
Ochrona sieci lokalnych LAN
BST Laboratorium V

Port Security – CLI Commands
switchport mode access
Switch(config-if)#
•
Sets the interface mode as access
switchport port-security
Switch(config-if)#
•
Enables port security on the interface
switchport port-security maximum value
Switch(config-if)#
•
Sets the maximum number of secure MAC addresses for
the interface (optional)
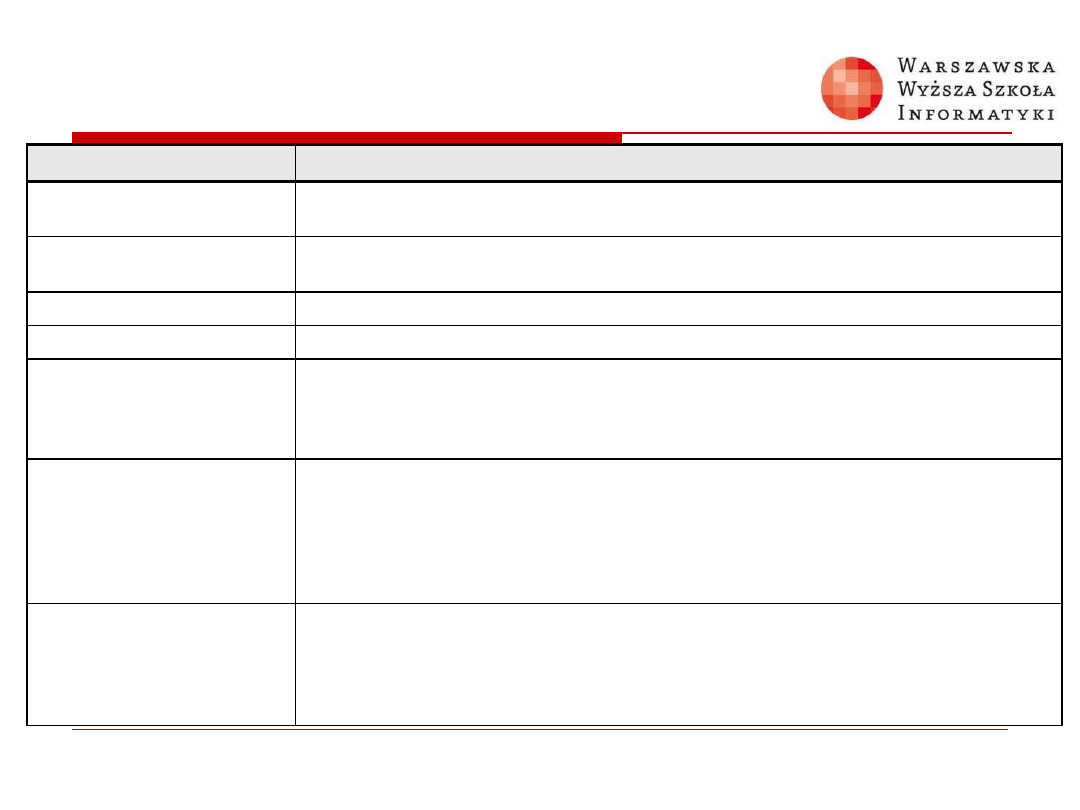
Switchport Port-Security Parameters
Parameter
Description
mac-address mac-address
(Optional) Specify a secure MAC address for the port by entering a 48-bit MAC aaddress. You can add additional
secure MAC addresses up to the maximum value configured.
vlan vlan-id
(Optional) On a trunk port only, specify the VLAN ID and the MAC address. If no VLAN ID is specified, the native
VLAN is used.
vlan access
(Optional) On an access port only, specify the VLAN as an access VLAN.
vlan voice
(Optional) On an access port only, specify the VLAN as a voice VLAN
mac-address sticky
[mac-address]
(Optional) Enable the interface for sticky learning by entering only the mac-address sticky keywords. When sticky
learning is enabled, the interface adds all secure MAC addresses that are dynamically learned to the running
configuration and converts these addresses to sticky secure MAC addresses.
Specify a sticky secure MAC address by entering the mac-address sticky mac-address keywords..
maximum value
(Optional) Set the maximum number of secure MAC addresses for the interface. The maximum number of secure
MAC addresses that you can configure on a switch is set by the maximum number of available MAC
addresses allowed in the system. The active Switch Database Management (SDM) template determines this
number. This number represents the total of available MAC addresses, including those used for other Layer 2
functions and any other secure MAC addresses configured on interfaces.
The default setting is 1.
vlan [vlan-list]
(Optional) For trunk ports, you can set the maximum number of secure MAC addresses on a VLAN. If the vlan
keyword is not entered, the default value is used.
n
vlan: set a per-VLAN maximum value.
n
vlan vlan-list: set a per-VLAN maximum value on a range of VLANs separated by a hyphen or a series of
VLANs separated by commas. For nonspecified VLANs, the per-VLAN maximum value is used.

Port Security Violation Configuration
switchport port-security mac-address sticky
Switch(config-if)#
Enables sticky learning on the interface (optional)
switchport port-security violation {protect | restrict |
shutdown}
Switch(config-if)#
Sets the violation mode (optional)
switchport port-security mac-address mac-address
Switch(config-if)#
Enters a static secure MAC address for the interface
(optional)
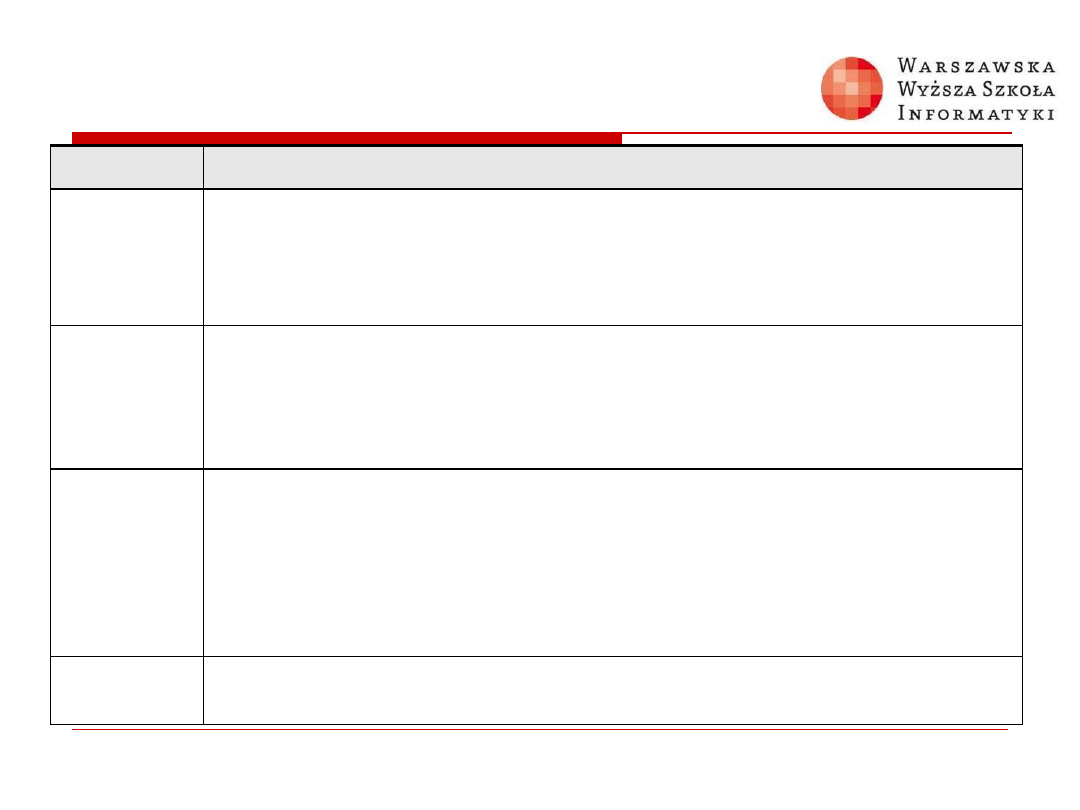
Switchport Port-Security
Violation Parameters
Parameter
Description
protect
(Optional) Set the security violation protect mode. When the number of secure MAC
addresses reaches the limit allowed on the port, packets with unknown source
addresses are dropped until you remove a sufficient number of secure MAC addresses
or increase the number of maximum allowable addresses. You are not notified that a
security violation has occurred.
restrict
(Optional) Set the security violation restrict mode. When the number of secure MAC
addresses reaches the limit allowed on the port, packets with unknown source
addresses are dropped until you remove a sufficient number of secure MAC addresses
or increase the number of maximum allowable addresses. In this mode, you are notified
that a security violation has occurred.
shutdown
(Optional) Set the security violation shutdown mode. In this mode, a port security
violation causes the interface to immediately become error-disabled and turns off the
port LED. It also sends an SNMP trap, logs a syslog message, and increments the
violation counter. When a secure port is in the error-disabled state, you can bring it out
of this state by entering the errdisable recovery cause psecure-violation global
configuration command, or you can manually re-enable it by entering the shutdown and
no shut down interface configuration commands.
shutdown
vlan
Set the security violation mode to per-VLAN shutdown. In this mode, only the VLAN on
which the violation occurred is error-disabled.

Port Security Aging Configuration
switchport port-security aging {static | time time | type
{absolute | inactivity}}
Switch(config-if)#
Enables or disables static aging for the secure port or
sets the aging time or type
The aging command allows MAC-Addresses on the
Secure switchport to be deleted after the set aging time
This helps to avoid a situation where obsolete MAC-
Address occupy the table and saturates causing a
violation (when the max number exceeds)
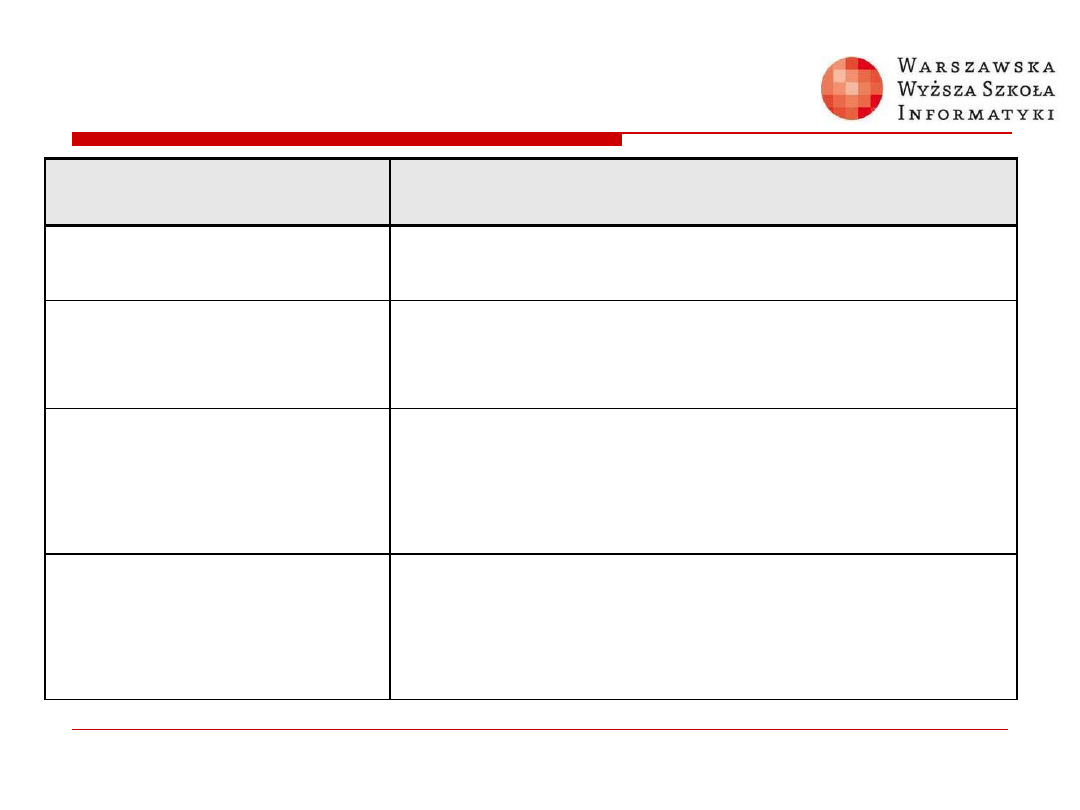
Switchport Port-Security
Aging Parameters
Parameter
Description
static
Enable aging for statically configured secure
addresses on this port.
time time
Specify the aging time for this port. The range is 0 to
1440 minutes. If the time is 0, aging is disabled for
this port.
type absolute
Set absolute aging type. All the secure addresses
on this port age out exactly after the time (minutes)
specified and are removed from the secure address
list.
type inactivity
Set the inactivity aging type. The secure addresses
on this port age out only if there is no data traffic
from the secure source address for the specified
time period.
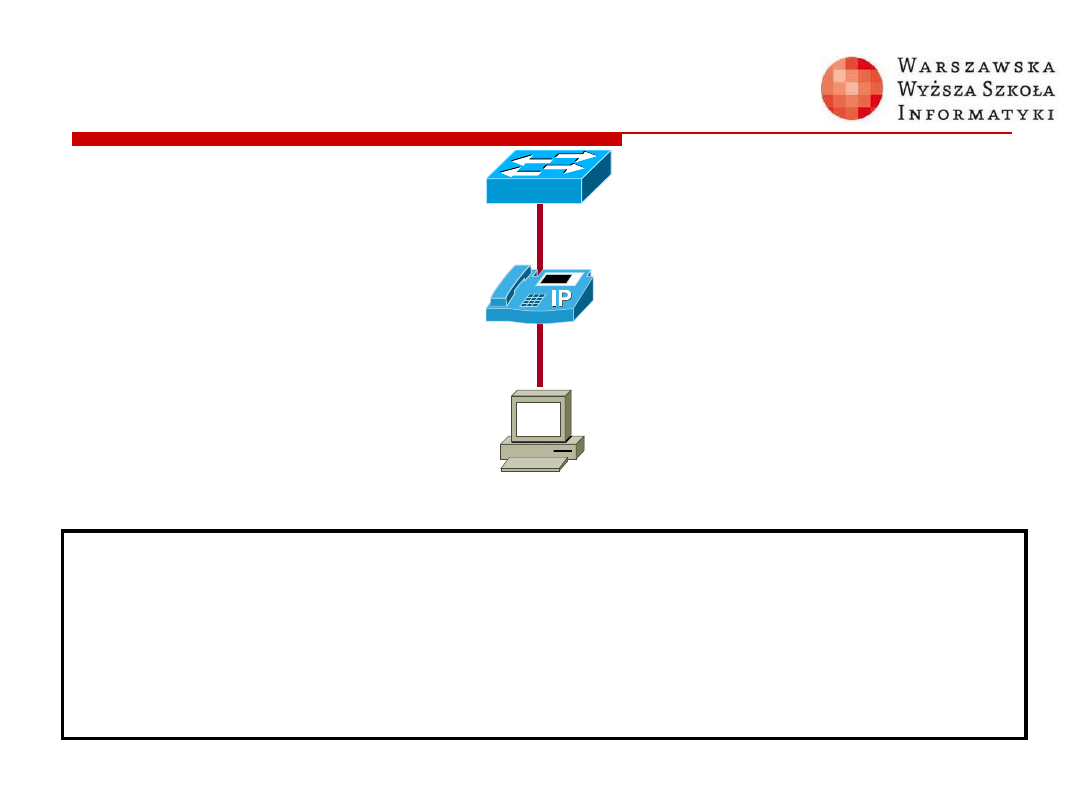
Typical Configuration
switchport mode access
switchport port-security
switchport port-security maximum 2
switchport port-security violation shutdown
switchport port-security mac-address sticky
switchport port-security aging time 120
Switch(config-if)#
S2
PC B
Verification – CLI Commands
sw-class#
show port-security
Secure Port MaxSecureAddr CurrentAddr SecurityViolation Security Action
(Count) (Count) (Count)
---------------------------------------------------------------------------
Fa0/12 2 0 0 Shutdown
---------------------------------------------------------------------------
Total Addresses in System (excluding one mac per port) : 0
Max Addresses limit in System (excluding one mac per port) : 1024
sw-class#
show port-security interface f0/12
Port Security : Enabled
Port status : Secure-down
Violation mode : Shutdown
Maximum MAC Addresses : 2
Total MAC Addresses : 1
Configured MAC Addresses : 0
Aging time : 120 mins
Aging type : Absolute
SecureStatic address aging : Disabled
Security Violation Count : 0
View Secure MAC Addresses
sw-class#
show port-security address
Secure Mac Address Table
-------------------------------------------------------------------
Vlan Mac Address Type Ports Remaining Age
(mins)
----
-----------
----
-----
-------------
1 0000.ffff.aaaa SecureConfigured Fa0/12 -
-------------------------------------------------------------------
Total Addresses in System (excluding one mac per port) : 0
Max Addresses limit in System (excluding one mac per port) : 1024
Configure Portfast
Command
Description
Switch(config-if)# spanning-tree
portfast
Enables PortFast on a Layer 2 access port and forces it to enter the
forwarding stateimmediately.
Switch(config-if)# no spanning-
tree portfast
Disables PortFast on a Layer 2 access port. PortFast is disabled by
default.
Switch(config)# spanning-tree
portfast default
Globally enables the PortFast feature on all nontrunking ports.
Switch# show running-config
interface type slot/port
Indicates whether PortFast has been configured on a port.
Server
Workstation
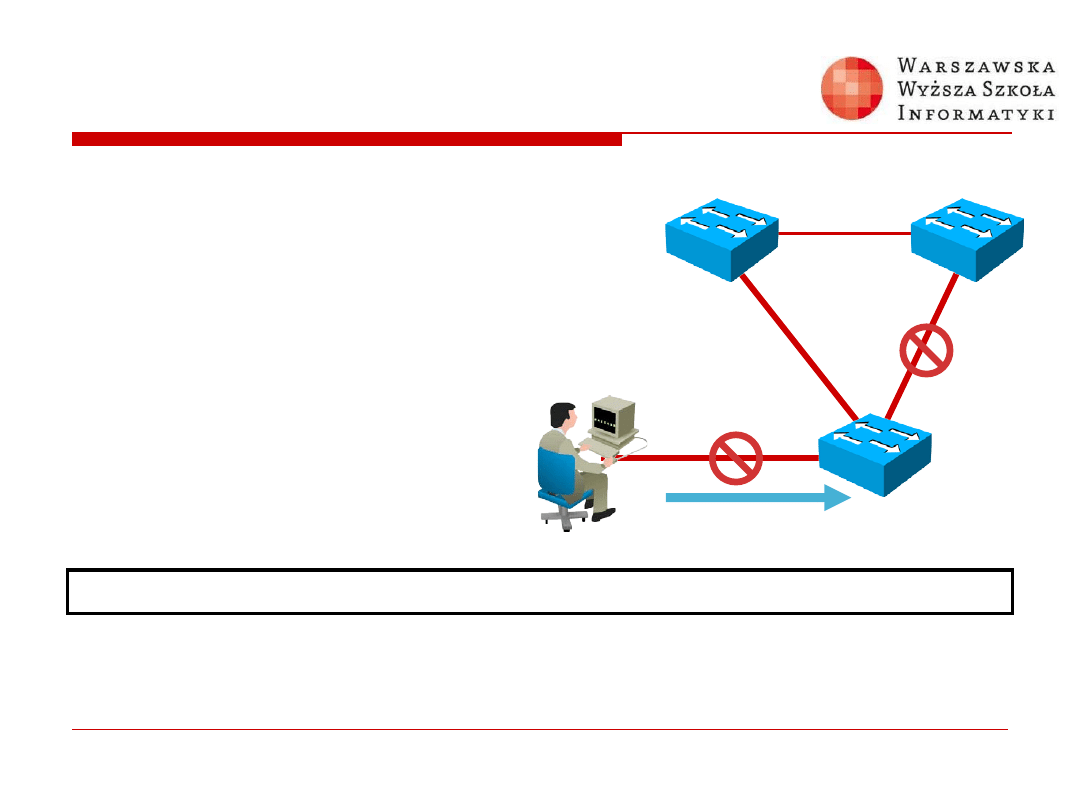
BPDU Guard
Switch(config)#
spanning-tree portfast bpduguard default
Globally enables BPDU guard on all ports with PortFast enabled
F
F
F
F
F
B
Root
Bridge
BPDU
Guard
Enabled
Attacker
STP
BPDU

Display the State of Spanning Tree
Switch# show spanning-tree summary totals
Root bridge for: none.
PortFast BPDU Guard is enabled
UplinkFast is disabled
BackboneFast is disabled
Spanning tree default pathcost method used is short
Name Blocking Listening Learning Forwarding STP Active
-------------------- -------- --------- -------- ---------- ----------
1 VLAN 0 0 0 1 1
<output omitted>
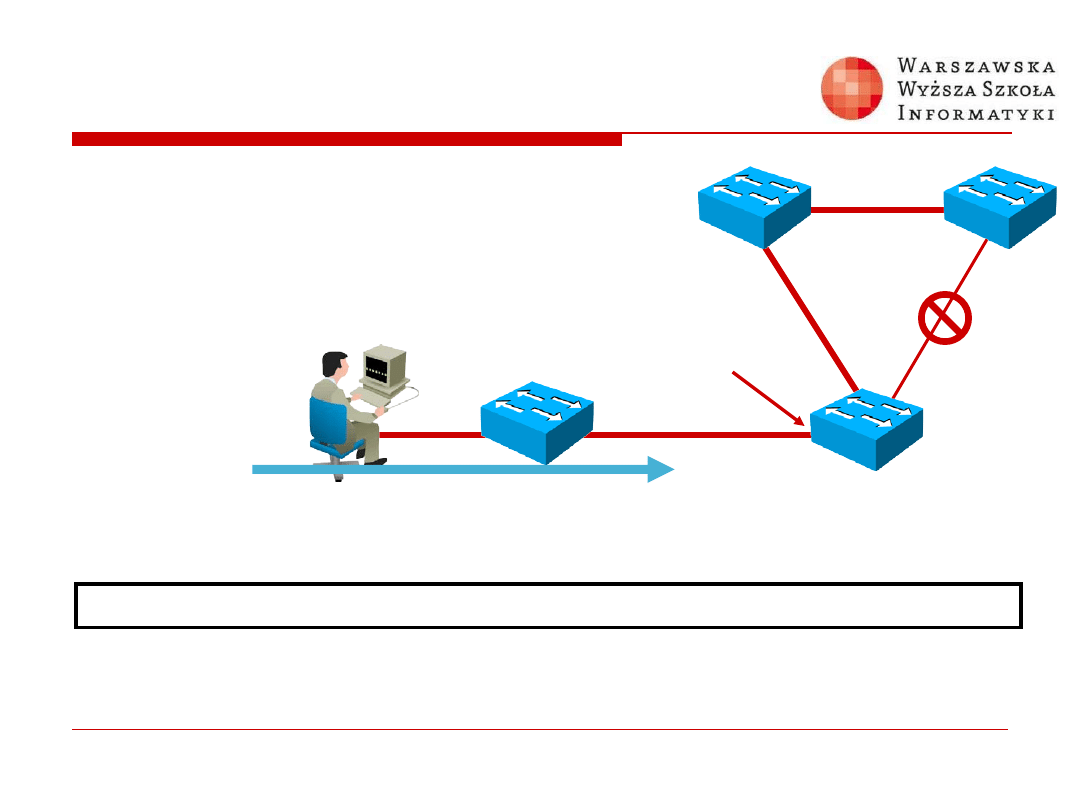
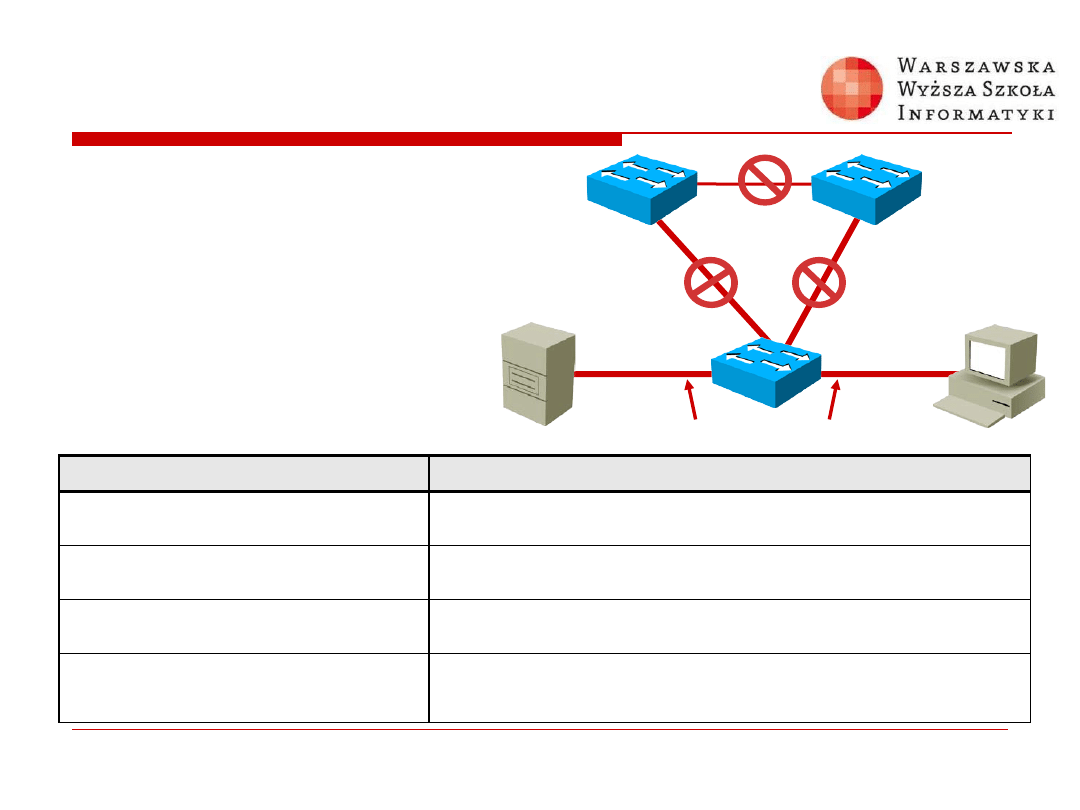
Root Guard
Switch(config-if)#
spanning-tree guard root
Enables root guard on a per-interface basis
Root Bridge
Priority = 0
MAC Address =
0000.0c45.1a5d
F
F
F
F
F
B
F
STP BPDU
Priority = 0
MAC Address = 0000.0c45.1234
Root
Guard
Enabled
Attacker

Verify Root Guard
Switch# show spanning-tree inconsistentports
Name Interface Inconsistency
-------------------- ---------------------- ------------------
VLAN0001 FastEthernet3/1 Port Type Inconsistent
VLAN0001 FastEthernet3/2 Port Type Inconsistent
VLAN1002 FastEthernet3/1 Port Type Inconsistent
VLAN1002 FastEthernet3/2 Port Type Inconsistent
VLAN1003 FastEthernet3/1 Port Type Inconsistent
VLAN1003 FastEthernet3/2 Port Type Inconsistent
VLAN1004 FastEthernet3/1 Port Type Inconsistent
VLAN1004 FastEthernet3/2 Port Type Inconsistent
VLAN1005 FastEthernet3/1 Port Type Inconsistent
VLAN1005 FastEthernet3/2 Port Type Inconsistent
Number of inconsistent ports (segments) in the system :10

Storm Control Configuration
Enables storm control
Specifies the level at which it is enabled
Specifies the action that should take place when the
threshold (level) is reached, in addition to filtering traffic
Switch(config-if)# storm-control broadcast level 75.5
Switch(config-if)# storm-control multicast level pps
2k
1k
Switch(config-if)# storm-control action shutdown
Storm Control Parameters
Parameter
Description
broadcast
This parameter enables broadcast storm control on the interface.
multicast
This parameter enables multicast storm control on the interface.
unicast
This parameter enables unicast storm control on the interface.
level level [level-low]
Rising and falling suppression levels as a percentage of total bandwidth of the port.
•
level: Rising suppression level. The range is 0.00 to 100.00. Block the flooding of storm
packets when the value specified for level is reached.
•
level-low: (Optional) Falling suppression level, up to two decimal places. This value must
be less than or equal to the rising suppression value.
level bps bps [bps-low]
Specify the rising and falling suppression levels as a rate in bits per second at which traffic is
received on the port.
•
bps: Rising suppression level. The range is 0.0 to 10000000000.0. Block the flooding of
storm packets when the value specified for bps is reached.
•
bps-low: (Optional) Falling suppression level, up to one decimal place. This value must be
equal to or less than the rising suppression value.
level pps pps [pps-low]
Specify the rising and falling suppression levels as a rate in packets per second at which traffic
is received on the port.
•
pps: Rising suppression level. The range is 0.0 to 10000000000.0. Block the flooding of
storm packets when the value specified for pps is reached.
•
pps-low: (Optional) Falling suppression level, up to one decimal place. This value must be
equal to or less than the rising suppression value.
action {shutdown|trap}
The action taken when a storm occurs on a port. The default action is to filter traffic and to not
send an SNMP trap.
The keywords have these meanings:
•
shutdown: Disables the port during a storm
•
trap: Sends an SNMP trap when a storm occurs

Verify Storm Control Settings
Switch# show storm-control
Interface
Filter State Upper Lower Current
---------
-------------
----------
---------
--------
-Gi0/1
Forwarding
20 pps
10 pps
5 pps
Gi0/2
Forwarding
50.00%
40.00%
0.00%
<output omitted>

switchport mode trunk
switchport trunk native vlan vlan_number
switchport nonegotiate
.
Switch(config-if)#
Specifies an interface as a trunk link
Switch(config-if)#
Prevents the generation of DTP frames.
Switch(config-if)#
Set the native VLAN on the trunk to an unused VLAN
Controlling Trunking
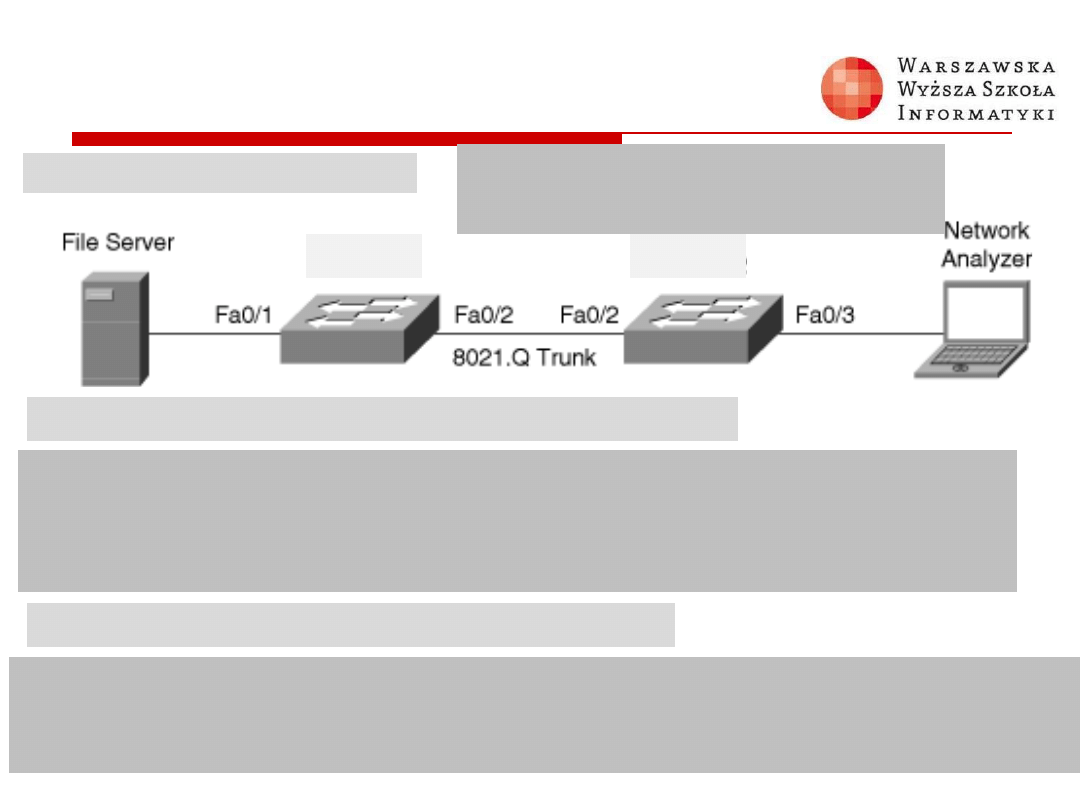
SPAN – CLI Commands
monitor session session_number source {interface
interface-id [, | -] [both | rx | tx]} | {vlan vlan-id [,
| -] [both | rx | tx]}| {remote vlan vlan-id}
monitor session session_number destination {interface
interface-id [, | -] [encapsulation replicate] [ingress
{dot1q vlan vlan-id | isl | untagged vlan vlan-id | vlan
vlan-id}]} | {remote vlan vlan-id}
Switch(config)#
Switch(config)#

Verify SPAN Configuration
Configuring RSPAN
2960-1
2960-2
2960-1(config)# vlan 100
2960-1(config-vlan)# remote-span
2960-1(config-vlan)# exit
2960-1(config)# monitor session 1 source interface FastEthernet 0/1
2960-1(config)# monitor session 1 destination remote vlan 100
reflector-port FastEthernet 0/24
2960-1(config)# interface FastEthernet 0/2
2960-1(config-if)# switchport mode trunk
2960-2(config)# monitor session 2 source remote vlan 100
2960-2(config)# monitor session 2 destination interface FastEthernet 0/3
2960-2(config)# interface FastEthernet 0/2
2960-2(config-if)# switchport mode trunk
1. Configure the RSPAN VLAN
2. Configure the RSPAN source ports and VLANs
3. Configure the RSPAN traffic to be forwarded
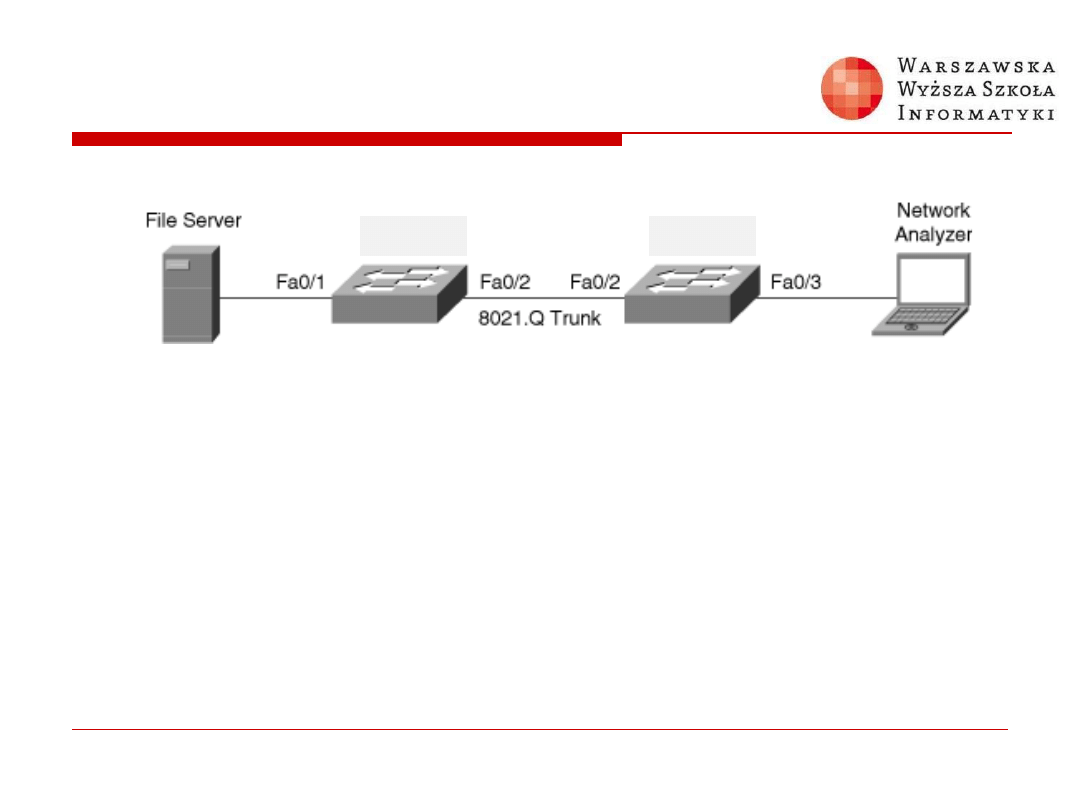
Verifying RSPAN Configuration
show monitor [session {session_number | all | local
| range list | remote} [detail]] [ | {begin | exclude
| include}expression]
2960-1
2960-2
Document Outline
- BST Laboratorium V
- Port Security – CLI Commands
- Switchport Port-Security Parameters
- Port Security Violation Configuration
- Switchport Port-Security Violation Parameters
- Port Security Aging Configuration
- Switchport Port-Security Aging Parameters
- Typical Configuration
- Verification – CLI Commands
- View Secure MAC Addresses
- Configure Portfast
- BPDU Guard
- Display the State of Spanning Tree
- Root Guard
- Verify Root Guard
- Storm Control Configuration
- Storm Control Parameters
- Verify Storm Control Settings
- Controlling Trunking
- SPAN – CLI Commands
- Verify SPAN Configuration
- Configuring RSPAN
- Verifying RSPAN Configuration
Wyszukiwarka
Podobne podstrony:
Ochrona teoria id 330276 Nieznany
Mierzenie teoria 2 id 299961 Nieznany
kudtba teoria id 253533 Nieznany
polimery teoria id 371571 Nieznany
filtracja teoria id 170991 Nieznany
ko o z doju teoria id 237555 Nieznany
cwiczenie I teoria id 125672 Nieznany
Mechanika Plynow Teoria id 2912 Nieznany
cwicz2 teoria id 124169 Nieznany
Akustyka teoria id 54512 Nieznany
NSP teoria id 324873 Nieznany
3 calki podwojne, teoria id 33 Nieznany (2)
Ochrona teoria(1) id 330277 Nieznany
cwiczenie 3 teoria id 125339 Nieznany
AMINOKWASY teoria id 59145 Nieznany
Kolo 1 teoria id 237085 Nieznany
KOLOS testy&teoria id 737100 Nieznany
mechanika egzamin teoria id 290 Nieznany
więcej podobnych podstron