
Internet Products 9-15
Cisco PIX Firewall
9
Cisco PIX Firewall
Product Overview
Cisco’s PIX Firewall series delivers high security and fast performance to corporate networks. The firewalls allow you to
thoroughly conceal your internal network from the outside world—providing full firewall security protection. Unlike typical
CPU-intensive proxy servers that perform extensive processing on each data packet, the Cisco PIX Firewalls use a
non-UNIX, secure, real-time, embedded system. This setup allows the Cisco PIX Firewall series to deliver the outstanding
performance of more than 16,000 simultaneous connections, dramatically greater than any UNIX-based firewall.
For simplified management, the Cisco PIX Firewall series includes the Firewall Manager, a Java-based graphical user
interface (GUI) configuration tool that lets you click on a PIX Firewall icon to retrieve, edit, and centrally manage security
policies. With management reports, network managers can perform statistical analysis on unauthorized users, amounts of
traffic, and event logging for potential cost accounting. Network managers can also use Universal Resource Locator (URL)
accounting to monitor which Web sites their users visit most. And by setting thresholds, the Cisco PIX Firewall series can
automatically provide real-time alerts of any attempted firewall breaches through e-mail or page notification. The Cisco PIX
Firewall series can also block out unwanted Java applets.
The Cisco PIX Firewall series provides the following benefits:
•
Less complex and more robust than packet-filtering
•
No downtime required for installation
•
No day-to-day management required
•
No upgrading of hosts or routers
•
Full outbound Internet access from unregistered internal hosts
•
Does not require additional registered IP addresses for network expansion
•
Allows use of Address Allocation for Private Internets (RFC 1918) or registered IP addresses
•
No user impact—nondisruptive to existing LANs
•
Interoperable with Cisco IOS-based routers
The heart of the high performance of the Cisco PIX Firewall series is a protection scheme based on the adaptive security
algorithm (ASA), which effectively protects access to an internal host network. The stateful, connection-oriented ASA
approach to security builds session flows based on source and destination addresses, TCP sequence numbers (which are
randomized), port numbers, and additional TCP flags. This information is stored in a table, and all inbound and outbound
packets are compared against entries in the table. Access is permitted through the Cisco PIX Firewall series only if an
appropriate connection exists to validate passage. This provides internal users and authorized external users transparent
access to an organization, while protecting the internal network from unauthorized access.
Cisco’s PIX Firewall series gains further dramatic performance advantage through a new feature called cut-though proxy.
Whereas UNIX-based proxy servers are an ideal platform and can provide user authentication and maintain “state”
(information about a packet’s origin and destination) to offer good security, their performance suffers because they process
all packets at the application layer (Layer 7) of the OSI model, which is highly CPU-intensive.
The cut-through proxy feature of the Cisco PIX Firewall, on the other hand, challenges a user initially at the application layer,
like a proxy server. But once the user is authenticated against an industry-standard database based on Terminal Access
Controller Access Control System (TACACS)+ or Remote Authentication Dial-In User Service (RADIUS), and access
policy is checked, the Cisco PIX Firewall series shifts the session flow, and all traffic thereafter flows directly and quickly
between the two parties, while maintaining session state without compromising any security over traditional proxy-based
firewalls. This cut-through capability allows the Cisco PIX Firewall series to perform dramatically faster than proxy servers.
Cut-through proxy also saves installation and maintenance costs by leveraging an already-existing authorization database
(based on TACACS+ or RADIUS) used for the dial-in communications server. Cisco Systems offers such an enterprise
management authorization database/server called CiscoSecure Access Control Server. For more information on CiscoSecure
Access Control Server, see the “CiscoSecure Access Control Server v2.1 for UNIX” section in the “CiscoSecure Access
Control Server Software” chapter, earlier in this catalog.
Cisco PIX Firewall
9-16 Cisco Reseller Product Catalog, March 1998
Beyond this high level of performance, the real-time embedded system also enhances the security of the Cisco PIX Firewall
series. Although UNIX-based proxy servers are an ideal open development platform with widely available source code, such
general-purpose operating systems provide less-than-optimum performance and security. The dedicated Cisco PIX Firewall
series is designed specifically for secure, high-performance protection.
For even higher reliability, the Cisco PIX Firewall series is available with a failover/hot standby upgrade option, which
eliminates a single point of failure. With two PIX Firewalls running in parallel, if one malfunctions, the second Cisco PIX
Firewall transparently maintains security operations.
The Cisco PIX Firewall series also provides a feature to expand and reconfigure IP networks without being concerned about
a shortage of IP addresses. Network address translation (NAT) makes it possible to use either existing IP addresses or the
addresses set aside in the Internet Assigned Numbers Authority’s (IANA’s) reserve pool (RFC 1918). The PIX Firewall series
can also selectively allow a mix of addresses to be translated or not translated, as needed.
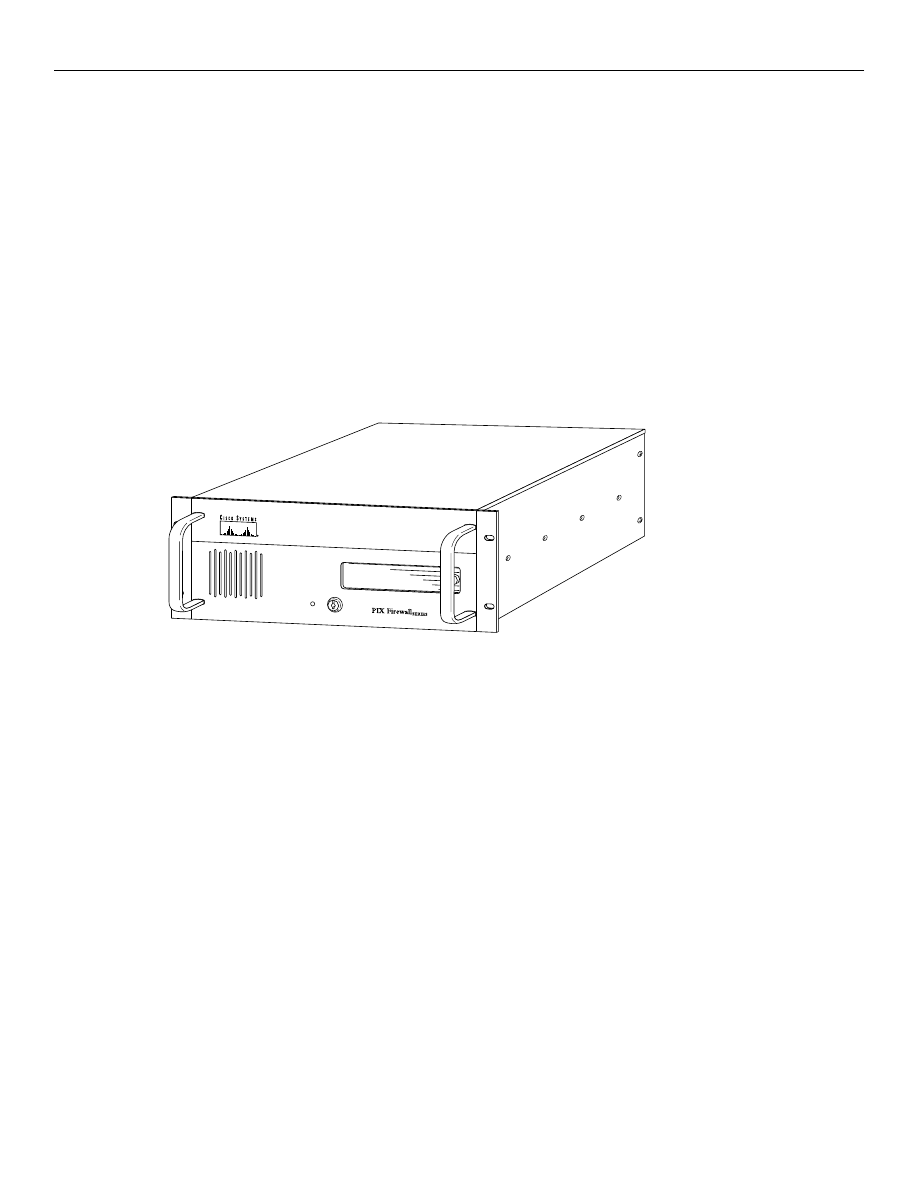
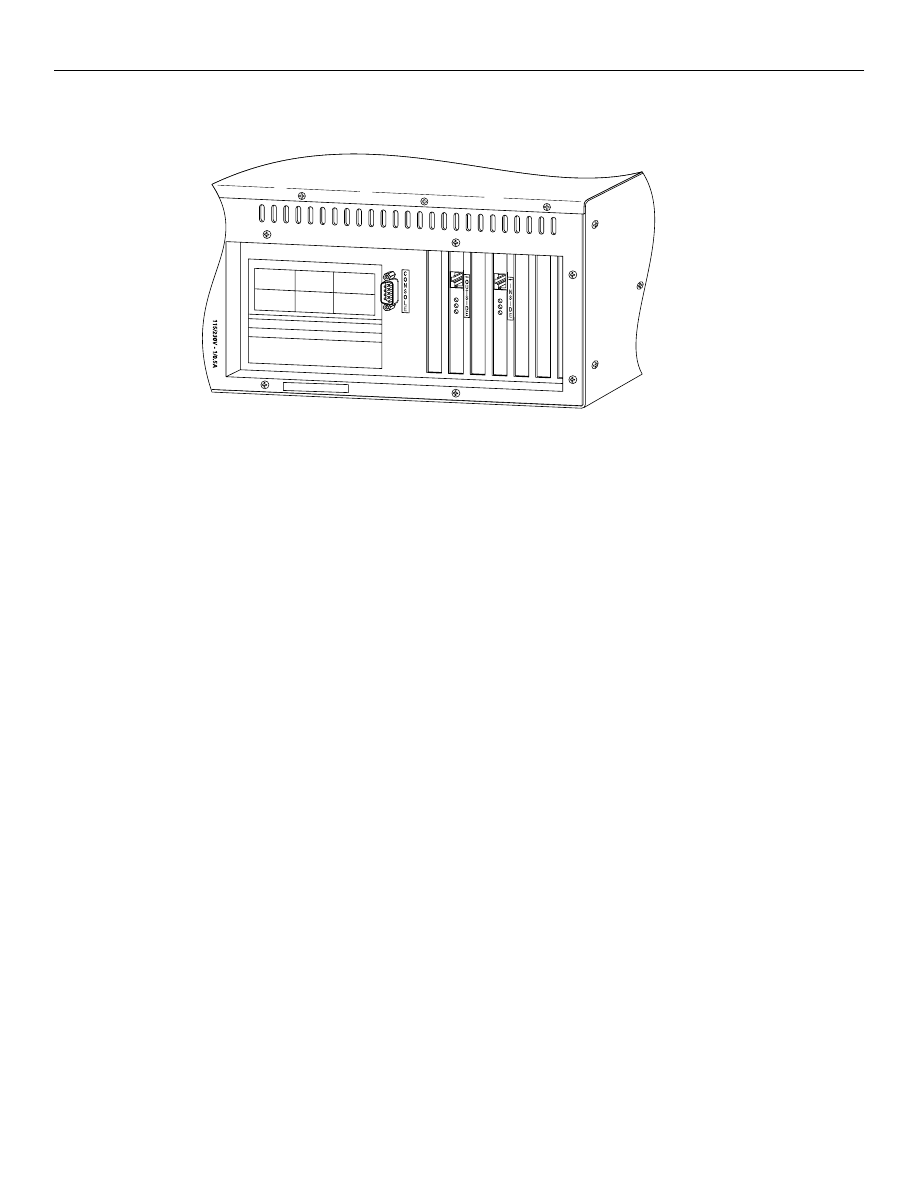
Figure 9-3 shows a front view of the PIX Firewall, and Figure 9-4 shows a rear view.
Figure 9-3
PIX Firewall Front View
H10924
Internet Products 9-17
Standard Features
Figure 9-4
PIX Firewall Rear View
Standard Features
The PIX Firewall series includes the following features:
•
Strong, stateful connection-oriented protection to restrict unauthorized users from accessing network resources
•
Cut-through proxy to allow both inbound and outbound Internet access based on industry-standard protocols such as
TACACS+ and RADIUS
•
Support for over 16,000 simultaneous connections
•
Enhanced, easy-to-use Firewall Manager for configuring multiple Cisco PIX Firewall series
•
Third network interface for platform extensibility and security policy enforcement on publicly accessible services
(WWW, mail, DNS, etc.)
•
Oracle SQL*Net access through the Cisco PIX Firewall series for secure client/server applications
•
Support of Cisco IOS-style command-line interface
•
Failover/hot standby for high reliability
•
True Network Address Translation (NAT) as specified in RFC 1631
•
Port Address Translation (PAT) to further expand a company’s address pool–one IP address supports more than 64,000
hosts, 16,384 simultaneously
•
Net Aliasing to transparently merge overlapping networks with the same IP address space
•
For networks with registered IP addresses, nontranslation allows use of existing registered IP numbers
•
Transparent support for all common TCP/IP Internet services, such as WWW, File Transfer Protocol (FTP), Telnet,
Archie, gopher, and rlogin
•
Support of multimedia data types, including Progressive Networks’ RealAudio, Xing Technologies’ Streamworks, White
Pines’ CuSeeMe, Vocal Tec’s Internet Phone, VDOnet’s VDOLive, Microsoft’s NetShow, VXtreme Web Theatre 2; and
Intel’s Internet Video Phone and Microsoft’s NetMeeting (based on H.323 standards)
•
Blocking of potentially dangerous Java applets
•
Secure, real-time system
•
Multiple login levels supported
•
Support of Simple Network Management Protocol (SNMP) traps
•
Management reports and URL accounting features
H7501
Cisco PIX Firewall
9-18 Cisco Reseller Product Catalog, March 1998
•
Auditing provided through syslog
•
Syslog Management Information Base (MIB) support
•
URL and FTP accounting to allow auditing of Web usage
•
Remote-procedure call (RPC) support
•
Mail Guard to remove need for external mail relay workstation in perimeter network
•
SYN Flood Defender-protects the host on the private network from denial of service attacks
•
NetBIOS translation-support for Microsoft Networking client and server communication through the Cisco PIX Firewall
series
•
Two hardware platforms (PIX and PIX 10000) to meet a range of performance and scalability needs, from 45 Mb/s to
greater than 90 Mb/s
Table 9-10
Cisco PIX Firewall Series Summary of Features
Characteristic
Description
Available software sessions:
64, 1024, 16,384
(based on simultaneous TCP/IP connections)
Network support
10/100BaseT Ethernet
4- to 16-Mbps Token Ring
Internet Protocol standards: IP, TCP, User Datagram Protocol
(UDP), Internet Control Message Protocol (ICMP)
RJ-45
Hardware
19-in. rack-mount enclosure
DB-9 EIA/TIA-232 console port
3.5-in. diskette drive
Lockable front panel
Dimensions (H x W x D)
7 x 19 x 18.5 in. (17.8 x 48.3 x 47 cm)
Weight
21 lb (9.5 kg)
Power requirements
115 VAC 10%, 47–63 Hz, 4.2A maximum
230 VAC 10%, 47–63 Hz, 2.0A maximum
Agency approvals
UL-1950 standard
CSA-EB-1402C standard
IEC-380/VDE-0806 standard
IEC-950/VDE-0805 EN-60-950 standard
Table 9-11
Cisco PIX Firewall Series Environmental Specifications
Description
Specification
Temperature
Operating: 32 to 113 F (0to 45 C)
Storage: 14 to 167 F (–10 to 75 C)
Humidity
Operating: 85%, maximum at 131 F (55 C)
Storage: 92%, maximum at 131 F (55 C)
Altitude
Operating: 10,000 ft (3048 m)
Storage: 50,000 ft (15,240 m)
Internet Products 9-19
Hardware
Hardware
The Cisco PIX Firewall series includes two hardware platforms: the original PIX Firewall and the high-end model 10000
Cisco PIX Firewall for higher network performance demands. Both platforms include Cisco’s ASA software.
Also available is the Cisco PIX Private Link encryption card. With this card, companies can dramatically reduce
telecommunications costs by having options to dedicated leased lines and sending encrypted IP packets over any public
IP-based network, such as the Internet. With a Cisco PIX Private Link encryption card at each PIX Firewall site, companies
can be assured of secure communications through the Internet. The encryption card uses the Data Encryption Standard (DES)
algorithm and the Internet Engineering Task Force’s (IETF’s) Authentication Header/Encapsulating Security Payload
(AH/ESP) protocols (RFCs 1826 and 1827, respectively).
Other products included in the Cisco PIX Firewall series are a 10/100-Mbps Ethernet network interface card (NIC), and a
4/16-Mbps Token Ring NIC. An optional cable supports a failover/hot standby firewall to eliminate a single point of failure.
Product Numbers
Table 9-12
Cisco PIX Firewall Series Product Numbers
Description
Product Number
Base System
PIX Firewall, 133-MHz processor
PIX
PIX Firewall, 200-MHz processor
PIX10000
Software and Documentation
64 simultaneous sessions
SWPIX-64
1024 simultaneous sessions
SWPIX-1K
16,384 simultaneous sessions
SWPIX-UR
PIX Documentation Set
DOC-PIX=
Software Upgrades and Updates
PIX software version update
SWPIX-VER=
PIX software upgrade 1Kto 16K sessions
SWPIX-1K-UR-C=
PIX software upgrade 64 sessions to 1K sessions
SWPIX-64-1K-C=
PIX software upgrade 64 sessions to 16K sessions
SWPIX-64-UR-C=
Software to update inventory, sold stand-alone (spare)
SWPIX-SC=
PIX Firewall Network Interfaces
10/100-Mbps Ethernet interface, RJ-45
PIX-1FE
4- or 16-Mbps Token Ring interface
PIX-1TR
Bundles
Bundle of 133 MHz PIX, 1024 session s/w, 2 Ethernet
NICs
PIX1K-A-CH
Bundle of 200MHz PIX, 1K session s/w, 2 Ethernet NICs
PIX1K-B-CH
Bundle of 133 MHz PIX, 64 session s/w, 2 Ethernet NICs
PIX64-A-CH
Bundle of 200 MHz PIX, 64session s/w, 2 Ethernet NICs
PIX64-B-CH
Bundle of 133 MHz PIX, 16K session s/w, 2 Ethernet
NICs
PIXUR-A-CH
Bundle of 200 MHz PIX, 16K session s/w, 2 Ethernet
NICs
PIX64-B-CH

Cisco PIX Firewall
9-20 Cisco Reseller Product Catalog, March 1998
Accessories
Private Link encryption
PIX-PL
Service and Support
PIX SMARTnet maintenance
PIX On-Site maintenance
Table 9-12
Cisco PIX Firewall Series Product Numbers
Description
Product Number
Wyszukiwarka
Podobne podstrony:
O'Reilly How To Build A FreeBSD STABLE Firewall With IPFILTER From The O'Reilly Anthology
Przenikanie firewalli w tunelach kryptograficznych
2009 01 Firewall w Linuksie [Poczatkujacy]
Firewalle i bezpieczenstwo w sieci Vademecum profesjonalisty firevp
Definiowanie reguł postępowania dla serwera FireWall określających sposób dostępu do wybranych serwe
Firewalle i bezpieczeństwo w sieci Vademecum profesjonalisty
firewall manual
Linux 2 4 Firewall designl fw a4
Cisco IOS Firewall Intrusion Detection System(1)
Firewalls r472
Firewalls, Firewall
PSI firewall
Firewalle i bezpieczenstwo w sieci Vademecum profesjonalisty firevp
firewall
Firewall i kryptografia
FirewallIOS
Cisco PIX Firewalle cispix
firewalle i bezpieczeństwo w sieci (helion, stresczenie) GXQCAUNAIKIGTTUEZOAK6IMEJFBA6ZPGGJGDAZY
firewall
więcej podobnych podstron