
Tom Chen
SMU
tchen@engr.smu.edu
www.engr.smu.edu/~tchen
Malware Research at SMU

TC/BT/11-5-04
SMU Engineering p.
2
•
About SMU and Me
•
Virus Research Lab
•
Early Worm Detection
•
Epidemic Modeling
•
New Research Interests
Outline

TC/BT/11-5-04
SMU Engineering p.
3
About SMU
•
Small private university with 6 schools -
engineering, sciences, arts, business, law,
theology
•
6,300 undergrads; 3,600 grads; 1,200
professional (law, theology) students
•
School of Engineering: 51 faculty in 5
departments
•
Dept of EE: specialization in signal
processing, communications, networking,
optics

TC/BT/11-5-04
SMU Engineering p.
4
About Me
•
BS and MS in EE from MIT, PhD in EE
from U. California, Berkeley
•
GTE (Verizon) Labs: research in ATM
switching, traffic modeling/control, network
operations
•
1997 joined EE Dept at SMU: traffic
control, network security

TC/BT/11-5-04
SMU Engineering p.
5
Research Interests
•
Convergence of traffic control and Internet
threats
-
Large-scale traffic effects of worm epidemics
-
Traffic control (packet classification, filtering/
throttling) for detection and defenses
•
Deception-based attacks and defenses
-
Social engineering, honeypots

TC/BT/11-5-04
SMU Engineering p.
6
Motivations
•
Worms and social engineering attacks
(phishing, spam) have widespread effects
in Internet
-
Top worms (Loveletter, Code Red,
Slammer,...) causes billions in damages
-
78% organizations hit by virus/worm, $200k
average damage per organization [2004 FBI/
CSI survey]
-
40% Fortune 100 companies hit [Symantec
report]
TC/BT/11-5-04
SMU Engineering p.
7
1979
1983
1988
1999
2000
2001
2003
1992
1995
• 25 years- problem continues to get worse
• We want to apply theories (traffic control,
epidemiology) towards detection and control
John Shoch and Jon Hupp at Xerox
Fred Cohen
Robert Morris Jr
Melissa (March), ExploreZip (June)
Love Letter (May)
Sircam (July), Code Red I+II (July-Aug.), Nimda (Sep.)
Slammer (Jan.), Blaster (Aug.), Sobig.F (Aug.)
Virus creation toolkits, Self Mutating Engine
Concept macro virus
2004
MyDoom, Netsky

TC/BT/11-5-04
SMU Engineering p.
8
•
Virus research lab
•
Early worm detection
•
Epidemic modeling
Research Activities
TC/BT/11-5-04
SMU Engineering p.
9
Virus Research Lab
•
Distributed computers in EE building and
Business School
Internet
Campus
network
Cox Business School
EE Building

TC/BT/11-5-04
SMU Engineering p.
10
Virus Research Lab (cont)
•
Intrusion detection systems to monitor live
traffic
-
Snort (network IDS), Prelude (event
correlation), Samhain (host-based IDS),
Nagios (network manager)
•
Honeypots for worm detection/capture
-
Honeyd (honeypot), Logwatch (log
monitoring)

TC/BT/11-5-04
SMU Engineering p.
11
Virus Research Lab (cont)
•
Network/worm simulator (Java)
-
To simulate different worm behaviors in
different network topologies
-
To find worm-resistant network topologies

TC/BT/11-5-04
SMU Engineering p.
12
Early Detection of Worms
•
Goal is global system including honeypots
for early warning of new worm outbreaks
•
Honeypots are traditionally used for post-
attack forensics
•
For early warning, honeypots need
augmentation with real-time analysis

TC/BT/11-5-04
SMU Engineering p.
13
Early Detection (cont)
•
Jointly with Symantec to enhance their
DeepSight Threat Management System
-
DeepSight collects log data from hosts,
firewalls, IDSs from 20,000 organizations in
180 countries
-
Symantec correlates and analyzes traffic data
to track attacks by type, source, time, targets
TC/BT/11-5-04
SMU Engineering p.
14
Early Detection (cont)
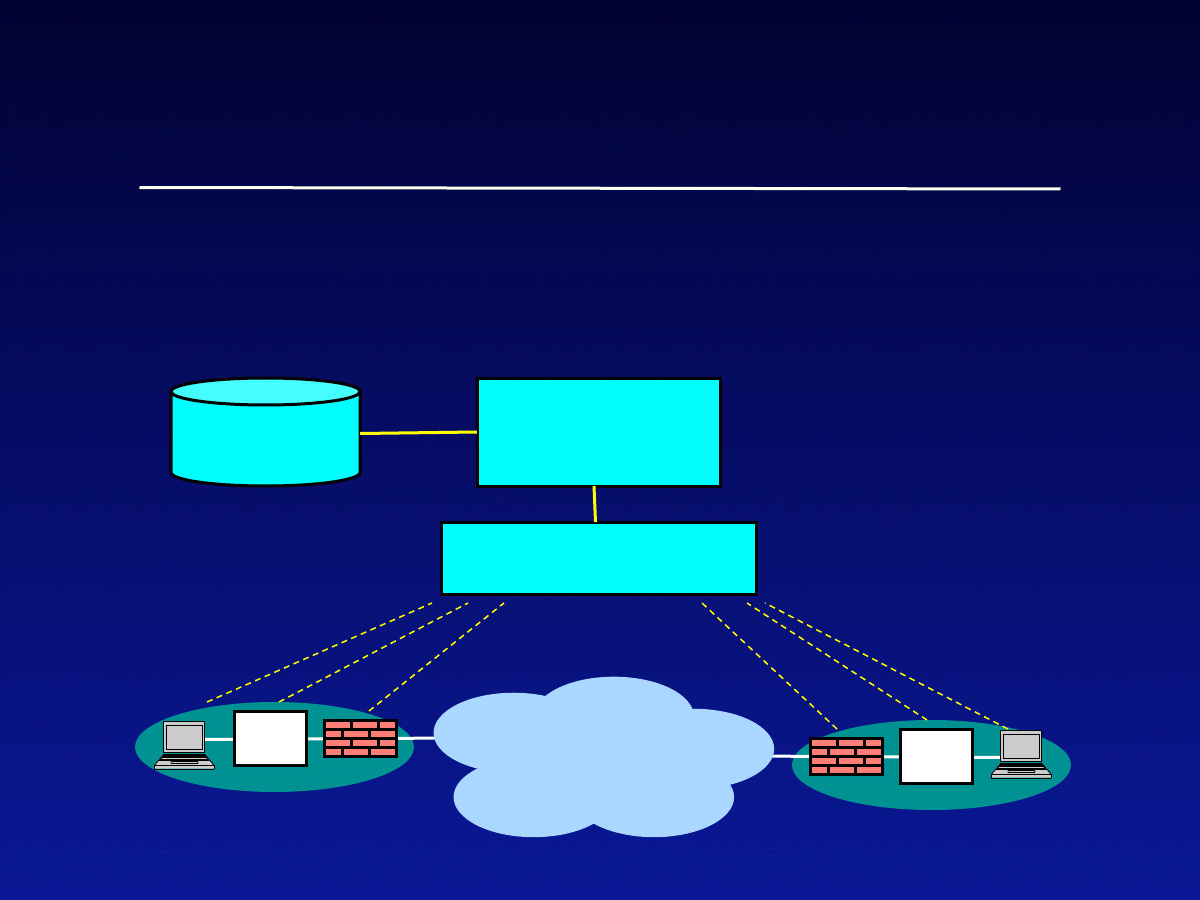
•
Architecture of DeepSight
IDS
IDS
Data collection
Correlation
+ analysis
Signatures
Internet

TC/BT/11-5-04
SMU Engineering p.
15
Early Detection (cont)
•
We want to add honeypots to DeepSight
•
Honeypot sensors have advantage of low
false positives (a problem with IDSs)
•
DeepSight has correlation/analysis engine
to make honeypots useful for real-time
detection
-
Modifications to correlation engine needed

TC/BT/11-5-04
SMU Engineering p.
16
Epidemic Modeling
•
Epidemic models predict spreading of
diseases through populations
-
Deterministic and stochastic models
developed over 250 years
-
Helped devise vaccination strategies, eg,
smallpox
•
Our goal is to adapt epidemic models to
computer viruses and worms
-
Take into account network congestion

TC/BT/11-5-04
SMU Engineering p.
17
Basic Epidemic Model
•
Assumes all hosts are initially Susceptible,
can become Infected after contact with an
Infected
-
Assumes fixed population and random
contacts
•
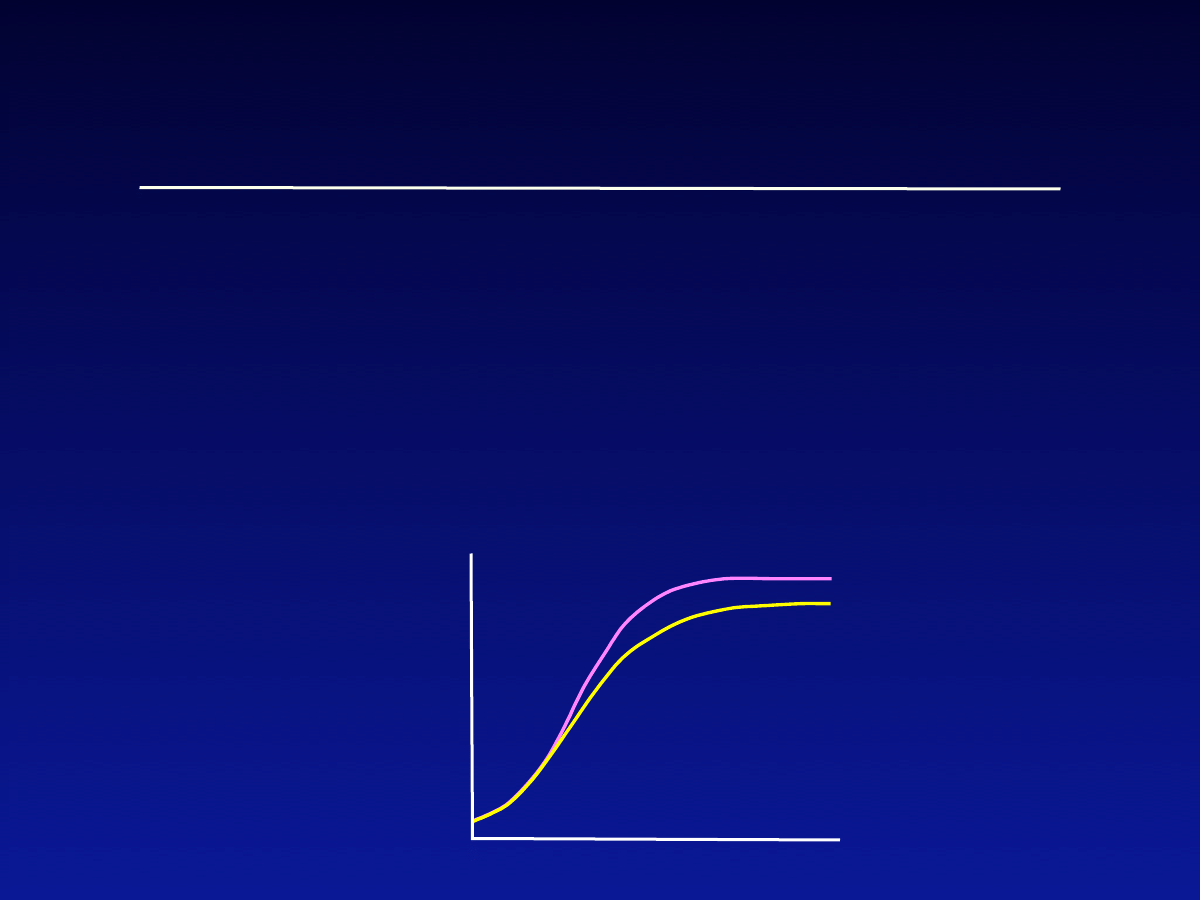
Then basic epidemic model predicts
number of Infected hosts has logistic
growth
TC/BT/11-5-04
SMU Engineering p.
18
Number
infected
Observed
Predicted
Basic Epidemic (cont)
•
Logistic equation predicts “S” growth
•
Observed worm outbreaks (eg, Code Red)
tend to slow down more quickly than
predicted

TC/BT/11-5-04
SMU Engineering p.
19
Basic Epidemic (cont)
•
Initial rate is exponential: random
scanning is efficient when susceptible
hosts are many
•
Later rate slow downs: random scanning
is inefficient when susceptible hosts are
few
•
Spreading rate also slows due to network
congestion caused by heavy worm traffic

TC/BT/11-5-04
SMU Engineering p.
20
Dynamic Quarantine
•
Recent worms spread too quickly for
manual response
•
Dynamic quarantine tries to isolate worm
outbreak from spreading to other parts of
Internet
-
Cisco and Microsoft proposals
-
Rate throttling proposals
•
Epidemic modeling can evaluate
effectiveness

TC/BT/11-5-04
SMU Engineering p.
21
Quarantining (cont)
•
“Community of households” epidemic
model assumes
-
Population is divided into households
-
Infection rates within households can be
different than between households
•
Similar to structure of Internet as “network
of networks”
-
Household = organization’s network
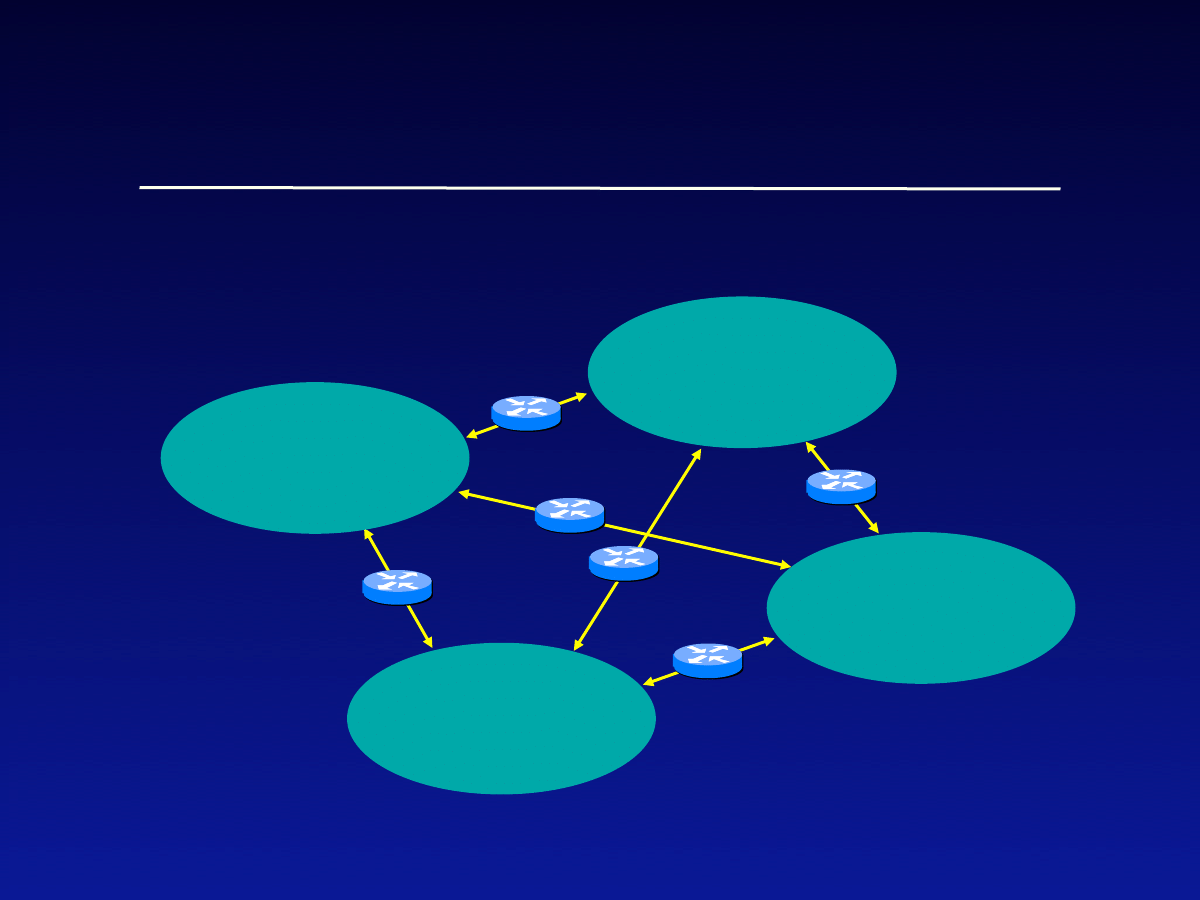
TC/BT/11-5-04
SMU Engineering p.
22
Quarantining (cont)
Network
(household)
Network
(household)
Network
(household)
Network
(household)
Inter-network infection
rates -- Control these
routers for quarantining
Intra-network
infection rates
Routers might
be actually ISPs

TC/BT/11-5-04
SMU Engineering p.
23
Quarantining
•
As outbreak spreads, congestion causes
inter-network infection rates to slow down
outbreak naturally (seen empirically)
•
Dynamic quarantining: quickly shutting
down or throttling inter-network rates
should slow down outbreak faster
-
Reaction time is critical
-
In practice, rate throttling may be preferred as
gentler than blocking

TC/BT/11-5-04
SMU Engineering p.
24
New Research Interests
•
Phishing
-
Damages: $1.2 billion to US financial
organizations; 1.8 million consumer victims
[Symantec]
-
1,974 new unique phishing attacks in July
2004; 50% monthly growth rate in attacks
[Anti-Phishing Working Group]

TC/BT/11-5-04
SMU Engineering p.
25
Phishing (cont)
•
Our approach: email honeypots
(spamtraps) are honeypots modified to
receive and monitor email at fake
addresses
-
Reliably capture spam
•
Modify spam filters to detect phishing
emails
•
Analyze contents and links to fake Web
sites, generate new email filter rules

TC/BT/11-5-04
SMU Engineering p.
26
New Research (cont)
•
Bot nets
-
Symantec tracking 30,000+ compromised
hosts; around 1,000 variants each of Gaobot,
Randex, Spybot
-
Used for remote control, information theft,
DDoS
-
Potentially useful for fast launching worms
-
Perhaps used by organized crime

TC/BT/11-5-04
SMU Engineering p.
27
Bot Nets (cont)
•
Bots typically use IRC (Internet relay chat)
channels for command and control
•
We are seeking signs of bot nets on IRC
channels

TC/BT/11-5-04
SMU Engineering p.
28
Conclusions
•
Interests in traffic control and modeling
applied to network security
-
Early detection, dynamic quarantining,
epidemic modeling
•
Interests in deception-based threats and
defenses
-
Phishing, honeypots
Wyszukiwarka
Podobne podstrony:
Understanding the productives economy during the bronze age trought archeometallurgical and palaeo e
NSA Quantum Computer Research at LPS 2005
zooming in and out connecting individuals and collectivities at the frontiers of organizational netw
2 Marketing Research&Laterial Thinking
AT kurs analityka giełdowego 3
WISL Pods I cyklu AT
Aprobata na zaprawe murarska YTONG AT 15 2795
120222160803 english at work episode 2
Jim Hall at All About Jazz
Access to History 001 Gas Attack! The Canadians at Ypres, 1915
AT 15 3847 99
AT AT mini
Legenda AT, Policja, AT
Body language is something we are aware of at a subliminal level
121024104303 bbc english at work episode 37
Investigations at Souskiou Laona settlement, Dhiarizos Valley, 2005
AT 15 4948 2002 FID
więcej podobnych podstron