
Anjana Suparna Sriram Divya Muntimadugu
Red Hat Storage 2.0
Installation Guide
Installing Red Hat Storage 2.0
Edition 1

Red Hat Storage 2.0 Installation Guide
Installing Red Hat Storage 2.0
Edition 1
Anjana Suparna Sriram
Red Hat Engineering Co ntent Services
asriram@redhat.co m
Divya Muntimadugu
Red Hat Engineering Co ntent Services
divya@redhat.co m

Legal Notice
Copyright © 2012 Red Hat Inc.
This document is licensed by Red Hat under the
Creative Commons Attribution-ShareAlike 3.0 Unported
. If you distribute this document, or a modified version of it, you must provide attribution to Red
Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be
removed.
Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section
4d of CC-BY-SA to the fullest extent permitted by applicable law.
Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo,
and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries.
Linux ® is the registered trademark of Linus Torvalds in the United States and other countries.
Java ® is a registered trademark of Oracle and/or its affiliates.
XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States
and/or other countries.
MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other
countries.
Node.js ® is an official trademark of Joyent. Red Hat Software Collections is not formally related to or
endorsed by the official Joyent Node.js open source or commercial project.
The OpenStack ® Word Mark and OpenStack Logo are either registered trademarks/service marks or
trademarks/service marks of the OpenStack Foundation, in the United States and other countries and
are used with the OpenStack Foundation's permission. We are not affiliated with, endorsed or
sponsored by the OpenStack Foundation, or the OpenStack community.
All other trademarks are the property of their respective owners.
Abstract
This guide describes the prerequisites and provides step-by-instructions to install Red Hat Storage
using different methods.

. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Table of Contents
1. Audience
2. License
3. Document Conventions
3.1. Typographic Conventions
3.2. Pull-quote Conventions
3.3. Notes and Warnings
4. Getting Help and Giving Feedback
4.1. Do You Need Help?
4.2. We Need Feedback!
Chapter 2. Obtaining Red Hat Storage
Chapter 3. Planning Red Hat Storage Installation
3.1.1. Network Time Protocol Setup
3.2. Is Your Hardware Compatible?
Chapter 4 . Installing Red Hat Storage
4.1. Installing from an .ISO Image
4.2. Booting from a PXE Server
Chapter 5. Registering to Red Hat Network (RHN)
Chapter 6. Setting up Software Updates
Chapter 7. Managing glusterd Service
7.1. Starting and Stopping glusterd Manually
Chapter 8. Using the Gluster Command Line Interface
3
3
3
3
3
4
5
6
6
6
7
8
8
8
9
9
9
10
11
11
16
17
19
19
20
20
21
22
Table of Contents
1

Red Hat Storage 2.0 Installation Guide
2

Preface
Red Hat Storage is scale-out network attached storage (NAS) for private cloud or datacenter, public
cloud, and hybrid cloud environments. It is software-only, open source, and designed to meet
unstructured data storage requirements.
This installation guide describes the Red Hat Storage installation process, describes the minimum
requirements, and provides step-by-step instructions to install the software and manage your storage
environment.
1. Audience
This guide is intended for anyone responsible for installing Red Hat Storage. This guide assumes that
you are familiar with the Linux operating system, concepts of file system, and GlusterFS concepts.
2. License
The Red Hat Storage End User License Agreement (EULA) is available at
http://www.redhat.com/licenses/rhel_rha_eula.html
.
3. Document Conventions
This manual uses several conventions to highlight certain words and phrases and draw attention to
specific pieces of information.
In PDF and paper editions, this manual uses typefaces drawn from the
set. The
Liberation Fonts set is also used in HTML editions if the set is installed on your system. If not, alternative
but equivalent typefaces are displayed. Note: Red Hat Enterprise Linux 5 and later include the Liberation
Fonts set by default.
3.1. Typographic Conventions
Four typographic conventions are used to call attention to specific words and phrases. These
conventions, and the circumstances they apply to, are as follows.
Mono-spaced Bold
Used to highlight system input, including shell commands, file names and paths. Also used to highlight
keys and key combinations. For example:
To see the contents of the file my_next_bestselling_novel in your current working
directory, enter the cat my_next_bestselling_novel command at the shell prompt
and press Enter to execute the command.
The above includes a file name, a shell command and a key, all presented in mono-spaced bold and all
distinguishable thanks to context.
Key combinations can be distinguished from an individual key by the plus sign that connects each part of
a key combination. For example:
Press Enter to execute the command.
Press Ctrl+Alt+F2 to switch to a virtual terminal.
The first example highlights a particular key to press. The second example highlights a key combination:
Preface
3

a set of three keys pressed simultaneously.
If source code is discussed, class names, methods, functions, variable names and returned values
mentioned within a paragraph will be presented as above, in mono-spaced bold. For example:
File-related classes include filesystem for file systems, file for files, and dir for
directories. Each class has its own associated set of permissions.
Proportional Bold
This denotes words or phrases encountered on a system, including application names; dialog box text;
labeled buttons; check-box and radio button labels; menu titles and sub-menu titles. For example:
Choose System → Preferences → Mouse from the main menu bar to launch Mouse
Preferences. In the Buttons tab, select the Left-handed mouse check box and click
Close to switch the primary mouse button from the left to the right (making the mouse
suitable for use in the left hand).
To insert a special character into a gedit file, choose Applications → Accessories →
Character Map from the main menu bar. Next, choose Search → Find… from the
Character Map menu bar, type the name of the character in the Search field and click
Next. The character you sought will be highlighted in the Character T able. Double-click
this highlighted character to place it in the Text to copy field and then click the Copy
button. Now switch back to your document and choose Edit → Paste from the gedit menu
bar.
The above text includes application names; system-wide menu names and items; application-specific
menu names; and buttons and text found within a GUI interface, all presented in proportional bold and all
distinguishable by context.
Mono-spaced Bold Italic or Proportional Bold Italic
Whether mono-spaced bold or proportional bold, the addition of italics indicates replaceable or variable
text. Italics denotes text you do not input literally or displayed text that changes depending on
circumstance. For example:
To connect to a remote machine using ssh, type ssh username@domain.name at a shell
prompt. If the remote machine is example.com and your username on that machine is
john, type ssh john@example.com.
The mount -o remount file-system command remounts the named file system. For
example, to remount the /home file system, the command is mount -o remount /home.
To see the version of a currently installed package, use the rpm -q package command. It
will return a result as follows: package-version-release.
Note the words in bold italics above — username, domain.name, file-system, package, version and
release. Each word is a placeholder, either for text you enter when issuing a command or for text
displayed by the system.
Aside from standard usage for presenting the title of a work, italics denotes the first use of a new and
important term. For example:
Publican is a DocBook publishing system.
3.2. Pull-quote Conventions
Red Hat Storage 2.0 Installation Guide
4
Terminal output and source code listings are set off visually from the surrounding text.
Output sent to a terminal is set in mono-spaced roman and presented thus:
books Desktop documentation drafts mss photos stuff svn
books_tests Desktop1 downloads images notes scripts svgs
Source-code listings are also set in mono-spaced roman but add syntax highlighting as follows:
static
int
kvm_vm_ioctl_deassign_device(
struct
kvm *kvm,
struct
kvm_assigned_pci_dev *assigned_dev)
{
int
r = 0;
struct
kvm_assigned_dev_kernel *match;
mutex_lock(&kvm->lock);
match = kvm_find_assigned_dev(&kvm->arch.assigned_dev_head,
assigned_dev->assigned_dev_id);
if
(!match) {
printk(KERN_INFO
"%s: device hasn't been assigned before, "
"so cannot be deassigned
\n
"
, __func__);
r = -EINVAL;
goto
out;
}
kvm_deassign_device(kvm, match);
kvm_free_assigned_device(kvm, match);
out:
mutex_unlock(&kvm->lock);
return
r;
}
3.3. Notes and Warnings
Finally, we use three visual styles to draw attention to information that might otherwise be overlooked.
Note
Notes are tips, shortcuts or alternative approaches to the task at hand. Ignoring a note should
have no negative consequences, but you might miss out on a trick that makes your life easier.
Important
Important boxes detail things that are easily missed: configuration changes that only apply to the
current session, or services that need restarting before an update will apply. Ignoring a box
labeled 'Important' will not cause data loss but may cause irritation and frustration.
Preface
5

Warning
Warnings should not be ignored. Ignoring warnings will most likely cause data loss.
4. Getting Help and Giving Feedback
4.1. Do You Need Help?
If you experience difficulty with a procedure described in this documentation, visit the Red Hat Customer
Portal at
. Through the customer portal, you can:
search or browse through a knowledgebase of technical support articles about Red Hat products.
submit a support case to Red Hat Global Support Services (GSS).
access other product documentation.
Red Hat also hosts a large number of electronic mailing lists for discussion of Red Hat software and
technology. You can find a list of publicly available mailing lists at
https://www.redhat.com/mailman/listinfo
.
Click on the name of any mailing list to subscribe to that list or to access the list archives.
4.2. We Need Feedback!
If you find a typographical error in this manual, or if you have thought of a way to make this manual
better, we would love to hear from you! Please submit a report in Bugzilla:
against the product Red Hat Storage.
When submitting a bug report, be sure to mention the manual's identifier: doc-Installation_Guide
If you have a suggestion for improving the documentation, try to be as specific as possible when
describing it. If you have found an error, please include the section number and some of the surrounding
text so we can find it easily.
Red Hat Storage 2.0 Installation Guide
6

Chapter 1. Introduction
Red Hat Storage is software only, scale-out storage that provides flexible and affordable unstructured
data storage for the enterprise. Red Hat Storage 2.0 provides new opportunities to unify data storage
and infrastructure, increase performance, and improve availability and manageability in order to meet a
broader set of an organization’s storage challenges and needs.
GlusterFS, a key building block of Red Hat Storage, is based on a stackable user space design and can
deliver exceptional performance for diverse workloads. GlusterFS aggregates various storage servers
over network interconnects into one large parallel network file system. The POSIX compatible GlusterFS
servers, which use XFS file system format to store data on disks, can be accessed using industry
standard access protocols including NFS and CIFS.
Red Hat Storage can be deployed in the private cloud or datacenter using Red Hat Storage Server for
On-premise. Red Hat Storage can be installed on commodity servers and storage hardware resulting in
a powerful, massively scalable, and highly available NAS environment. Additionally, Red Hat Storage can
be deployed in the public cloud using Red Hat Storage Server for Public Cloud, for example, within the
Amazon Web Services (AWS) cloud. It delivers all the features and functionality possible in a private
cloud or datacenter to the public cloud by providing massively scalable and high available NAS in the
cloud.
Red Hat Storage Server for On-Premise
Red Hat Storage Server for On-Premise enables enterprises to treat physical storage as a virtualized,
scalable, and centrally managed pool of storage by using commodity server and storage hardware.
Red Hat Storage Server for Public Cloud
Red Hat Storage Server for Public Cloud packages GlusterFS as an Amazon Machine Image (AMI) for
deploying scalable NAS in the AWS public cloud. This powerful storage server provides a highly
available, scalable, virtualized, and centrally managed pool of storage for Amazon users.
Chapter 1. Introduction
7
Chapter 2. Obtaining Red Hat Storage
This chapter provides information on how you can obtain Red Hat Storage software.
2.1. Obtaining Red Hat Storage Server for On-Premise
If you have a Red Hat subscription, you can download ISO image files of the Red Hat Storage Server for
On-Premise installation DVD from the Software & Download Center that is part of the Red Hat customer
portal. If you do not already have a subscription, either purchase one or obtain a free evaluation
subscription from the Software & Download Center at
https://access.redhat.com/downloads
.
If you have a subscription or evaluation subscription, follow these steps to obtain the Red Hat Storage
.ISO image files:
1. Visit the customer portal at
https://access.redhat.com/login
and enter your Login and Password.
2. Click Downloads to visit the Software & Download Center.
3. In the Red Hat Storage Server area, click the Download your software link to obtain the latest
version of the software.
2.2. Obtaining Red Hat Storage Server for Public Cloud
Red Hat Storage Server for Public Cloud is a pre-integrated, pre-verified and ready to run Amazon
Machine Image (AMI) that provides a fully POSIX compatible highly available scale-out NAS and object
storage solution for the Amazon Web Services (AWS) public cloud infrastructure.
For more information on obtaining access to AMI, see
https://access.redhat.com/knowledge/articles/145693
.
Red Hat Storage 2.0 Installation Guide
8
Chapter 3. Planning Red Hat Storage Installation
This chapter outlines the hardware and software requirements for installing the Red Hat Storage. The
requirements outlined herein are based on the minimum requirements for successful installation,
configuration, and operation of a Red Hat Storage Server environment.
3.1. Prerequisites
Ensure that your environment meets the following requirements.
File System Requirements
XFS - It is mandatory that the back-end file system be formatted using XFS for GlusterFS bricks. It
supports metadata journaling, which facilitates quicker crash recovery. The XFS file system can also be
defragmented and expanded while mounted and active.
Note
If you are an existing Gluster Storage Software Appliance customer and use ext3 or ext4 as your
back-end file systems, Red Hat will assist you to upgrade to a supported Red Hat Storage with
XFS back-end file system.
Logical Volume Manager
You must format GlusterFS bricks using XFS on Logical Volume Manager.
Network Time Configuration
Ensure to synchronize time on all Red Hat Storage servers. You are recommended to set up NTP
(Network Time Protocol) daemon to sync time.
3.1.1. Network Time Protocol Setup
You can also synchronize the system clock with a remote server over the Network Time Protocol (NTP).
To synchronize the time at boot time automatically, set the ntpd daemon to synchronize the time.
1. Open the NTP configuration file /etc/ntp.conf in a text editor such as vi or nano.
# nano /etc/ntp.conf
2. Now add or edit the list of public NTP servers. If you are using Red Hat Enterprise Linux 6, the file
should already contain the following lines, but feel free to change or expand these according to
your needs:
server 0.rhel.pool.ntp.org
server 1.rhel.pool.ntp.org
server 2.rhel.pool.ntp.org
Chapter 3. Planning Red Hat Storage Installation
9
Speed up initial synchronization
To speed the initial synchronization up, add the iburst directive at the end of each server
line:
server 0.rhel.pool.ntp.org iburst
server 1.rhel.pool.ntp.org iburst
server 2.rhel.pool.ntp.org iburst
3. Once you have the list of servers complete, in the same file, set the proper permissions, giving the
unrestricted access to localhost only:
restrict default kod nomodify notrap nopeer noquery
restrict -6 default kod nomodify notrap nopeer noquery
restrict 127.0.0.1
restrict -6 ::1
4. Save all changes, exit the editor, and restart the NTP daemon:
# service ntpd restart
5. Make sure that ntpd daemon is started at boot time:
# chkconfig ntpd on
You can use the ntpdate command for the one-time synchronization of NTP. For more information
about this feature, refer to the Red Hat Enterprise Linux Deployment Guide.
3.2. Is Your Hardware Compatible?
Hardware compatibility is particularly important if you have an older system or a system that you built
yourself. However, hardware specifications change almost daily, so it is hard to guarantee that your
hardware will be 100% compatible.
The most recent list of supported hardware can be found at:
https://access.redhat.com/knowledge/articles/66206
Red Hat Storage 2.0 Installation Guide
10

Chapter 4. Installing Red Hat Storage
Red Hat Storage can be installed in a data center using Red Hat Storage Server On-Premise.
This chapter describes the two different methods for installing Red Hat Storage Server. You can install
Red Hat Storage Server using an .iso image or boot using a PXE server. In addition, you can define
how you wish to partition the storage.
For information on launching Red Hat Storage Server for Public Cloud, see Red Hat Storage
Administration Guide.
4.1. Installing from an .ISO Image
To install Red Hat Storage Server from the .iso image:
1. Download an .iso image file of the Red Hat Storage Server as described in
The installation process launches automatically when you boot the system.
Press Enter to begin the installation process.
2. Configure TCP/IP screen displays.
To configure your computer for TCP/IP support, accept the default values of Internet Protocol
Version 4 (TCP/IPv4) and Internet Protocol Version 6 (TCP/IPv6) and click OK. Alternatively, you
can manually configure the network setting for both Internet Protocol Version 4 (TCP/IPv4) and
Internet Protocol Version 6 (TCP/IPv6)
Chapter 4. Installing Red Hat Storage
11
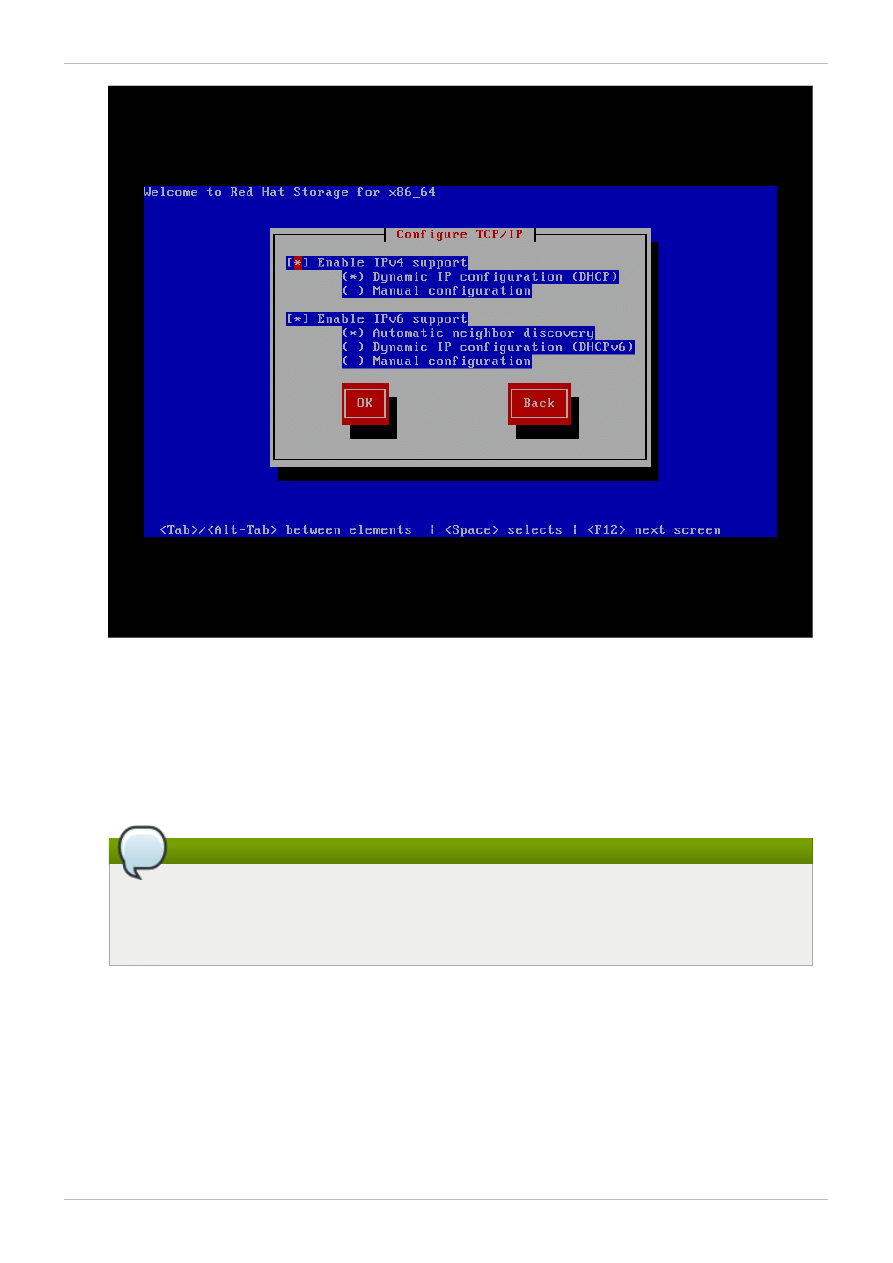
Figure 4 .1. Configure TCP/IP
3. Set the Root Password screen displays.
Setting up a root account and password is one of the most important steps during your installation
as you will use this account's credentials to install packages, upgrade RPMs, and perform most
system maintenance.
You cannot proceed to the next stage of the installation process without entering a root password.
Note
The root user (also known as the superuser) has complete access to the entire system;
for this reason, logging in as the root user is best done only to perform system
maintenance or administration.
Red Hat Storage 2.0 Installation Guide
12

Set Root Password screen prompts you to set a root password for your system. You must set
the root password in order to proceed.
Enter the root password into the Root Password field. Red Hat Storage Software Appliance
displays the characters as asterisks for security. Type the same password into the Confirm field
to ensure it is set correctly. After you set the root password, select Next to proceed.
4. The Partitioning Type screen displays.
Partitioning allows you to divide your hard drive into isolated sections, where each section
behaves as its own hard drive. Partitioning is particularly useful if you run multiple operating
systems. If you are not sure how you want your system to be partitioned, read Appendix A, An
Introduction to Disk Partitions of Red Hat Enterprise Linux 6 Installation Guide for more information.
On this screen you can choose to create the default partition layout in one of four different ways,
or choose to partition storage devices manually to create a custom layout.
If you do not feel comfortable with partitioning your system, choose one of the first four options
that allow you to perform an automated installation without having to partition your storage devices
yourself. Depending on the option that you choose, you can still control what data (if any) is
removed from the system. Your options are:
Use All Space
Replace Existing Linux System(s)
Shrink Current System
Use Free Space
Create Custom Layout
Choose your preferred partitioning method by clicking the radio button to the left of its description
in the dialog box.
Chapter 4. Installing Red Hat Storage
13
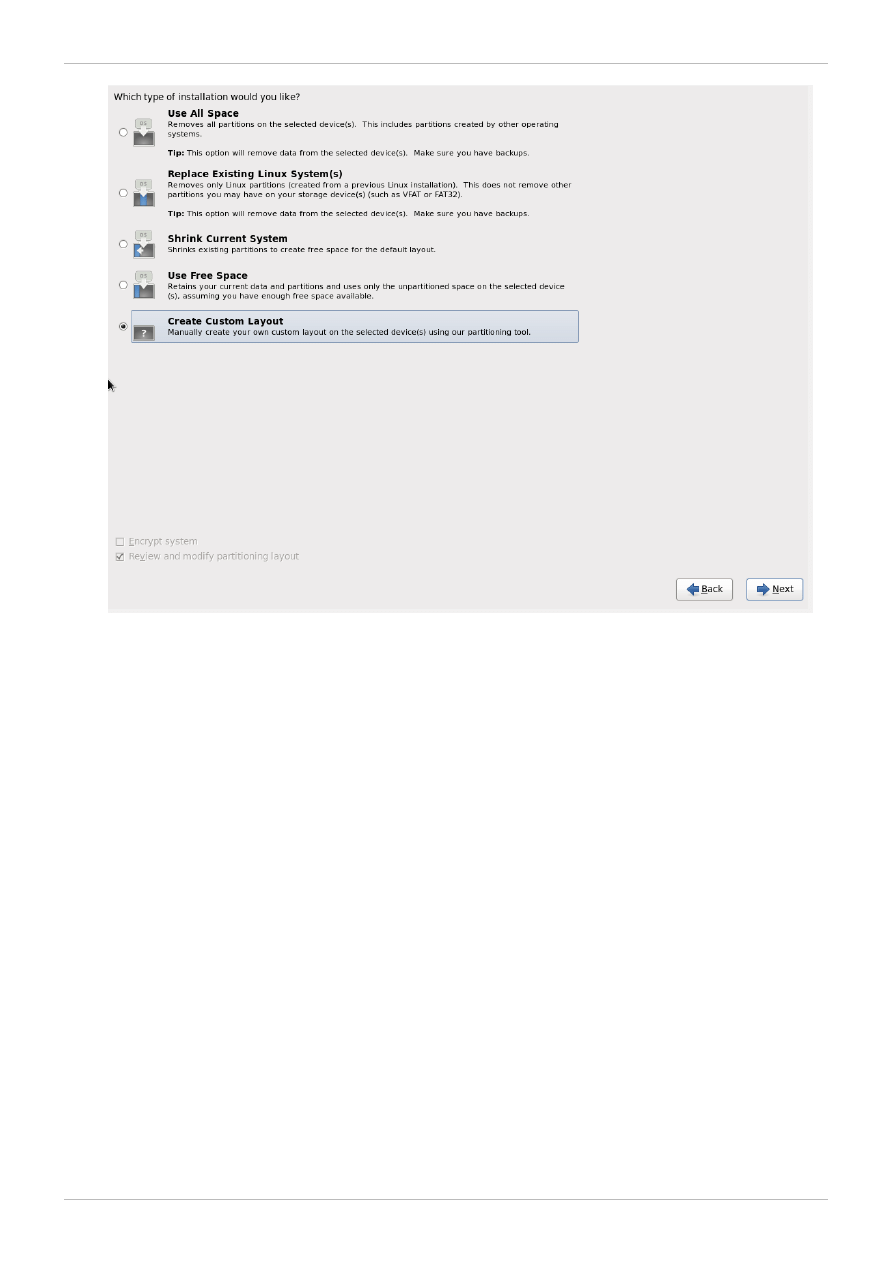
Click Next once you have made your selections to proceed. For more information on disk
partitioning, refer 9.13. Disk Partitioning Setup of Red Hat Enterprise 6 Installation Guide.
5. The Package Installation screen displays.
Red Hat Storage Server reports the installation progress on the screen as it writes the selected
packages to your system.
Red Hat Storage 2.0 Installation Guide
14
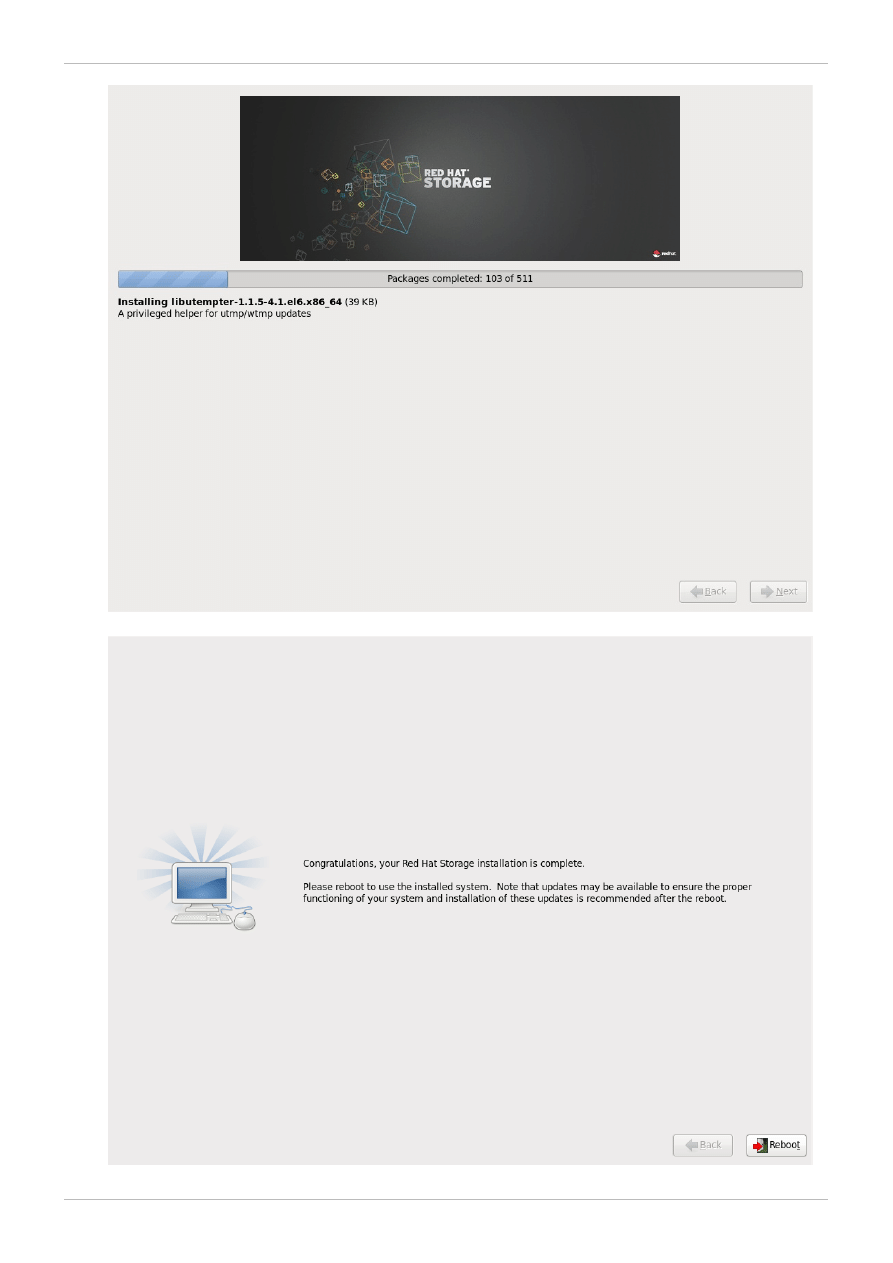
6. On successful completion the Complete Status screen displays.
Chapter 4. Installing Red Hat Storage
15

7. Click Reboot to reboot the server.
Congratulations! Your Red Hat Storage Server installation is now complete.
4.2. Booting from a PXE Server
To boot using a PXE server, you need a properly configured server, and a network interface in your
computer that supports PXE.
Configure the computer to boot from the network interface. This option is in the BIOS, and may be
labeled Network Boot or Boot Services. Once you properly configure PXE booting, the computer
can boot the Red Hat Storage Server installation system without any other media.
To boot a computer from a PXE server:
1. Ensure that the network cable is attached. The link indicator light on the network socket should be
lit, even if the computer is not switched on.
2. Switch on the computer.
3. A menu screen appears. Press the number key that corresponds to the desired option.
If your PC does not boot from the netboot server, ensure that the BIOS is configured to boot first from
the correct network interface. Some BIOS systems specify the network interface as a possible boot
device, but do not support the PXE standard. Refer to your hardware documentation for more
information.
Important
Check SELinux status on the Red Hat Storage server after installation. You must ensure to
disable, if found to be enforced or permissive. For more information on enabling and disabling
SELinux, refer to
https://access.redhat.com/knowledge/docs/en-
Red Hat Storage 2.0 Installation Guide
16

Chapter 5. Registering to Red Hat Network (RHN)
After you have successfully installed Red Hat Storage, you must first register the target system to Red
Hat Network and subscribe to the required software channels.
To subscribe to the Red Hat Storage Channels using RHN Classic:
1. Run the rhn_register command to register the system with Red Hat Network. To complete
registration successfully you will need to supply your Red Hat Network username and password.
Follow the on screen prompts to complete registration of the system.
# rhn_register
2. Subscribe to Required Channels.
You must subscribe the system to the required channels using either the web interface to Red Hat
Network or the command line rhn-channel command.
A. Using the rhn-channel Command
Run the rhn-channel command to subscribe the system to each of the required
channels. The commands which need to be run are:
# rhn-channel --add --channel=rhel-x86_64-server-6-rhs-2.0
# rhn-channel --add --channel=rhel-x86_64-server-sfs-6.2.z
Run the following command to ensure the system is registered successfully.
# rhn-channel -l
rhel-x86_64-server-6-rhs-2.0
rhel-x86_64-server-6.2.z
rhel-x86_64-server-sfs-6.2.z
B. Using the Web Interface to Red Hat Network.
To add a channel subscription to a system from the web interface:
1. Log on to Red Hat Network (
).
2. Move the mouse cursor over the Subscriptions link at the top of the screen, and
then click the Registered Systems link in the menu that appears.
3. Select the system to which you are adding channels from the list presented on the
screen, by clicking the name of the system.
4. Click Alter Channel Subscriptions in the Subscribed Channels section
of the screen.
5. Select the channels to be added from the list presented on the screen. Red Hat
Storage requires:
RHEL EUS Server Scalable File System (v. 6.2.z for x86_64 )
On the same page, expand the node for Additional Services Channels for Red
Hat Enterprise Linux 6.2 for x86_64 and select Red Hat Storage
Server 2.0 (RHEL 6.2.z for x86_64 ).
6. Click the Change Subscription button to finalize the change.
After the page refreshes, select Details tab to verify if your system is subscribed to
the appropriate channels.
The system is now registered with Red Hat Network and subscribed to the channels required for Red
Hat Storage installation.
Chapter 5. Registering to Red Hat Network (RHN)
17

Red Hat Storage 2.0 Installation Guide
18
Chapter 6. Setting up Software Updates
Red Hat strongly recommends you update your Red Hat Storage software regularly with the latest
security patches and upgrades. Associate your system with a content server to update existing content
or to install new content. This ensures that your system is up-to-date with security updates and
upgrades.
If you wish to install software updates periodically, use the following command:
# yum update
6.1. Updating Red Hat Storage
To keep your Red Hat Storage system up-to-date, associate the system with the RHN or your locally-
managed content service. This ensures your system automatically stays up-to-date with security
patches and bug fixes.
Note
Asynchronous errata update releases of Red Hat Storage includes all fixes that were released
asynchronously since the last release as a cumulative update.
To manually update the system, run the following command:
# yum update
The update process automatically restarts the glusterd management deamon. The glusterfs server
processes, glusterfsd is not restarted by default since restarting this daemon affects the active read
and write operations.
After all the nodes in the cluster are updated, the volume must be restarted for the changes to be
applied. Red Hat recommends that you restart the system when there are no active read and write
operations running on the cluster.
To restart the volume, run the following commands:
# gluster volume stop VOLNAME
# gluster volume start VOLNAME
For example, to start VOLNAME volume:
# gluster volume start VOLNAME
Starting VOLNAME has been successful
For example, to stop VOLNAME volume:
# gluster volume stop VOLNAME
Stopping ...
Chapter 6. Setting up Software Updates
19
Chapter 7. Managing glusterd Service
After installing Red Hat Storage, glusterd service is started automatically on all the servers in your
trusted storage pool. You can also manually start and stop glusterd service.
Red Hat Storage allows you to dynamically change the configuration of GlusterFS volumes without
having to restart servers or remount volumes on clients. You can perform this type of elastic volume
management using the GlusterFS daemon called glusterd.
Using the gluster command line, logical storage volumes are decoupled from physical hardware,
allowing you to grow, shrink, and migrate storage volumes without any application downtime. As you add
storage, the volumes are rebalanced across the cluster making it always available online regardless of
changes to the underlying hardware.
7.1. Starting and Stopping glusterd Manually
This section describes how to start and stop glusterd service manually.
To start glusterd manually, enter the following command:
# /etc/init.d/glusterd start
or
#service glusterd start
To stop glusterd manually, enter the following command:
# /etc/init.d/glusterd stop
or
#service glusterd stop
Red Hat Storage 2.0 Installation Guide
20

Chapter 8. Using the Gluster Command Line Interface
The Gluster CLI is a command line utility that simplifies configuration and management of your storage
environment. The Gluster CLI is similar to the LVM (Logical Volume Manager) CLI or ZFS CLI, but across
multiple storage servers. You can use the Gluster CLI online, while volumes are mounted and active. Red
Hat Storage automatically synchronizes volume configuration information across all servers.
Using the Gluster CLI, you can create new volumes, start volumes, and stop volumes. You can also add
bricks to volumes, remove bricks from existing volumes, as well as change translator settings, among
other operations.
You can also use the commands to create scripts for automation, as well as use the commands as an
API to allow integration with third-party applications.
Note
If you suffix --mode=script to any command on the CLI, the specified action is executed
automatically without any prompts for confirmation.
Running the Gluster CLI
You can run the Gluster CLI on any Red Hat Storage server either by invoking the commands or by
running the Gluster CLI in an interactive mode. You can also use the gluster command remotely using
SSH.
To run commands directly:
# gluster peer command
For example:
# gluster peer status
To run the Gluster CLI in interactive mode
# gluster
You can execute gluster commands from the CLI prompt:
gluster> command
For example:
To view the status of the peer server:
# gluster
gluster> peer status
Displays the status of the peer.
To view the gluster help:
# gluster
gluster> help
Displays the list of gluster commands and options.
Chapter 8. Using the Gluster Command Line Interface
21

Revision History
Revision 1-21.4 00
2013-10-31
Rüdiger Landmann
Rebuild with publican 4.0.0
Revision 1-21
Mon Mar 28 2013
Anjana Suparna Sriram
Updated Booting from a PXE Server section.
Revision 1-20
Mon Mar 28 2013
Anjana Suparna Sriram
Updated Booting from a PXE Server section.
Revision 1-19
Mon Mar 25 2013
Anjana Suparna Sriram
Updated the chapter 5 based on PM's feedback.
Revision 1-18
Fri Mar 22 2013
Anjana Suparna Sriram
Updated the guide with instructions on how to register to RHN and added a new image for network
configuration.
Revision 1-16
Mon Oct 01 2012
Anjana Suparna Sriram
Bug fixes and updated the guide with instructions on how to update Red Hat Storage.
Revision 1-13
Tue Sep 04 2012
Anjana Suparna Sriram
Bug fixes.
Revision 1-1
Tue Jun 26 2012
Divya Muntimadugu
Version for 2.0 GA release.
Revision 1-0
Thu Jun 21 2012
Anjana Suparna Sriram
Draft
Red Hat Storage 2.0 Installation Guide
22
Document Outline
- Table of Contents
- Preface
- Chapter 1. Introduction
- Chapter 2. Obtaining Red Hat Storage
- Chapter 3. Planning Red Hat Storage Installation
- Chapter 4. Installing Red Hat Storage
- Chapter 5. Registering to Red Hat Network (RHN)
- Chapter 6. Setting up Software Updates
- Chapter 7. Managing glusterd Service
- Chapter 8. Using the Gluster Command Line Interface
- Revision History
Wyszukiwarka
Podobne podstrony:
Red Hat Storage 2 0 Installation Guide en US
Red Hat Storage 2 0 2 0 Release Notes en US
Red Hat Storage 2 0 Quick Start Guide en US
Red Hat Storage 2 1 Quick Start Guide en US
Red Hat Storage 2 1 Console Command Line Shell Guide en US
Red Hat Enterprise Virtualization 3 2 Command Line Shell Guide en US
Red Hat Storage 2 1 2 1 Update 2 Release Notes en US
Red Hat Storage 2 0 2 0 Update 4 and Update 5 Release Notes en US
Red Hat Enterprise Linux 6 Beta Virtualization Getting Started Guide en US
Red Hat Enterprise Virtualization 3 1 User Portal Guide en US
Red Hat Enterprise Virtualization 3 2 User Portal Guide en US
Red Hat Enterprise Linux 6 Performance Tuning Guide en US
Red Hat Enterprise MRG 2 Tuna User Guide en US
Red Hat Enterprise Linux 6 Migration Planning Guide en US
Red Hat Enterprise Virtualization 3 0 Hypervisor Deployment Guide en US
Red Hat Enterprise Virtualization 3 3 Command Line Shell Guide en US
Red Hat Enterprise Virtualization 3 0 User Portal Guide en US
Red Hat Enterprise Linux 6 Migration Planning Guide en US
Red Hat Enterprise Linux 6 Virtualization Getting Started Guide en US
więcej podobnych podstron