
Apache Web Login Authentication:
Adding password protection to a web site using Apache web server
authentication.
Tutorial Table of Contents:
#
Apache password file authentication
#
Apache configuration file
#
Password protection by a single login
#
Password protection by group access permissions
#
Restrict access based on domain or IP address
#
Authentication directives placed in httpd.conf exclusively without using .htaccess
#
Using Perl CGI script to manage .htaccess
#
Apache authentication using digest file
#
Apache authentication using LDAP
#
Apache authentication using NIS
#
Apache authentication using MySQL database
#
Login URL trick
#
Other Links
search
|
Home Page
|
Linux Tutorials
|
Terms
|
Privacy Policy
|
Advertising
|
Contact
|
Related YoLinux
Tutorials:
°
Web Site Configuration
°
Apache Authentication
°
NIS configuration
°
LDAP server configuration
°
Linux LDAP authentication
°
Apache Redirect
°
Internet Security
°
Disc Quotas
°
YoLinux Tutorials Index
Apache authentication and autorization Intro:
Apache authentication can be configured to require web site visitors to login with a user id and
password. This is different than adding a login form on a web page and creating your own
authentication. This tutorial describes the various methods available for authentication with Apache
and its' configuration. Login protection is applied to the web pages stored in a directory. The login
dialog box which requests the user id and password is provided by the web browser at the request
of Apache. Apache allows the configuration to be entered in its' configuration files (i.e. main
configuration file
/etc/httpd/conf/httpd.conf
, supplementary configuration files
/etc/httpd
/conf.d/component.conf
or in a file which resides within the directory to be password protected. Five
forms of authentication are detailed here: Apache password file authentication, digest file
authentication, LDAP, NIS and MySQL.
Apache authentication methods using local files to store passwords, have no association with
system user accounts. If using LDAP or NIS for system login authentication, its use can be extended
to support Apache web site logins.
Terms:
Authentication: Prove it is you. Authenticate the login by requiring a password only the user
would know.
Authorization: Only certain users or members of a privaleged group are allowed.
Typically Authentication or Authentication and Authorization are required for access.
Apache configuration files: (refered to generically in this tutorial as
httpd.conf
or reside as the file
.htpasswd, in the directory being protected.)
Red Hat / Fedora Core / CentOS:
/etc/httpd/conf/httpd.conf
or
/etc/httpd/conf.d
/application.conf
Novell SuSE:
/etc/apache2/httpd.conf
or
/etc/apache2/conf.d/application.conf
Ubuntu (dapper 6.06) / Debian:
/etc/apache2/apache2.conf
or
/etc/apache2/conf.d
/application.conf
Apache password file authentication:
Directory protection using .htaccess and .htpasswd
This tutorial applies to Apache based web servers. It requires:
Editing the server configuration file (httpd.conf) to enable/allow a directory structure on the
server to be password protected. Basically the default <Directory> access permission
statement need modification.
1.
The creation and addition of two files specifying the actual logins and passwords. (
.htaccess
and
.htpasswd
)
2.
Use this sparingly because Apache will have to check all directories and subdirectories specified in
the configuration file for the existence of the
.htaccess
file adding to a servers latency.
When trying to access a file in a protected directory, the user will be presented with a window
6
Advertisements
ads
Linux Tutorial - Apache Web Login Authentication:
http://www.yolinux.com/TUTORIALS/LinuxTutorialApacheAddingLog...
1 z 12
2014-01-22 11:16

Free Information
Technology
Magazines and
Document Downloads
(dialog box) requesting a username and password. This protection applies to all sub-directories.
Other
.htaccess
files in sub directories may respecify access rules.
Apache authentication uses the modules
mod_auth
and
mod_access
.
Apache configuration file:
File: /etc/httpd/conf/httpd.conf (older systems used access.conf)
Default: This disables the processing of
.htaccess
files for the system.
<Directory />
AllowOverride None
</Directory>
or for a specified directory:
<Directory /home/domain/public_html>
AllowOverride None
</Directory>
Change to and/or specify directory to protect:
<Directory /home/domain/public_html/membersonly>
AllowOverride All
</Directory>
OR
<Directory /home/domain/public_html/membersonly>
AllowOverride AuthConfig
</Directory>
AllowOverride parameters: AuthConfig FileInfo Indexes Limits Options
The name of the "distributed" and user controlled configuration file
.htaccess
is defined with the
directive: (default shown)
AccessFileName .htaccess
Password protection by a single login:
Password files:
Create the directory you want to password protect (example: membersonly)
1.
Create a file
/home/domain/public_html/membersonly/.htaccess
in that director that looks
something like this:
AuthName "Add your login message here."
AuthType Basic
AuthUserFile /home/domain/public_html/membersonly/.htpasswd
AuthGroupFile /dev/null
require user name-of-user
In this case the "name-of-user" is the login name you wish to use for accessing the web site.
[Pitfall]
The literature is full of examples of the next method but I never got it to work.
One can use Apache directives to specify access and restriction:
AuthName "Add your login message here."
AuthType Basic
AuthUserFile /home/domain/public_html/membersonly/.htpasswd
AuthGroupFile /dev/null
<Limit GET POST>
require user name-of-user
</Limit>
Also see:
List of Apache directives
. If an incorrect directive is used in the
.htaccess
file it will
result in a server error. Check your log files:
/var/log/httpd/error_log
.
The name of the access file
.htaccess
is specified by the httpd.conf directive
AccessFileName
.
2.
Create (or clobber if it already exists) the password file /home/domain/public_html
/membersonly/.htpasswd using the program
htpasswd
:
3.
Logitech 720p
Webcam C905
Logitech
New $88.99
SIIG CB-896111-S2
FireWire 800 9-6
A...
SIIG
New $1.70
D-Link Hi-Speed
USB 2.0 4-Port
Power...
DLite Press
New $21.35
StarTech Parallel
Port PCMCIA Card
STARTECH.COM
New $46.24
SteelSeries Zboard
Gaming Keyboard
SteelSeries
New $24.99
HP 57 Tri-Color
Inkjet Print Cartrid...
hp
New $24.95
Privacy Information
Jobs
Software QA Analyst
New York, NY
Adecco
Senior Security Analyst
Norcross, GA
AGILE
Sr. Software
Development Engineer...
Beijing, Guangdong,
China
Microsoft
Senior Java Developer
contract -...
Letterkenny, Donegal,
Ireland
E-Frontiers
Java Software Engineer
Chicago, IL
Request Technology
Software Engineer
Bangalore, Karnataka,
India
Intel
Senior Tech
Programmer needed
for...
Netherlands
Interactive Selection
SharePoint systems
administrator
New York, NY
C++ and .Net developer
boston, MA
Iconsoft
Software Development
Engineer (SDE) 2
Hyderabad, Andhra
Pradesh, India
Microsoft
POST A JOB >
POWERED BY JOBTHREAD
►
Apache 2.0 SSL
►
Apache
►
Authentication
Linux Tutorial - Apache Web Login Authentication:
http://www.yolinux.com/TUTORIALS/LinuxTutorialApacheAddingLog...
2 z 12
2014-01-22 11:16

htpasswd -c .htpasswd name-of-user
Add a new user to the existing password file:
htpasswd .htpasswd name-of-user
Man page:
htpasswd
Example file:
.htpasswd
user1:KgvCSeExtS4kM
USER1:KgvCSeExtS4kM
User1:KgvCSeExtS4kM
Password file protection, ownership and SELinux attributes:
File privileges:
chmod ug+rw .htpasswd
File ownership:
chown apache.apache .htpasswd
SELinux file attributes:
chcon -R -h -u system_u -r object_r -t httpd_config_t .htpasswd
This is required so that the Apache web server can access the password file.
Flexible password protection by group access permissions:
This example differs from the previous example in that it allows for greater control and flexibility by
using groups.
Password files:
Create a file
.htgroup
in that directory that contains the groupname and list of users:
member-users: user1 user2 user3 ... etc
Where member-users is the name of the group.
1.
Modify
.htaccess
in the membersonly directory so it looks something like:
AuthName "Add your login message here."
AuthType Basic
AuthUserFile /home/domain/public_html/membersonly/.htpasswd
AuthGroupFile /home/domain/public_html/membersonly/.htgroup
require group member-users
2.
Create the password file
.htpasswd
using the program
htpasswd
for each user as above. You
don't need the -c option if you are using the same
.htpasswd
file. (-c is only to create a new
file)
htpasswd -c /home/domain/public_html/membersonly/.htpasswd user1
htpasswd /home/domain/public_html/membersonly/.htpasswd user2
3.
Restrict access based on domain or IP address:
Allow specified domain to access site:
Order deny, allow
Deny from all
Allow from allowable-domain.com
Allow from XXX.XXX.XXX
Deny from evil-domain.com
Specify first three (or one, or two, ...) octets of IP address defining allowable domain.
Placing Authentication directives in httpd.conf exclusively instead of using
.htaccess:
The purpose of using the "distributed configuration file"
.htaccess
is so that users may control
authentication. It can also be set in the Apache configuration file
httpd.conf
WITHOUT using the
.htaccess
file. This can improve server performance as the server will not have to look for the
.htaccess
file in each subdirectory.
File:
httpd.conf
(portion)
..
...
<Directory /home/domain/public_html/membersonly>
AllowOverride AuthConfig
AuthName "Add your login message here."
AuthType Basic
AuthUserFile /home/domain/public_html/membersonly/.htpasswd
Linux Tutorial - Apache Web Login Authentication:
http://www.yolinux.com/TUTORIALS/LinuxTutorialApacheAddingLog...
3 z 12
2014-01-22 11:16
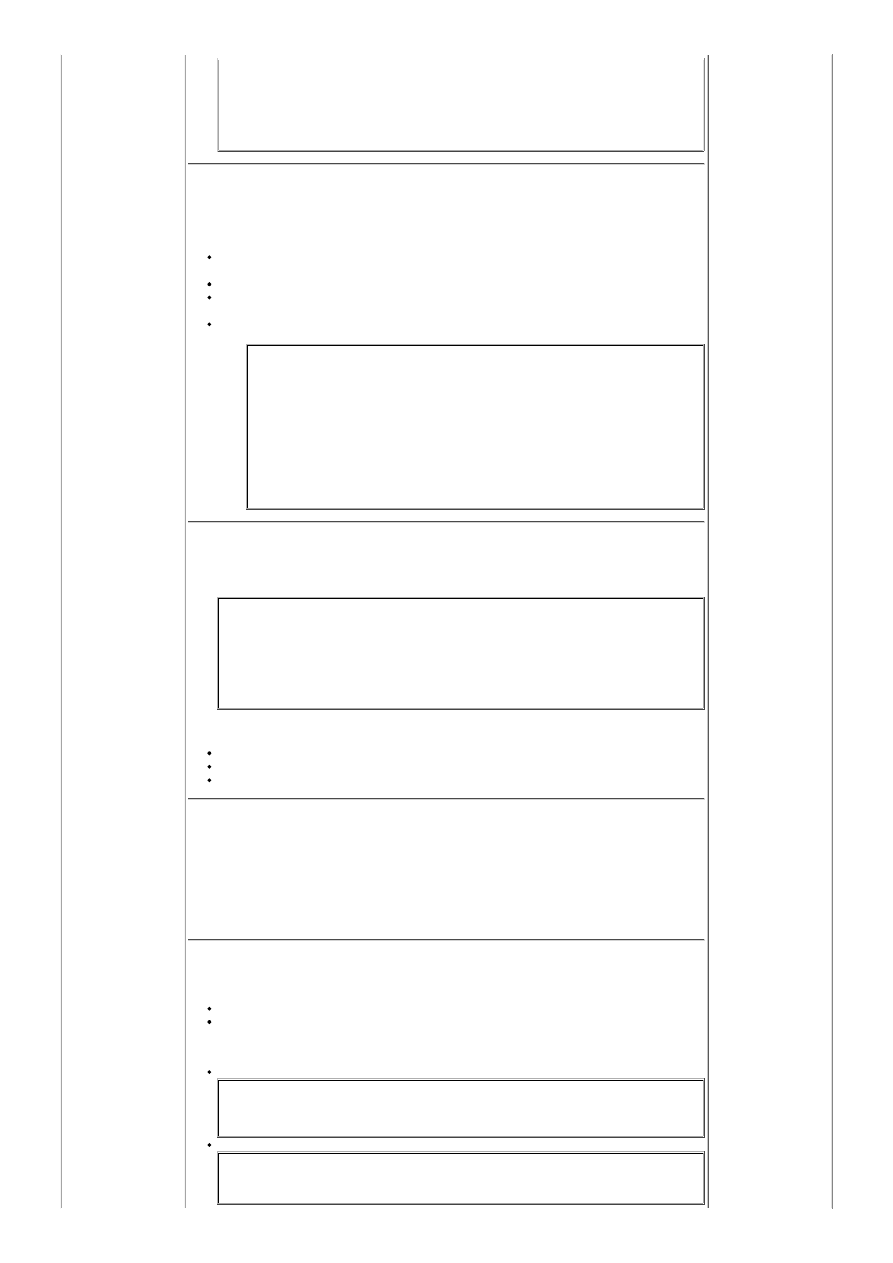
AuthGroupFile /dev/null
require user name-of-user
</Directory>
...
..
Perl CGI Script to Modify User Passwords:
This allows users to manage / change their own passwords.
Use the Perl CGI script
htpasswd.pl
[
cache
]
Edit location of Perl .i.e.:
/usr/bin/perl
Not
/usr/local/bin/perl
Edit the script to specify location of the password file i.e.
/var/www/PasswordDir/.htpasswd
SELinux users must add the correct attribute i.e.
chcon -R -h -t httpd_sys_content_t
/var/www/PasswordDir
The password file must be located in a directory where CGI is allowed to modify files.
File:
httpd.conf
(portion)
..
...
<Directory "/var/www/PasswordDir">
Options -Indexes
AllowOverride None
Options None
Order allow,deny
Allow from all
</Directory>
...
..
Using Digest File for Apache Authentication:
This method authenticates a user login using Apache 2.0 on Linux. The logins have no connection
to user accounts.
<Location /home/domain/public_html/membersonly>
AuthType Digest
AuthNAme "Members Only Area"
AuthDigestDomain /home/domain/public_html/membersonly
AuthDigestFile /etc/httpd/conf/digestpw
require valid-user
</Location>
For more on digest authentication see:
Apache.org: Module mod_auth_digest
RFC 2617: HTTP Authentication: Basic and Digest Access Authentication
Man page:
htdigest
Using LDAP for Apache Authentication:
This method authenticates using Apache 2.0/2.2 and the LDAP authentication modules on Linux
(supplied by default with most Linux distros) and an LDAP server. LDAP can be used to authenticate
user accounts on Linux and other computer systems as well as web site logins.
Also see
YoLinux TUTORIAL: LDAP system authentication
.
Try this out with your Apache server authenticating to our open LDAP server using our Three
Stooges example.
Apache LDAP modules:
Note that the following configurations work if the LDAP modules are enabled:
Apache 2.0 (Red Hat Enterprise 4/CentOS4):
mod_ldap
,
mod_auth_ldap
Apache 2.2 (Red Hat Enterprise 5/CentOS 5):
mod_ldap
,
mod_authnz_ldap
These are turned on by default. See
/etc/httpd/conf/httpd.conf
Apache 2.0:
LoadModule ldap_module modules/mod_ldap.so
LoadModule auth_ldap_module modules/mod_auth_ldap.so
Apache 2.2:
LoadModule ldap_module modules/mod_ldap.so
LoadModule authnz_ldap_module modules/mod_authnz_ldap.so
Linux Tutorial - Apache Web Login Authentication:
http://www.yolinux.com/TUTORIALS/LinuxTutorialApacheAddingLog...
4 z 12
2014-01-22 11:16
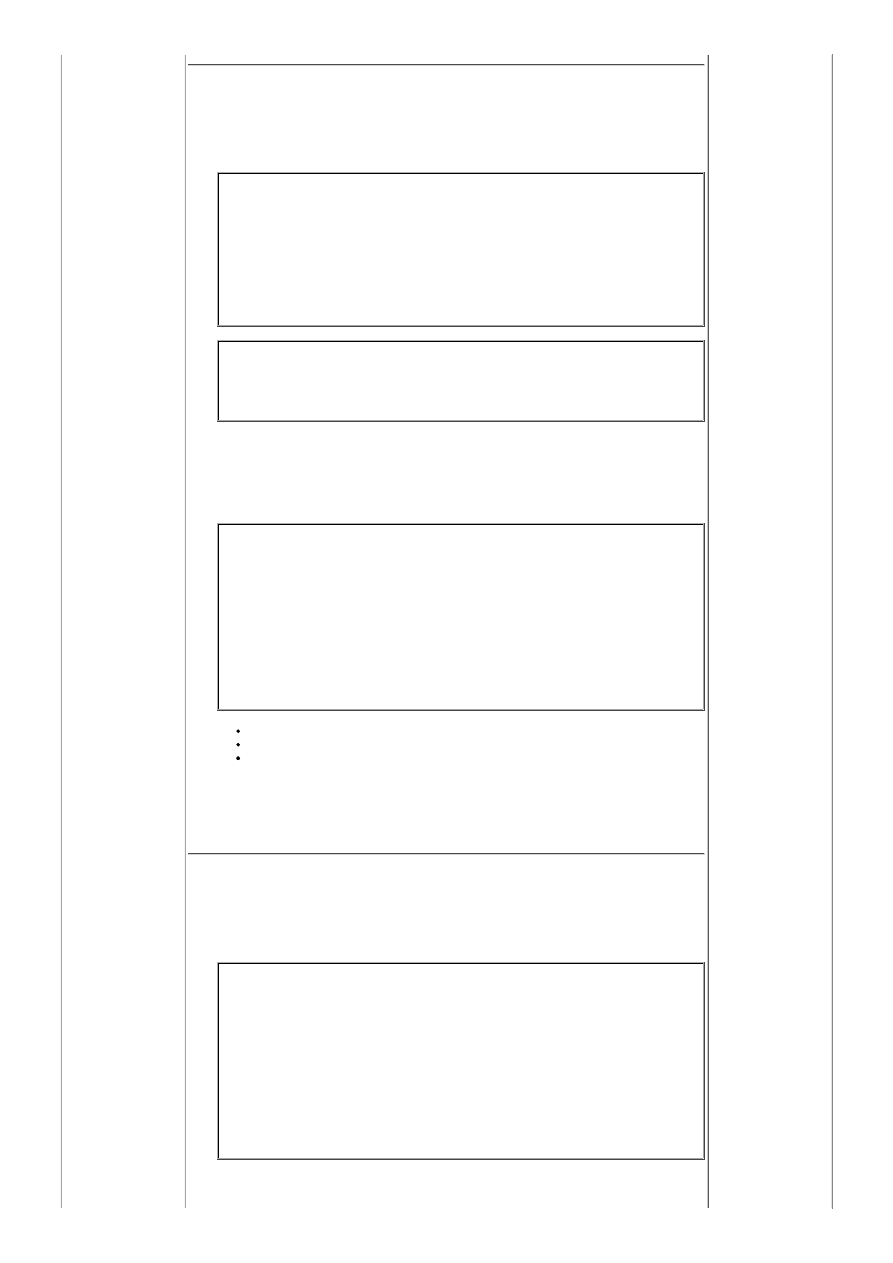
Apache Authentication Configuration:
Apache 2.0:
Authenticate to an Open LDAP server. (No bind name/password required to access LDAP server)
File:
httpd.conf
(portion)
..
...
<Directory /var/www/html>
AuthType Basic
AuthName "Stooges Web Site: Login with email address"
AuthLDAPURL ldap://ldap.yolinux.com:389/o=stooges?mail
require valid-user
</Directory>
...
..
or create the file
/var/www/html/.htaccess
AuthName "Stooges Web Site: Login with email address"
AuthType Basic
AuthLDAPURL ldap://ldap.your-domain.com:389/o=stooges?mail
require valid-user
Point your browser to
http://localhost/
Login with the user id "LFine@isp.com" and password "larrysecret".
You will be asked to use a user id (email address) and password to enter the site.
Bind with a bind DN: (password protected LDAP repository)
File:
httpd.conf
(portion)
..
...
<Directory /var/www/html>
AuthType Basic
AuthName "Stooges Web Site: Login with email address"
AuthLDAPEnabled on
AuthLDAPURL ldap://ldap.your-domain.com:389/o=stooges?mail
AuthLDAPBindDN "cn=StoogeAdmin,o=stooges"
AuthLDAPBindPassword secret1
require valid-user
</Directory>
...
..
Examples:
require valid-user
: Allow all users if authentication (password) is correct.
require user greg phil bob
: Allow only greg phil bob to login.
require group accounting
: Allow only users in group "accounting" to authenticate.
For this LDAP authentication example to work, configure your LDAP server with our
YoLinux
Three Stooges example
and set the password in the
/etc/openldap.slapd.conf
file.
This example specified the use of the email address as a login id. If using user id's specify:
AuthLDAPURL ldap://ldap.your-domain.com:389/o=stooges?uid
Apache 2.2:
Authenticate using Apache httpd 2.2 AuthzLDAP:
User Authentication:
File:
httpd.conf
(portion)
..
...
<Directory /var/www/html>
AuthType Basic
AuthName "Stooges Web Site: Login with user id"
AuthBasicProvider ldap
AuthzLDAPAuthoritative on
AuthLDAPURL ldap://ldap.your-domain.com:389/o=stooges?uid?sub
AuthLDAPBindDN "cn=StoogeAdmin,o=stooges"
AuthLDAPBindPassword secret1
require ldap-user lary curley moe joe bob mary
</Directory>
...
..
There are two configurations for the directive
AuthzLDAPAuthoritative
:
Linux Tutorial - Apache Web Login Authentication:
http://www.yolinux.com/TUTORIALS/LinuxTutorialApacheAddingLog...
5 z 12
2014-01-22 11:16
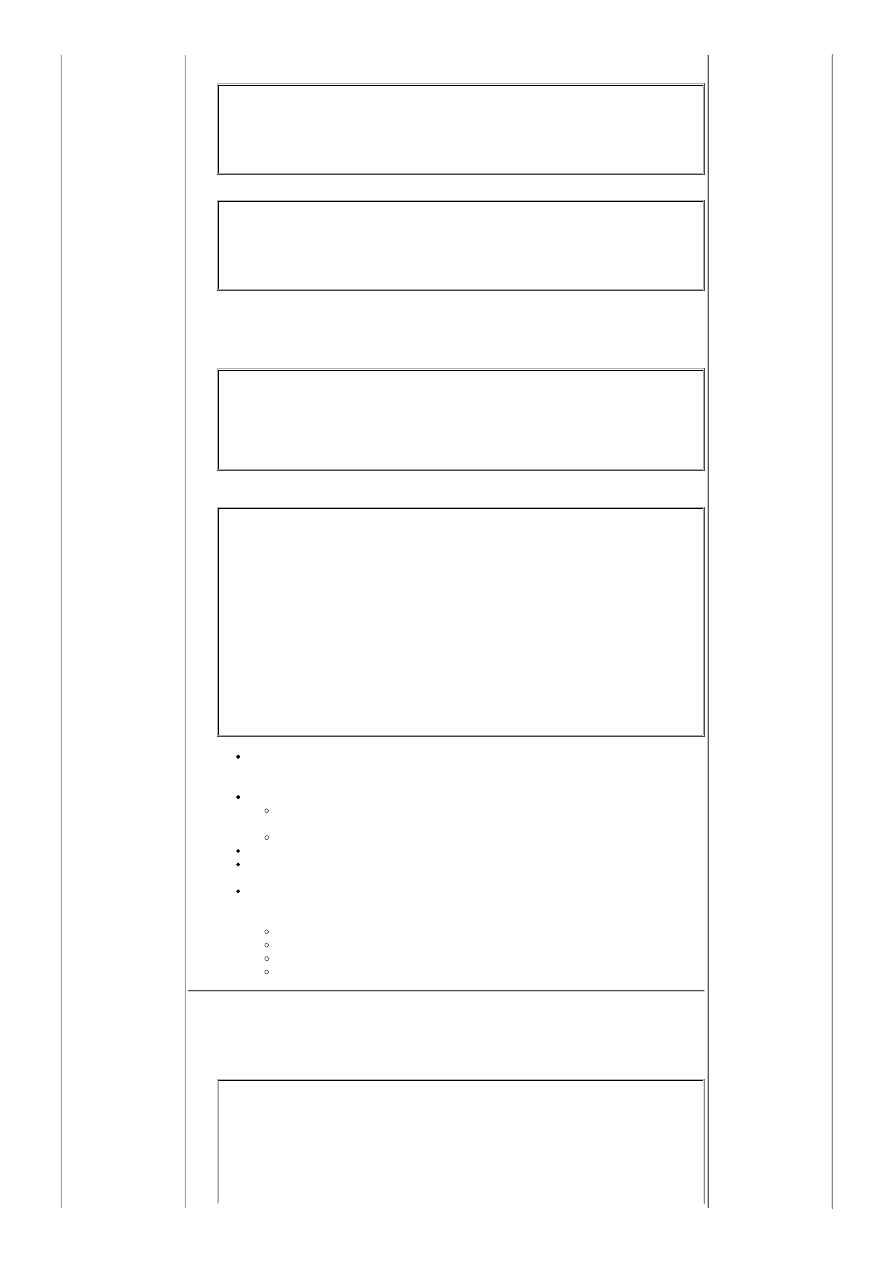
AuthzLDAPAuthoritative on
(default)
AuthzLDAPAuthoritative on
...
require ldap-user lary curley moe joe bob mary
AuthzLDAPAuthoritative off
AuthzLDAPAuthoritative off
...
require valid-user
This configuration allows a waterfall of other authentication methods to be employed along
side LDAP.
Group Authentication:
LDAP LDIF file: (part of our
stooges example
)
dn: cn=users,ou=group,o=stooges
cn: users
objectClass: top
objectClass: posixGroup
gidNumber: 100
memberUid: larry
memberUid: moe
Apache Configuration:
...
<Directory /var/www/html>
Order deny,allow
Deny from All
AuthType Basic
AuthName "Stooges Web Site: Login with user id"
AuthBasicProvider ldap
AuthzLDAPAuthoritative on
AuthLDAPURL ldap://ldap.your-domain.com:389/o=stooges?uid?sub
AuthLDAPBindDN "cn=StoogeAdmin,o=stooges"
AuthLDAPBindPassword secret1
AuthLDAPGroupAttribute memberUid
AuthLDAPGroupAttributeIsDN off
Require ldap-group cn=users,ou=group,o=stooges
Require ldap-attribute gidNumber=100
Satisfy any
</Directory>
...
Note:
Allow users (LDAP attribute:
memberUid
) in group
gidNumber: 100
of
objectClass:
posixGroup
which match to the login
uid
, authentication approval.
The directive
AuthLDAPGroupAttribute
identifies the attribute to match with the login
uid
.
AuthLDAPGroupAttributeIsDN:
on (default): Use DN (Distinguished name)
cn=Moe
Howard,ou=MemberGroupA,o=stooges
off: Use username
moe
Multiple
Require ldap-group ...
statements may be included to allow multiple groups.
Multiple
Require ldap-attribute ...
statements may be included to allow multiple
groups.
The directive
Satisfy any
is required if testing multiple conditions. Only one positive in
any of the conditions is required to authenticate. Thus you can combine the following
authorization schemes as well:
Require ldap-user
Require ldap-dn
Require ldap-attribute
Require ldap-filter
Concurrent File and LDAP authentication:
Apache can use both File and LDAP authentication concurently. This is sometimes required to run
cron jobs with a login where you do not want to use a system login or login managed by a directory
server in another department.
<Directory /ABC>
Order deny,allow
Deny from All
AuthType Basic
AuthBasicProvider file ldap
AuthName "Directory services login"
AuthBasicAuthoritative off
AuthUserFile /srv/htpasswd
AuthGroupFile /dev/null
AuthzLDAPAuthoritative off
Linux Tutorial - Apache Web Login Authentication:
http://www.yolinux.com/TUTORIALS/LinuxTutorialApacheAddingLog...
6 z 12
2014-01-22 11:16
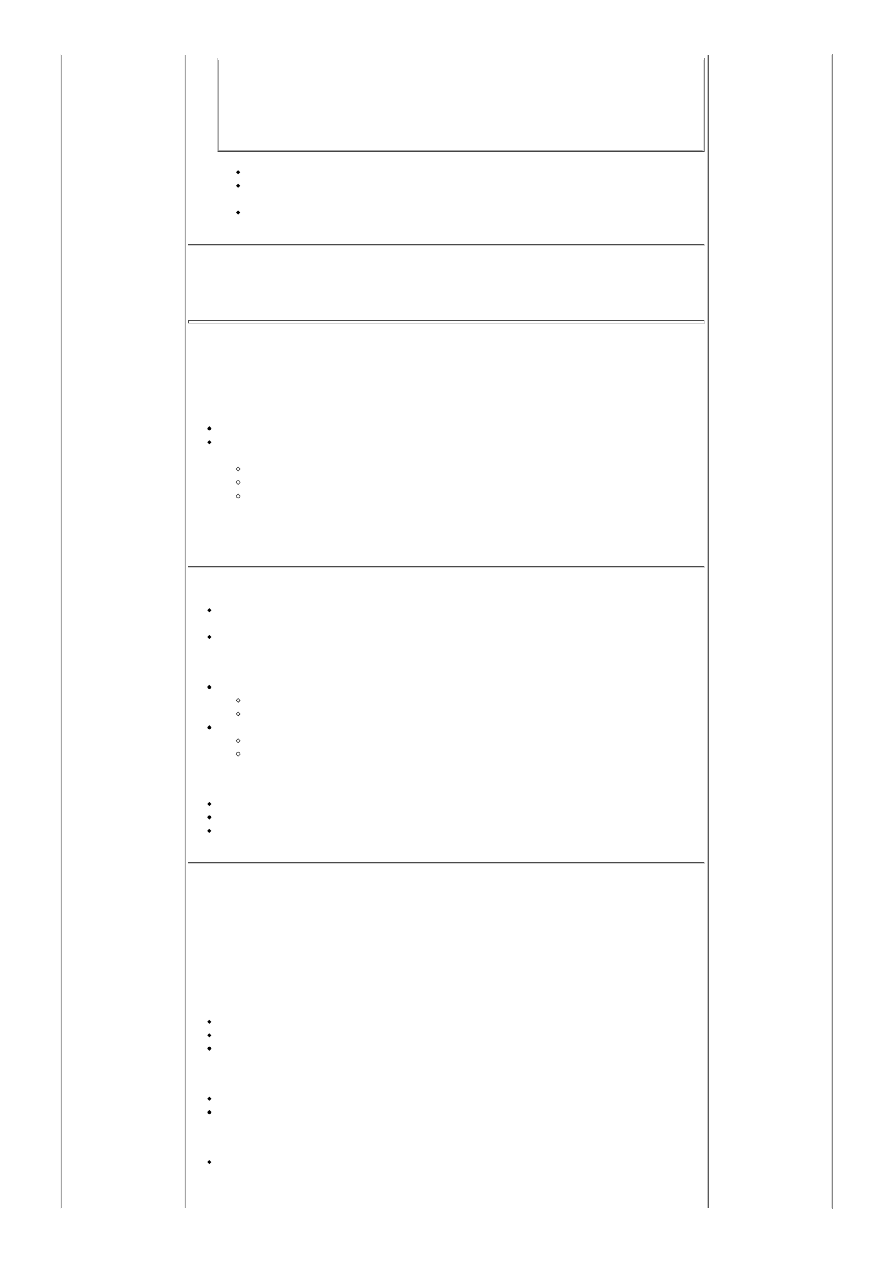
AuthLDAPURL "ldap://ldap.megacorp.com:389/ou=person,o=megacorp.com,c=us?uid?sub"
# This user created for local cron jobs. It is not a system user and allows
# the cron job to perform its task.
# This user is not in the LDAP directory but in the password file /srv/htpasswd
Require user cronuserjobx
Require ldap-user usera userb
</Directory>
Note:
AuthBasicProvider file ldap
- Check password "file" authentication then LDAP
AuthBasicAuthoritative off
- Allows fall back to another auth scheme, in this case
LDAP
AuthzLDAPAuthoritative off
- Allows fall back to other auth scheme besides LDAP, in
this case file
Debugging Apache Authentication:
Set
LogLevel debug
when debugging authentication. This will log all the LDAP connection events
and the LDAP attributes requested.
Authenticating with Microsoft Active directory using Microsoft's "Unix services for Windows":
AuthLDAPURL ldap://ldap.your-domain.com:389
/ou=Employees,ou=Accounts,dc=sos,dc=com?sAMAccountName?sub
Also note that encrypted connections will use the URL prefix "
ldaps://
" and the added directives:
LDAPTrustedCA directory-path/filename
LDAPTrustedCAType type
Where the "type" is one of:
DER_FILE: file in binary DER format
BASE64_FILE: file in Base64 format
CERT7_DB_PATH: Netscape certificate database file
Restart Apache after editing the configuration file:
service httpd restart
for configuration changes
to take effect.
See
/var/log/httpd/error_log
for configuration errors.
Links:
YoLinux Tutorial: Configuration of an LDAP server
- includes a quick start example using the
Three Stooges.
YoLinux Tutorial: Apache web server configuration
Apache documentation:
Apache 2.0:
mod_ldap
mod_auth_ldap
Apache 2.2:
mod_ldap
mod_authnz_ldap
Other LDAP modules:
Apache LDAP module auth_ldap
- (Apache 1.3)
Apache LDAP module mod_ldap_userdir
(Apache 2.x)
Apache mod_auth_ldap
web server module for authentication with Netscape or OpenLDAP
servers (HowTo)
Using NIS for Apache Authentication:
This method authenticates using Apache on Linux and an NIS server. The advantage of using NIS,
is the comonality of computer system accounts and web site logins. This configuration requires that
the system the Apache web server is running on, must be using NIS authentication for system
logins.
This requires a NIS server. See the
YoLinux.com NIS configuration tutorial
.
Requires the Linux RPM package
mod_perl
and the following Perl modules:
ExtUtils-AutoInstall
Net-NIS
Apache2-AuthenNIS or Apache-AuthenNIS
The version of Apache determines which Perl modules to use:
Apache 2.2 (RHEL5, CentOS5, FC6): Use the Perl module Apache2-AuthenNIS.
Apache 2.0 (RHEL4, CentOS4, FC3): Use the Perl module Apache-AuthenNIS.
Download / Install Perl modules:
Download "ExtUtils-AutoInstall" as an RPM from
RepoForge
RPMs:
perl-ExtUtils-AutoInstall-
0.63-1.2.el4.rf.noarch.rpm
Install:
rpm -ivh perl-ExtUtils-AutoInstall-0.63-1.2.el4.rf.noarch.rpm
Linux Tutorial - Apache Web Login Authentication:
http://www.yolinux.com/TUTORIALS/LinuxTutorialApacheAddingLog...
7 z 12
2014-01-22 11:16
Net-NIS
: (
CPAN
)
tar xzf Net-NIS-0.34.tar.gz
cd Net-NIS-0.34/
perl Makefile.PL
make
make install
Apache(2)-AuthenNIS:
Apache 2.2
Apache 2.0
Apache2-AuthenNIS
: (
CPAN
)
tar xzf Apache2-AuthenNIS-0.15.tar.gz
cd Apache2-AuthenNIS-0.15
perl Makefile.PL
make
make install
Apache-AuthenNIS
: (
CPAN
)
tar xzf Apache-AuthenNIS-0.13.tar.gz
cd Apache-AuthenNIS-0.13
perl Makefile.PL
make
make install
Or install from CPAN via the internet:
perl -MCPAN -e shell
(Answer no)
install ExtUtils::AutoInstall
install Net::NIS
install Apache2::AuthenNIS (or Apache::AuthenNIS)
quit
Test Perl module:
File:
testApache2AuthenNIS.pl
#!/usr/bin/perl
BEGIN{push @INC, "/usr/lib/perl5/site_perl/5.8.8/Apache2";}
eval "use Apache2::AuthenNIS"; $hasApacheAuth = $@ ? 0 : 1;
printf "Apache2::AuthenNIS". ($hasApacheAuth ? "" : " not") . " installed";
printf "\n";
Test:
[root]# ./testApache2AuthenNIS.pl
Good:
Apache2::AuthenNIS installed
Not good:
Apache2::AuthenNIS not installed
OR
File:
testApacheAuthenNIS.pl
#!/usr/bin/perl
BEGIN{push @INC, "/usr/lib/perl5/site_perl/5.8.5/Apache";}
eval "use Apache::AuthenNIS"; $hasApacheAuth = $@ ? 0 : 1;
printf "Apache::AuthenNIS". ($hasApacheAuth ? "" : " not") . " installed";
printf "\n";
Test:
[root]# ./testAuthenNIS.pl
Good:
Apache::AuthenNIS installed
Not good:
Apache::AuthenNIS not installed
Apache NIS authentication Examples:
require valid-user
: Allow all users if authentication (password) is correct.
1.
require user greg phil bob
: Allow only greg phil bob to login.
2.
require group accounting
: Allow only users in group "accounting" to authenticate.
3.
1) Restric access to NIS authenticated users:
Apache Configuration File:
httpd.conf
(portion)
..
...
<Directory /home/domain/public_html/membersonly>
AuthType Basic
AuthName "Add your login message here."
PerlAuthenHandler Apache2::AuthenNIS - or Apache::AuthenNIS
PerlSetVar AllowAlternateAuth no
require valid-user
</Directory>
...
..
2) Restrict to listed users greg, phil and bob, but still authenticate to NIS:
Apache Configuration File:
httpd.conf
(portion)
..
...
<Directory /home/domain/public_html/membersonly>
AuthType Basic
Linux Tutorial - Apache Web Login Authentication:
http://www.yolinux.com/TUTORIALS/LinuxTutorialApacheAddingLog...
8 z 12
2014-01-22 11:16
AuthName "Add your login message here."
PerlAuthenHandler Apache2::AuthenNIS - or Apache::AuthenNIS
PerlSetVar AllowAlternateAuth no
require user greg phil bob
</Directory>
...
..
3) Restrict access to NIS members of a specific NIS group:
Apache Configuration File:
httpd.conf
(portion)
..
...
<Directory /home/domain/public_html/membersonly>
AuthType Basic
AuthName "Add your login message here."
PerlAuthenHandler Apache2::AuthenNIS - or Apache::AuthenNIS
PerlAuthzHandler Apache2::AuthzNIS - or Apache::AuthzNIS
PerlSetVar AllowAlternateAuth no
require group accounting
</Directory>
...
..
Note Apache2::AuthzNIS only checks for group membership by group name (not GID).
Apache2::AuthenNIS still required to authenticate the user (check password).
Example showing password protection for user web directories:
Apache Configuration File:
httpd.conf
(portion)
..
...
<IfModule mod_userdir.c>
UserDir public_html
</IfModule>
<Directory /home/*/public_html>
AuthType Basic
AuthName "Add your login message here."
PerlAuthenHandler Apache2::AuthenNIS - or Apache::AuthenNIS
PerlSetVar AllowAlternateAuth no
require user valid-user
AllowOverride FileInfo AuthConfig Limit
Options MultiViews Indexes SymLinksIfOwnerMatch IncludesNoExec
<Limit GET POST OPTIONS>
Order allow,deny
Allow from all
</Limit>
<LimitExcept GET POST OPTIONS>
Order deny,allow
Deny from all
</LimitExcept>
</Directory>
...
..
Also see
YoLinux SysAdmin: Perl Admin
Links:
NIS+ (More secure than NIS):
Apache::AuthenNISPlus
Group NIS authentication:
Apache2::AuthzNIS
Apache::AuthzNIS
Note:
Apache allows further restriction by client IP network address or subnet.
Passwords can also be sent over an encrypted https connection by use of the Apache
directive
SSLRequireSSL
. See
Apache SSL/TLS encryption
[Potential Pitfall]:
This method of authentication will fail if using "adjunct password maps". This Perl
module requires the use of the library call
yp_match()
which must have access to the encrypted
passwords. If "adjunct password maps" are used, then this is not accessible to processes other than
root thus the web server daemon process
apache
will not be able to access the data required. Test
your system using the command
ypcat passwd | head
. If the second field is prefixed with "##", then
this perl module will not work. If the second field is an encrypted password, then this perl module
can work.
CGI to allow users to modify their NIS Passwords:
Linux Tutorial - Apache Web Login Authentication:
http://www.yolinux.com/TUTORIALS/LinuxTutorialApacheAddingLog...
9 z 12
2014-01-22 11:16
For those users who get a shell of
/sbin/nologin
, the "cgipaf" web interface is ideal for user
management of NIS passwords. Cgipaf uses PHP, cgi (written in C) and your system PAM
authentication (or
/etc/passwd, /etc/shadow
files). Cgipaf also can manage mail accounts using
procmail.
Download from
http://www.wagemakers.be/english/programs/cgipaf
Installation/configuration:
tar xf cgipaf-1.3.1.tar.gz
cd cgipaf-1.3.1/
./configure --bindir=/var/www/cgi-bin --datadir=/srv/cgipaf --sysconfigdir=/etc
/cgipaf --prefix=/opt
Note: nothing ends up in
/opt
make
make install
cd /srv/cgipaf
ln -s cgipasswd.php index.php
File:
/etc/httpd/conf.d/cgipaf.conf
(Red Hat style systems)
Alias /NIS/ "/srv/cgipaf/"
<Directory "/srv/cgipaf">
SSLRequireSSL
Options Indexes FollowSymLinks
AllowOverride None
Order allow, deny
Allow from all
</Directory>
Note the Apache 2 directive "
SSLRequireSSL
" will only allow https encrypted access. This is
important when managing passwords over the web.
The PHP pages reside in
/srv/cgipaf/
. The compiled C cgi will reside in
/var/www/cgi-bin
. The
configuration file will be
/etc/cgipaf/cgipaf.conf
.
See the web page at
http://localhost/NIS/
Using a MySQL database for Apache Authentication:
Two Apache modules are available for database authentication:
MySQL: mod_auth_mysql (This tutorial)
Red Hat RPM package:
mod_auth_mysql
SuSE RPM package:
apache2-mod_auth_mysql
DBM database file: mod_auth_dbm
(Fast even for 1000's of users.)
Apache Configuration:
Red Hat:
/etc/httpd/conf/httpd.conf
or
/etc/httpd/conf.d/application.conf
SuSE:
/etc/apache2/httpd.conf
or
/etc/apache2/conf.d/application.conf
..
...
<Directory /home/domain/public_html/membersonly>
AuthType Basic
AuthName "Add your login message here."
AuthMySQLHost localhost
AuthMySQLUser db_user
AuthMySQLPassword db_password
AuthMySQLDB database_name_used_for_authentication
AuthMysqlUserTable http_auth
AuthMySQLPwEncryption none
AuthMySQLEnable on
require valid-user
</Directory>
...
..
Examples:
require valid-user
: Allow all users if authentication (password) is correct.
require user greg phil bob
: Allow only greg phil bob to login.
require group accounting
: Allow only users in group "accounting" to authenticate.
Directives:
Directive
Description
AuthMySQLEnable On
If 'Off', MySQL authentication will pass on the
authentication job to the other authentication modules i.e
password files.
AuthMySQLHost host_name
Name of MySQL Database hosr. i.e. 'localhost'
AuthMySQLPort
TCP_Port_number
Port number of MySQL Database. Default: 3306
Linux Tutorial - Apache Web Login Authentication:
http://www.yolinux.com/TUTORIALS/LinuxTutorialApacheAddingLog...
10 z 12
2014-01-22 11:16

AuthMySQLDB database_name
Name of MySQL Database.
AuthMySQLUser user_id
MySQL Database login id.
AuthMySQLPassword
user_password
MySQL Database login password. Plain text.
AuthMySQLUserTable
user_table_name
Name of MySQL Databse table in the database which holds
the user name and passwords.
AuthMySQLGroupTable
group_table_name
Databse table holding group info.
AuthMySQLNameField
user_field_name
If not using default field name 'user_name', then specify.
Not case sensitive id CHAR or VARCHAR.
AuthMySQLPasswordField
password_field_name
If not using default field name 'user_passwd', then specify.
Passwords are case sensitive.
AuthMySQLGroupField
group_field_name
If not using default field name 'groups', then specify.
AuthMySQLNoPasswd Off
Off: Passwords can be null ('').
On: password must be specified.
AuthMySQLPwEncryption none
Options: none, crypt, scrambled (MySQL password
encryption), md5, aes, sha. If you are going to use
plain-text passwords for mysql authentication, you must
include this directive with the argument "none".
AuthMySQLSaltField salt_string
mysql_column_name
Salt field to be used for crypt and aes.
AuthMySQLAuthoritative on
Authenticate using other authentication modules after the
user is successfully authenticated by the MySQL auth
module. Default on: request is not passed on.
AuthMySQLKeepAlive Off
Off: Close the MySQL link after each authentication
request.
MySQL Admin:
mysqladmin -h localhost -u root -ppassword create http_auth
mysql -h localhost -u root -ppassword
mysql> use http_auth
mysql> create table mysql_auth ( user_name char(30) NOT NULL,user_passwd char(60)
NOT NULL,user_group char(25),primary key (user_name) );
mysql> insert into mysql_auth values('Fred','supersecret','worker');
Links:
Home page for mod_auth_mysql
Home page for mod_auth_dbm [
Apache 1.3
] - [
Apache 2.0
]
YoLinux MySQL tutorial
Login URL Tricks:
Here is a trick to incorporate a login and password into a URL. Typicall one would attempt to enter
the password protected area of the web site and the user would be confronted with a login dialog
box into which one would enter the user id and password. Another option is to enter a URL with the
login and password embedded.
http://login-id:password@UrlOfDomain.com/protectedPath/WebPage.html
Links:
Apache:
Users authentication with .dbmpasswd password file
Apache::AuthenSmb
,
Apache2::AuthenSmb
- Microsoft Active Directory authentication
Apache::AuthenMSAD
,
Apache2::AuthenMSAD
- Samba NT PDC authentication
Apache::AuthenNTLM
,
Apache2::AuthenNTLM
- Microsoft NTLM LAN protocol suported by
MS/Internet Explorer. Login/password credentials passed on the web server by IE browser.
Other forms of web authentication:
Facebook Platform authentication
- Using OAuth protocol, the Facebook API allows developers
to use Javascript, PHP, Python, etc.
IETF OAuth 2.0 Protocol draft
OpenID
- decentralized URL based auth
Authentication Server Providers:
Yahoo OpenID
Google OpenID
OpenID for Google Apps API
Launchpad
Verisign OpenID
- two factor auth
API:
mod_auth_openid
- Apache 2
OpenId4Java
List of OpenID Libraries
- developer interfaces
SAML: Security Assertion Markup Language
- XML based authentication
Authentication Server Providers:
Google SAML
Linux Tutorial - Apache Web Login Authentication:
http://www.yolinux.com/TUTORIALS/LinuxTutorialApacheAddingLog...
11 z 12
2014-01-22 11:16
Books:
"Apache Server Bible 2"
by Mohammed J. Kabir
ISBN # 0764548212, Hungry Minds
This book is very complete covering all aspects in detail. It
is not your basic reprint of the apache.org documents like
so many others.
"LDAP System Administration",
Gerald Carter
ISBN 1565924916, O'Reilly & Associates
This book covers the use of OpenLDAP and the integration
of services.
"Managing NFS and NIS",
by Hal Stern, Mike Eisler, Ricardo Labiaga
ISBN 1565925106, O'Reilly & Associates
YoLinux.com Home Page
YoLinux Tutorial Index
|
Terms
Privacy Policy
|
Advertise with us
|
Feedback Form
|
Unauthorized copying or redistribution
prohibited.
StumbleUpon
4
6
Copyright © 2000 - 2012 by Greg Ippolito
Linux Tutorial - Apache Web Login Authentication:
http://www.yolinux.com/TUTORIALS/LinuxTutorialApacheAddingLog...
12 z 12
2014-01-22 11:16
Wyszukiwarka
Podobne podstrony:
linux web solution php mysq apache HREZG5TBQHGLJQKXDM6YUEGP
Konfiguracja serwera Apache, SSL w systemie GNU Linux
Creating a dd dcfldd Image Using Automated Image & Restore (AIR) HowtoForge Linux Howtos and Tutor
java ApacheAnt tutorial
02 Linux Konfiguracja serwera WWW APACHE
Konfiguracja serwera Apache, SSL w systemie GNU Linux
Installing LAMP On Ubuntu For Newbies, HowtoForge Linux Howtos and Tutorials
Linux Apache MySQL i PHP Zaawansowane programowanie lapzap
Linux Apache MySQL i PHP Zaawansowane programowanie
Hardening Linux Web Servers (Free Software Magazine)(1)
Linux Apache MySQL i PHP Zaawansowane programowanie lapzap
Linux, Apache, MySQL i PHP Zaawansowane programowanie
Linux exploit writing tutorial part 1 Stack overflow
ebook Jason Gerner, Morgan L Owens, Elizabeth Naramore, Matt Warden Linux, Apache, MySQL i PHP Zaaw
Linux Apache MySQL i PHP Zaawansowane programowanie 2
więcej podobnych podstron