
• Unauthorised entry to IT cabinets or asset movement raises immediate alarm
• Servers, PCs, switching equipment are all monitored 24/7
• Records the movement of 3
rd
party personnel within facility
• Wireless
• Reduces Total Cost of Ownership of IT estate
• Saves time on engineer callouts by knowing exact location of equipment
• Centralised “Change Control” management
• “Real time” automated audit every 30 seconds, for lifetime of asset
• Enhances corporate integrity – more granular security down to individual components
• Integrates with third party systems and acts a a visible deterrent to thieves
• Fast modular installation and low maintenance
The aspects PRO benefits…
DATA
CE
NTRE
PR
O
T
EC
TIO
N
• “The cost of implementing the system was instantly justified”
– Norman Jinks, DfES
• “With Aspects we know the whereabouts of all our assets, all the time”
- Anna Williams, WPP
• “The system was installed and cost justified within 6 months”
- Chris Ferris, BT Ignite
Our Customers say…
Fortune 1000 companies experienced losses
of more than $45 billion from thefts of
proprietary information. (ASIS)
It is estimated that full-time employees, as
well as contractors with access to the
workplace, are responsible for 75% of all cases
involving corporate computer theft. (FBI, 1997)
Data Centre rooms
under attack
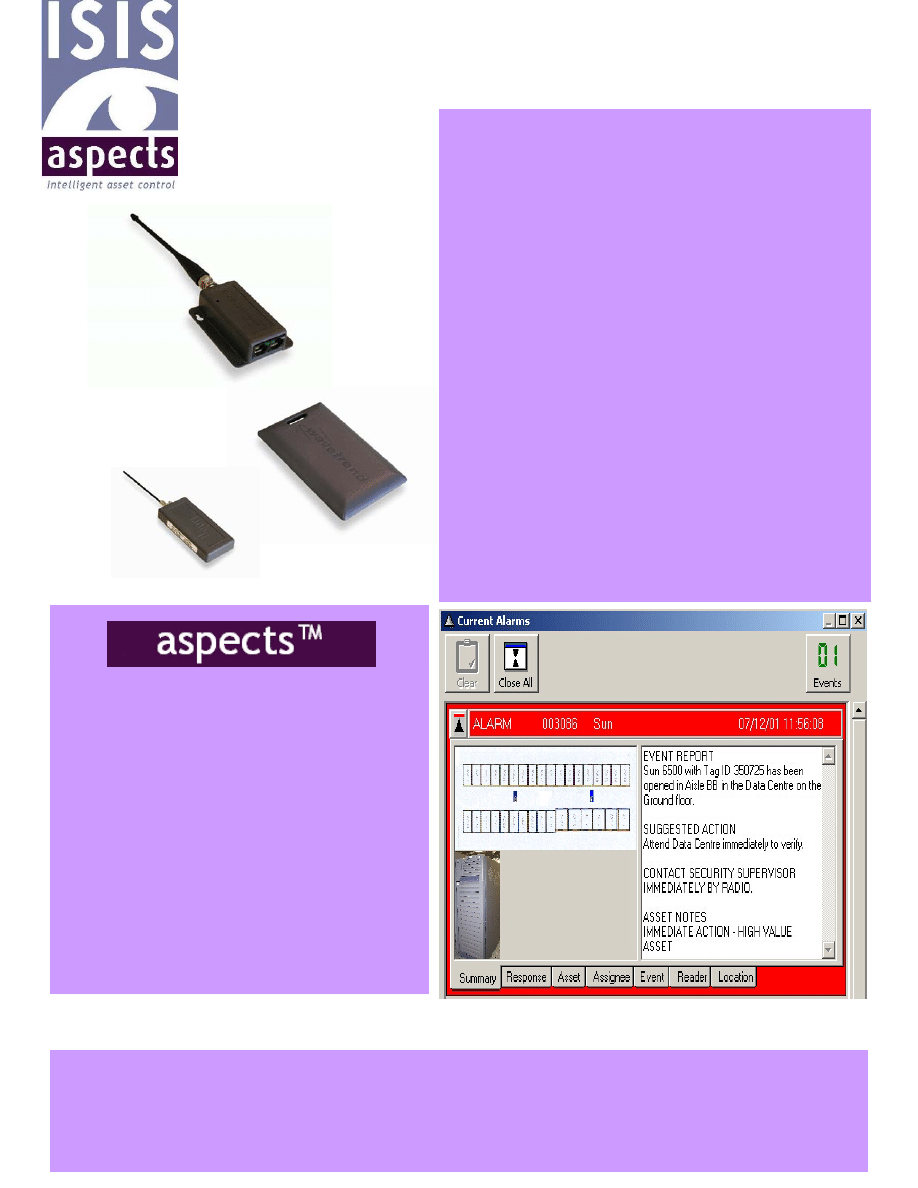
• Windows NT & 2000
• Real-time alarm graphics
• Easy-to-use authorisation for engineer
maintenance
• Server alarm sensitivity individually
programmable
• Historical log of all alarms, legitimate
asset and engineer movement
• Fast tag/asset registration
• Real-time asset register 24/7/365
• Multi-user – password protected
• Analysis Tools
ISIS -
Consultancy, Security, Audits and Professional Services
Call us now for free consultation and advice
+44 20 7259 9212
www.isis.co.uk
Technical Concepts
• Discreet, miniature, movement-sensing RF
tags monitor servers & components
• Personnel cards track and record movement
of engineers inside facility
• Small RF domino tags detect open/close of IT
cabinet doors
• All tags have unique ID
• Tags communicate with RF sensors located
inside the facility
• Sensors linked on daisy chain to aspects PRO
• Tag ranges up to 40 metres
• Tag battery life expectancy 5 years
• Tags reusable
• All tags are anti-tamper
• Radio emissions do not affect operability of
computer equipment
The Service …
Proven Technology
The Technology …
Wyszukiwarka
Podobne podstrony:
Mechanika Plynow Lab, Sitka Pro Nieznany
Corel Paint Shop Pro X Obrobka zdjec cyfrowych cwiczenia
marcinstolp pro
Mechanika Budowli pro 2
algorytmy, programy, jezyki pro Nieznany (2)
Krakow nowapr1 nowa kryt1,2 pro Nieznany
fiz egzamin opracowanie pro
1d analiza interasariuszy, pro Nieznany
IDX PRO
katalog nobiles pro
aqua pro io pl 1109
Ansmann Powerline 4 Pro PL
Dolby Surround eller Dolby Surround Pro Logic
Gradiente PRO 2000
Pro Prochloraz 450 EC
Pro Staff 3 PPC 3H id 392593 Nieznany
met pro Oscyloskop, AGH IMIR Mechanika i budowa maszyn, II ROK, Metrologia Tyka Haduch, Metrologia,
więcej podobnych podstron