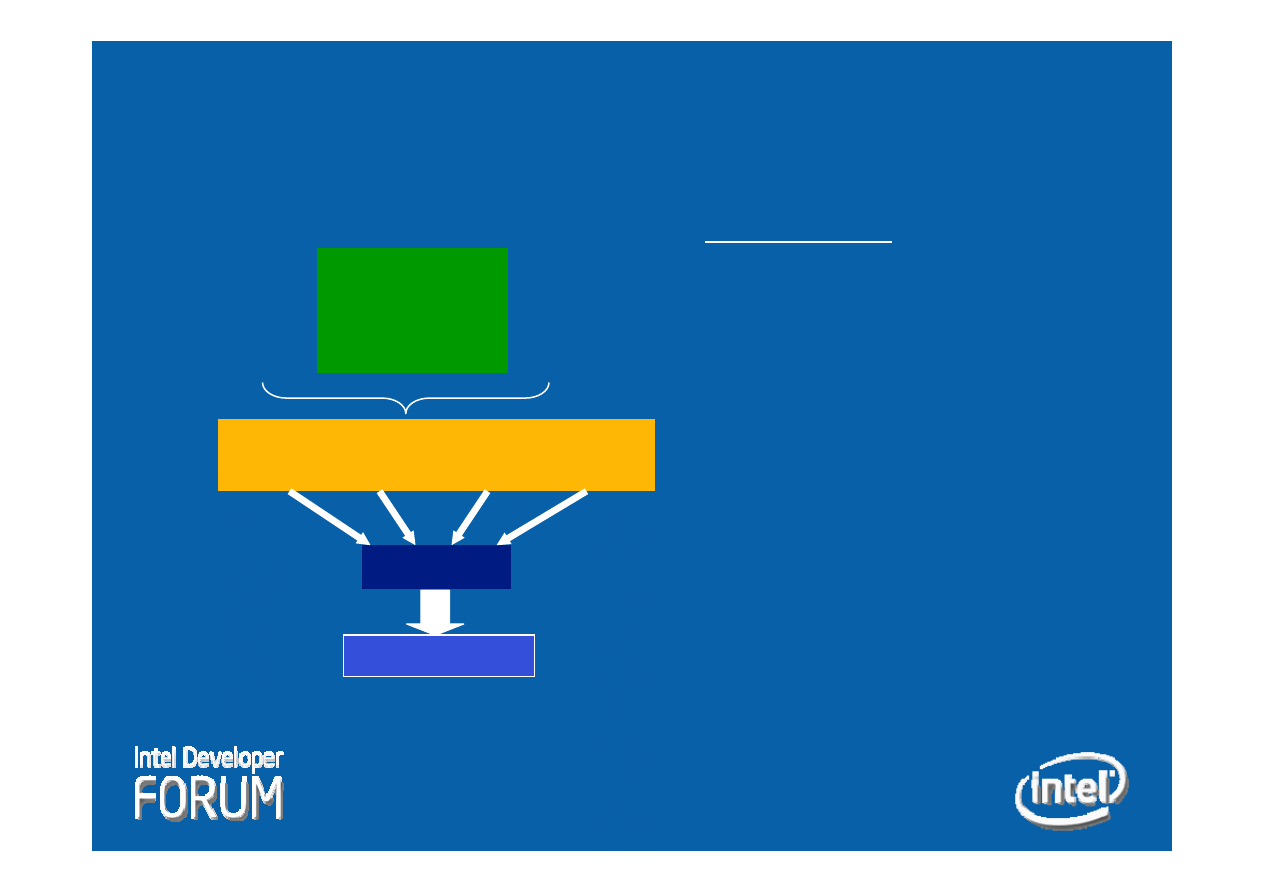
16
*Third party marks and brands are the property of their respective owners
Requirements
-Runtime information
• Relocations
• External symbols
-Cryptographic Signature
-Code and Data Sections
-Code Entry points
-Minimal to no program change
-Creation by Vendor or IT
Integrity Manifest Creation
Integrity Manifest Creation
Manifest
Program
Source/
Image
PE/
ELF
Compile
Link
Code
Update
VISN tools
IT
Config
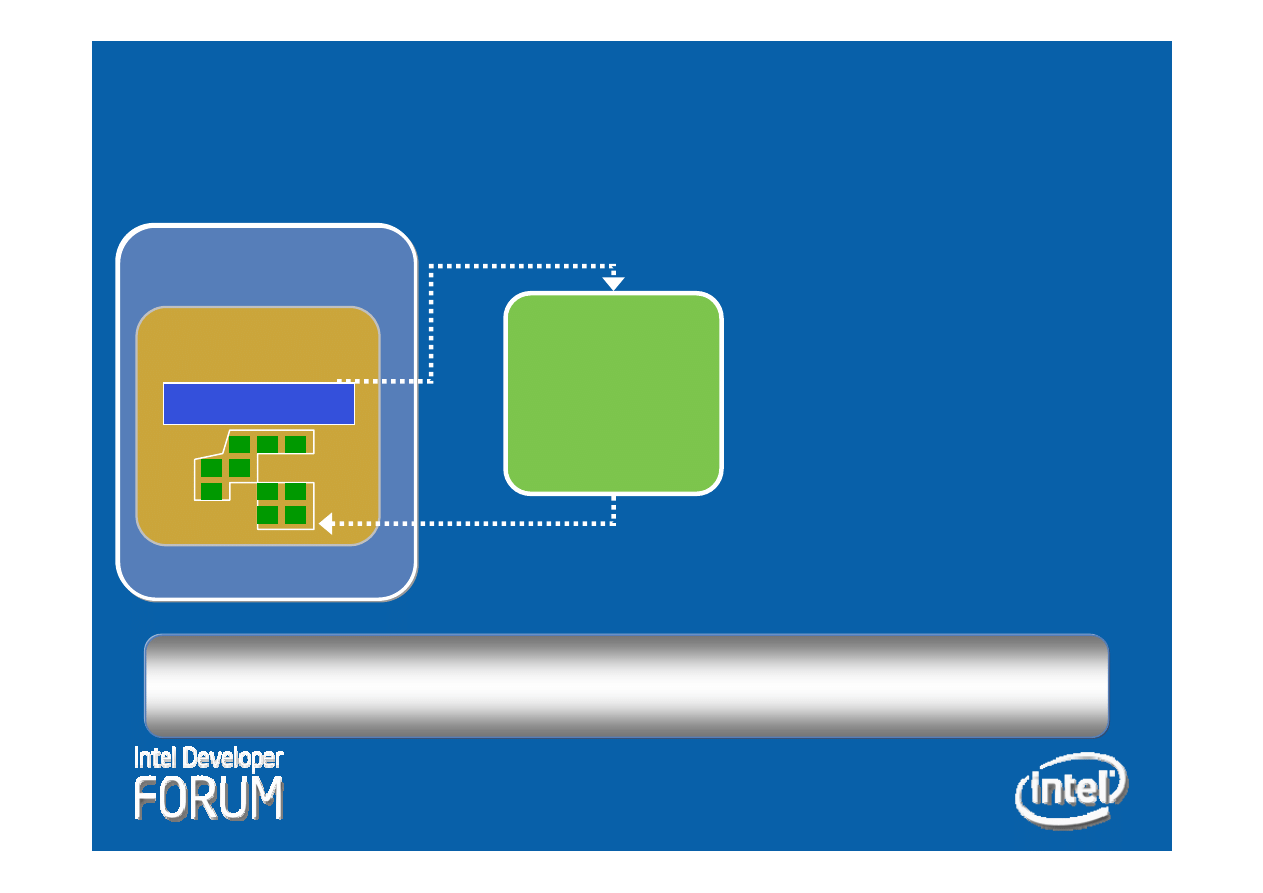
17
*Third party marks and brands are the property of their respective owners
Integrity Measurement
Integrity Measurement
y
y
From isolated VT
From isolated VT
partition
partition
y
y
Unspoofable access
Unspoofable access
to memory
to memory
y
y
Establishes
Establishes
programs location in
programs location in
memory
memory
Measured
Measured
Program
Program
OS kernel
OS kernel
9
9
9
9
9
9
9
9
9
9
9
9
9
9
9
9
9
9
9
9
Integrity
Integrity
Measurement
Measurement
Module
Module
Manifest
Definitively finds and validates platform agents
Definitively finds and validates platform agents

18
*Third party marks and brands are the property of their respective owners
Agenda
Agenda
y
y
Research motivation
Research motivation
y
y
VISN research
VISN research
–
–
VISN Integrity Measurement
VISN Integrity Measurement
–
–
VISN Memory Protections
VISN Memory Protections
y
y
Potential Applications
Potential Applications

19
*Third party marks and brands are the property of their respective owners
VISN Memory Protections
VISN Memory Protections
y
y
Purpose 1
Purpose 1
: Aid in preserving the integrity of
: Aid in preserving the integrity of
valid software agents
valid software agents
y
y
Purpose 2
Purpose 2
: Help ensure valid software
: Help ensure valid software
agents are used the right way
agents are used the right way
–
–
Program Entry points
Program Entry points
–
–
Dynamic data protection
Dynamic data protection
y
y
Resides in the VMM
Resides in the VMM
y
y
Monitors memory accesses
Monitors memory accesses
–
–
Uses VT capabilities for efficiency
Uses VT capabilities for efficiency
20
*Third party marks and brands are the property of their respective owners
IA
IA
-
-
32 Virtual Memory
32 Virtual Memory
(Simplified)
(Simplified)
21
*Third party marks and brands are the property of their respective owners
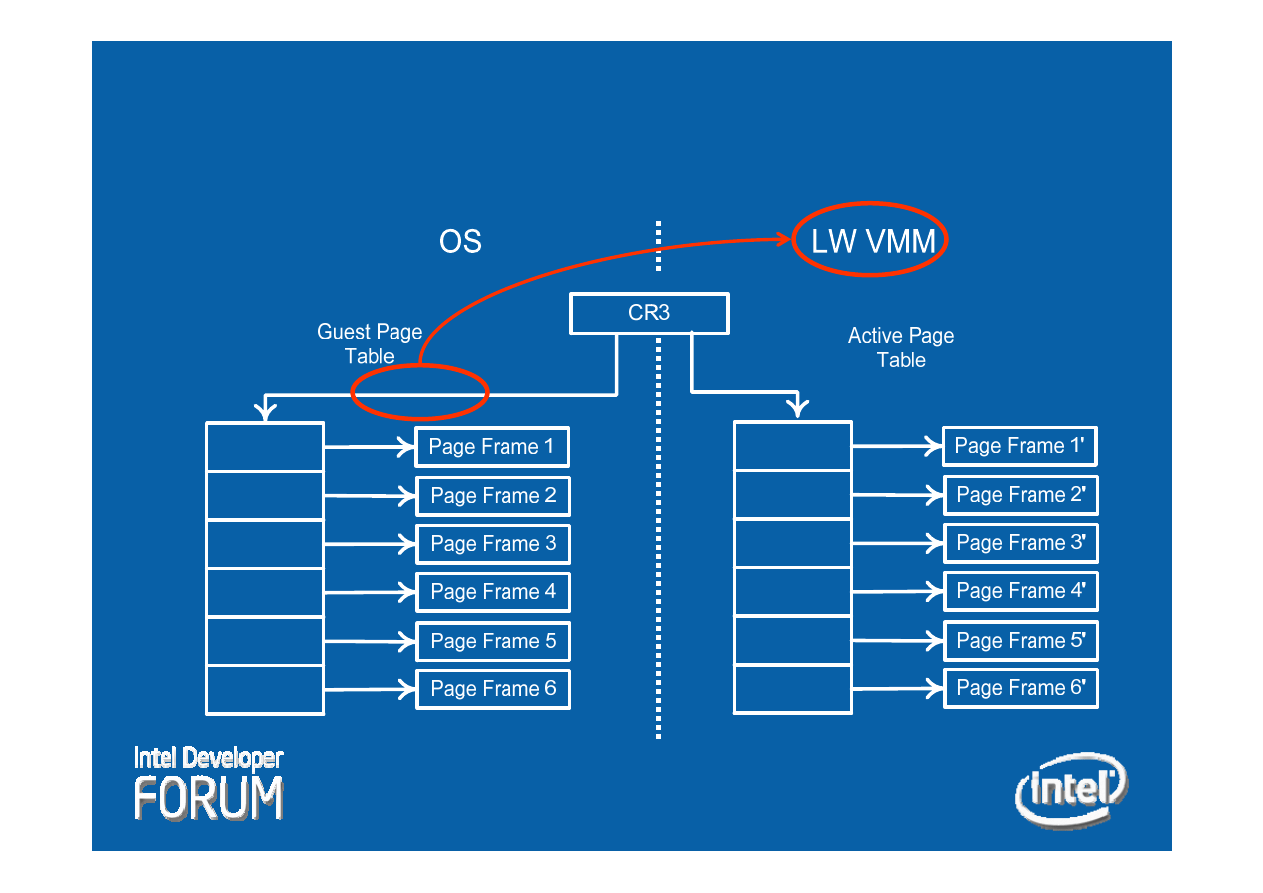
VT Virtual Memory
VT Virtual Memory
(Simplified)
(Simplified)
22
*Third party marks and brands are the property of their respective owners
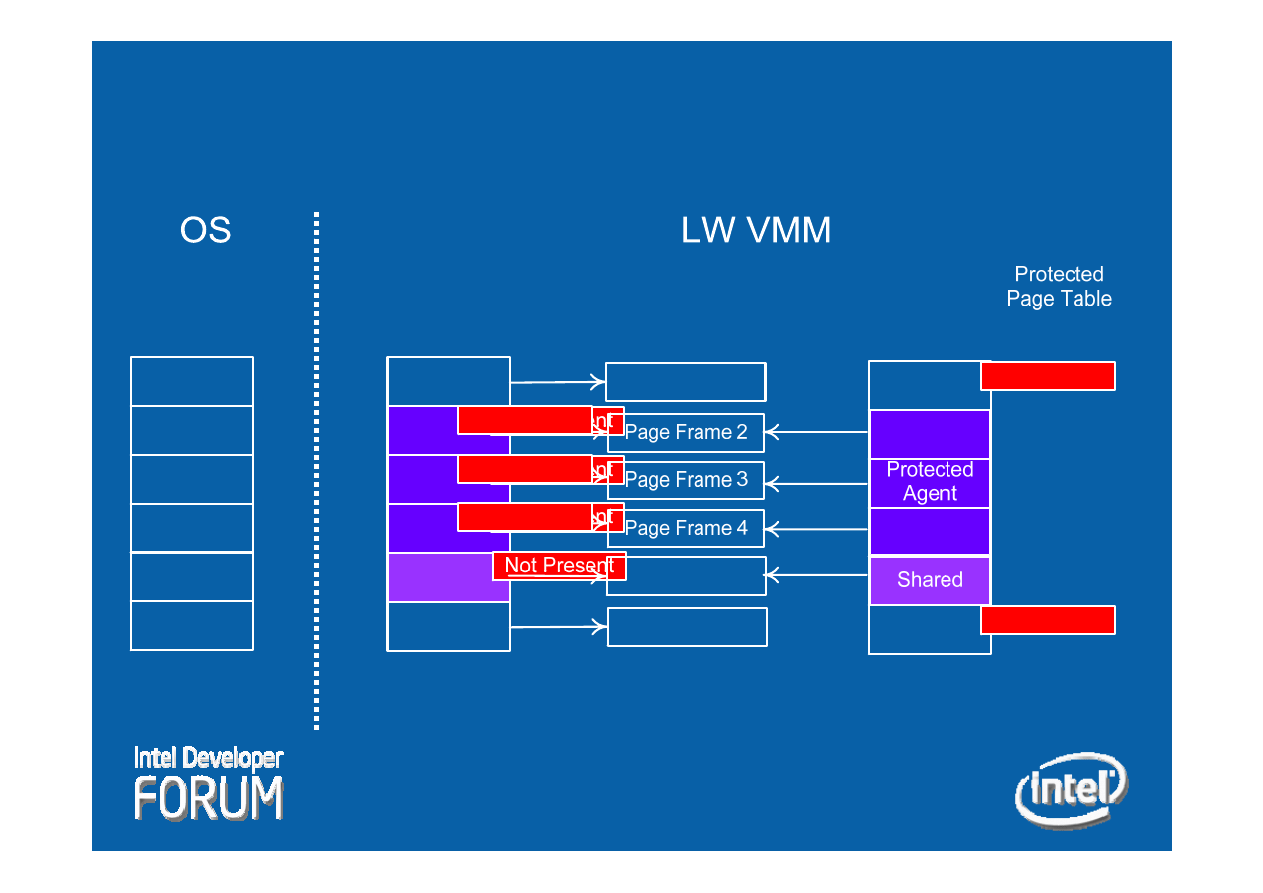
VISN Memory Protection
VISN Memory Protection
-
-
Setup
Setup
Shared
Protected
Agent
Page Frame 1
Page Frame 6
Active Page
Table
Page Frame 5
Not Present
Not Present
Not Present
Not Present
Not Present
Guest Page
Table
23
*Third party marks and brands are the property of their respective owners
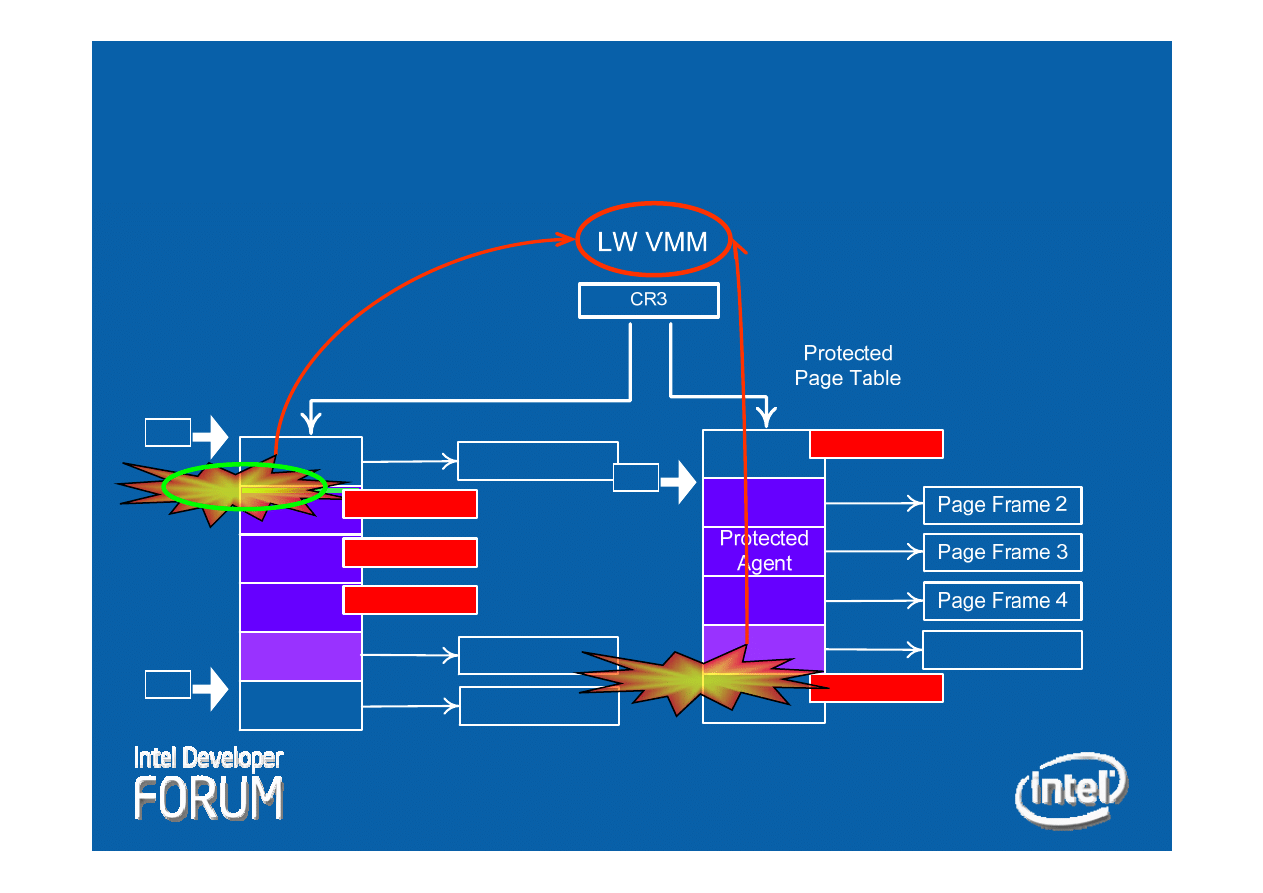
VISN Memory Protection
VISN Memory Protection
-
-
Operation
Operation
Shared
Page Frame 5
Shared
Protected
Agent
Page Frame 1
Page Frame 6
Active Page
Table
Page Frame 5
Not Present
Not Present
EIP
EIP
Page Fault
EIP
Entry-Point
Match
Page Fault
Not Present
Not Present
Not Present
24
*Third party marks and brands are the property of their respective owners
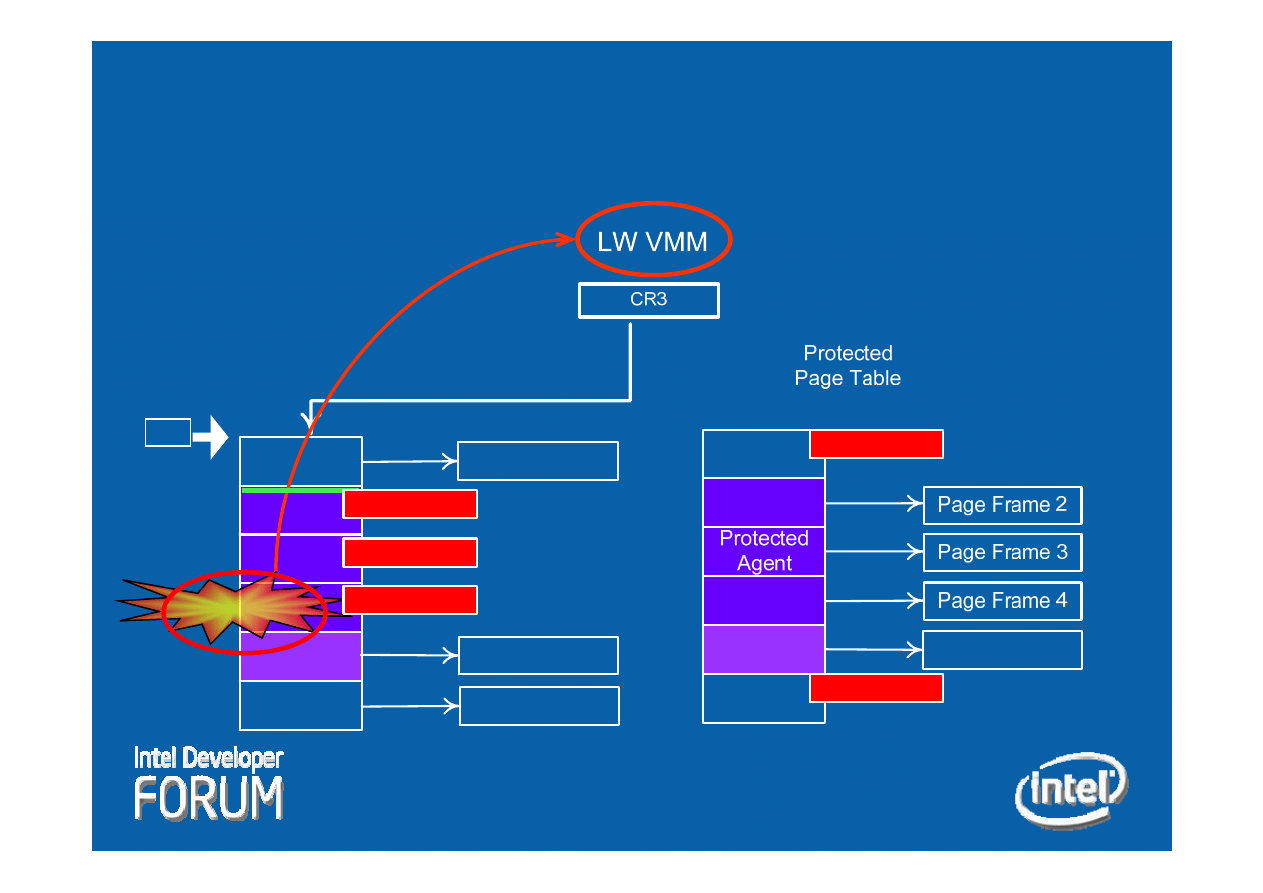
Shared
Page Frame 5
Shared
Protected
Agent
Page Frame 1
Page Frame 6
Active Page
Table
Page Frame 5
Not Present
Not Present
EIP
Page Fault
Entry-Point
Mismatch
Not Present
Not Present
Not Present
VISN Memory Protection
VISN Memory Protection
-
-
Operation
Operation

25
*Third party marks and brands are the property of their respective owners
VISN Features Review
VISN Features Review
y Program integrity verified in memory from isolated
partition
y Program integrity preserved using memory
protections – attacks mitigated
y Program dynamic data and entry points honored –
program use enforced
Prevention
Prevention
of memory attacks and invalid invocation
of memory attacks and invalid invocation

26
*Third party marks and brands are the property of their respective owners
Agenda
Agenda
y
y
Research motivation
Research motivation
y
y
VISN research
VISN research
–
–
VISN Integrity Measurement
VISN Integrity Measurement
–
–
VISN Memory Protections
VISN Memory Protections
y
y
Potential Applications
Potential Applications

27
*Third party marks and brands are the property of their respective owners
Potential Applications
Potential Applications
y
y
Security Software
Security Software
y
y
Device drivers
Device drivers
y
y
Critical OS components
Critical OS components
28
*Third party marks and brands are the property of their respective owners
Thwarting Memory Based
Thwarting Memory Based
Attacks
Attacks
Disable, Circumvent, Eavesdrop, Modify
Disable, Circumvent, Eavesdrop, Modify
Integrity
Msmt
Module
Memory Protections
IM
IM
IM
IM

29
*Third party marks and brands are the property of their respective owners
Summary
Summary
y
y
New attacks target software integrity and
New attacks target software integrity and
presence
presence
y
y
VISN aids in definitively finding and
VISN aids in definitively finding and
validating software agents
validating software agents
y
y
VISN mitigates runtime memory attacks
VISN mitigates runtime memory attacks
and ensures correct usage of agents
and ensures correct usage of agents
y
y
Several applications can benefit from VISN
Several applications can benefit from VISN

30
*Third party marks and brands are the property of their respective owners
Q/A
Q/A
y
y
Additional details at
Additional details at
http://www.intel.com/technology/magazine/research/runtime
http://www.intel.com/technology/magazine/research/runtime
-
-
integrity
integrity
-
-
1205.htm
1205.htm
y
y
Please fill out the session evaluation form
Please fill out the session evaluation form
y
y
Visit the
Visit the
VISN demonstration
VISN demonstration
in the Tech
in the Tech
Showcase, Booth 1003
Showcase, Booth 1003
y
y
Please join us for the
Please join us for the
VISN chalk talk
VISN chalk talk
–
–
3:30
3:30
–
–
4:20 in room 2001A
4:20 in room 2001A
Thank you!
Thank you!

Document Outline
- VT Integrity Services for Networking
- Agenda
- Some Malware Examples
- Effects Of Memory Based Attacks
- New Attacks Require New Approach
- Agenda
- VISN Approach
- VT-x Overview
- Some Causes of VMEXIT
- VISN Components
- Integrity Measurement Module
- VISN Integrity Manifest
- Integrity Manifest Creation
- Integrity Measurement
- Agenda
- VISN Memory Protections
- IA-32 Virtual Memory (Simplified)
- VT Virtual Memory (Simplified)
- VISN Memory Protection - Setup
- VISN Memory Protection - Operation
- VISN Memory Protection - Operation
- VISN Features Review
- Agenda
- Potential Applications
- Thwarting Memory Based Attacks
- Summary
- Q/A
Wyszukiwarka
Podobne podstrony:
Integrated Services Digital Network
10 Integracja NT i NetWare File and Print Services for NetWare
CTX 7130 Citrix NFuse Classic Administration with Enterprise Services for NFuse FR3
Cranenbroeck Advanced Surveying Control Services for Building the Vertical Cities
Amica Servicemanual for PCseries
Multimedia Messaging Service For Gprs And Umts
Integrated Plant for the Municipal Solid Waste of Madrit 01bm 196 1991
Multimedia Messaging Service For Gprs And Umts
System Services for Ad Hoc Routing Architecture, Implementation and68030
n is for network new tools for mapping organizational change
A Low Cost Integrated Approach for Balancing an Array of Piezoresistive Sensors
Windows XP Pro, Configuring for Networks Running Novell NetWare and UNIX
INTEGRATED SYSTEM FOR MULTISTOREY BUILDINGS USE OF SOFTWARE ENGINEERING RULES
ZRESETOWANIE NA WYŚWIETLACZU INFORMACJI SERVICE FOR
10 Integracja NT i NetWare Directory Service Manager for NetWare
więcej podobnych podstron